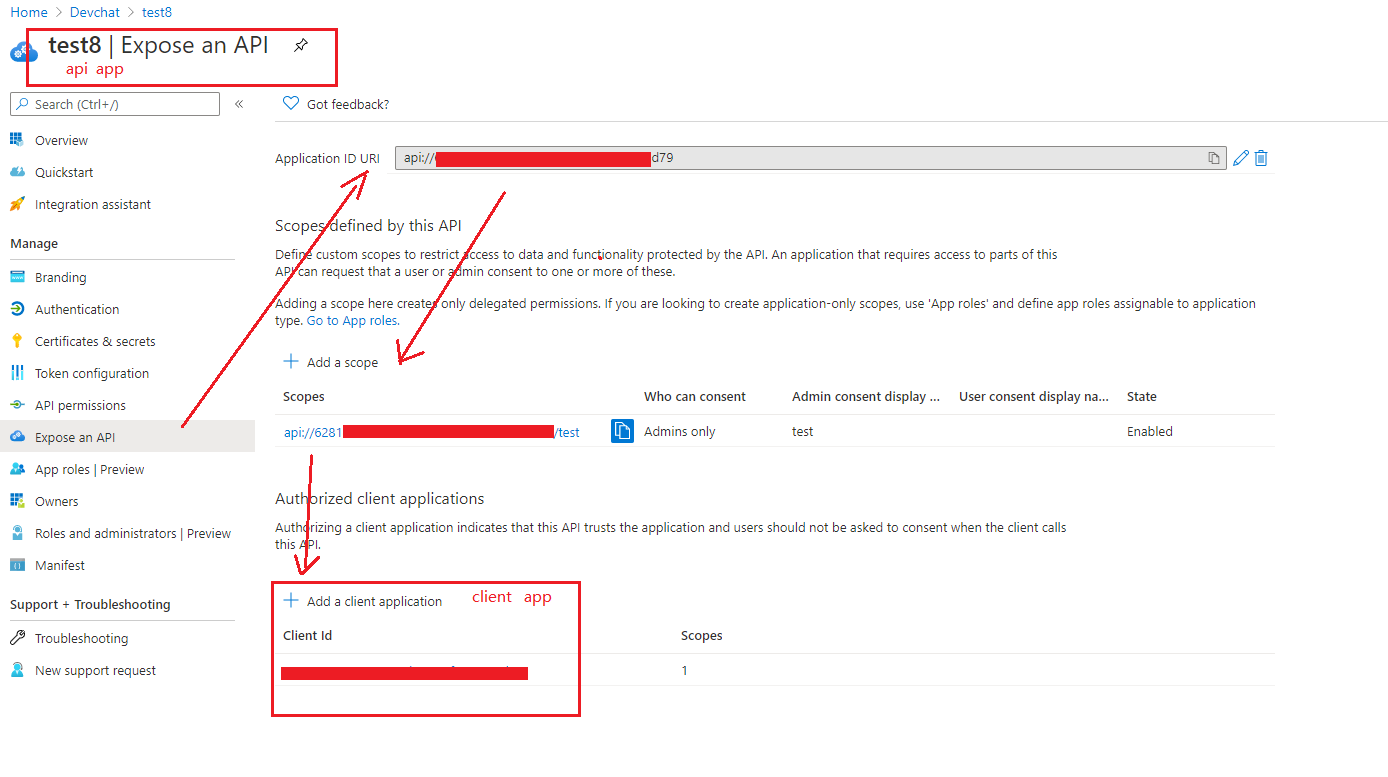
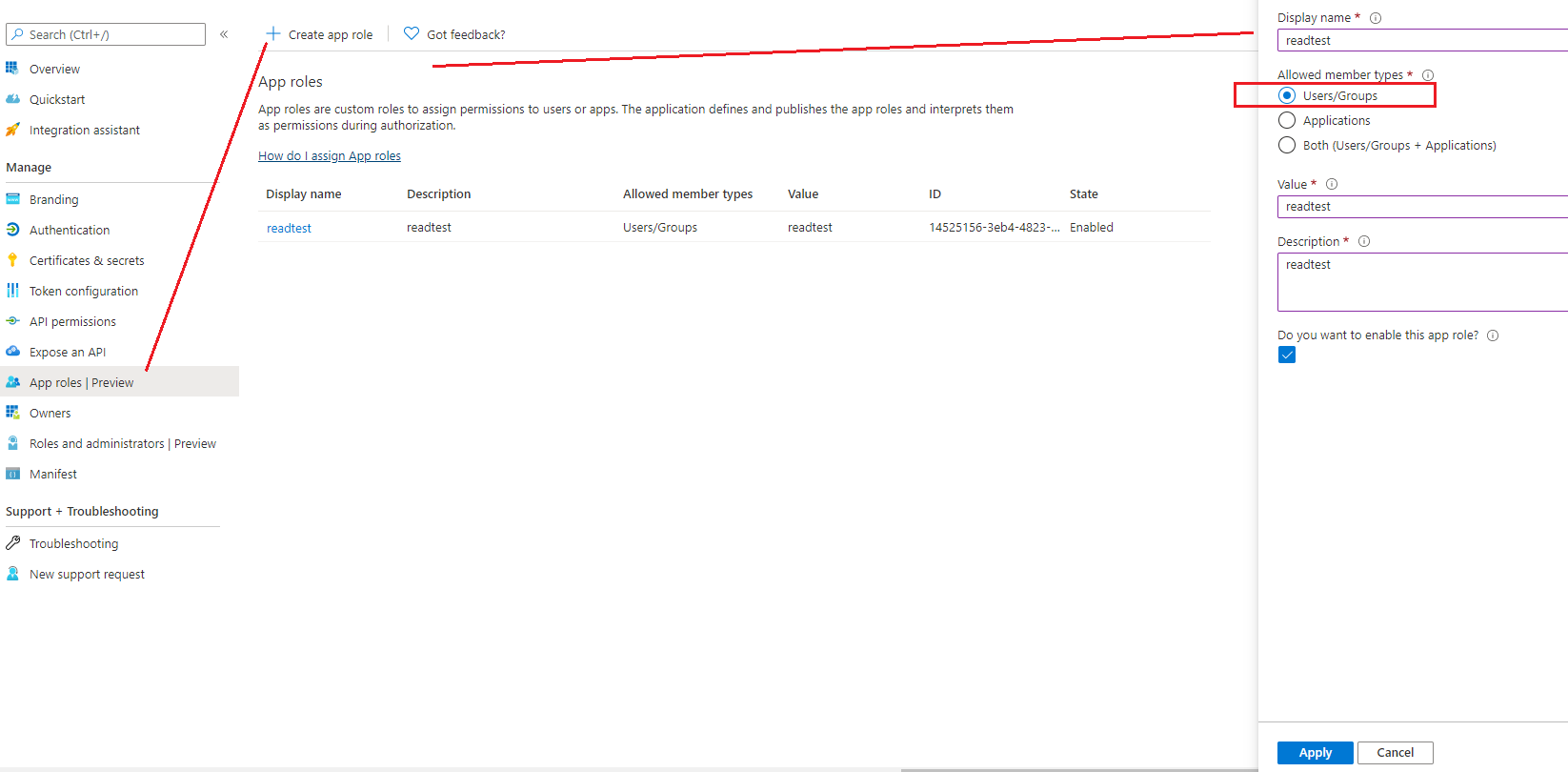
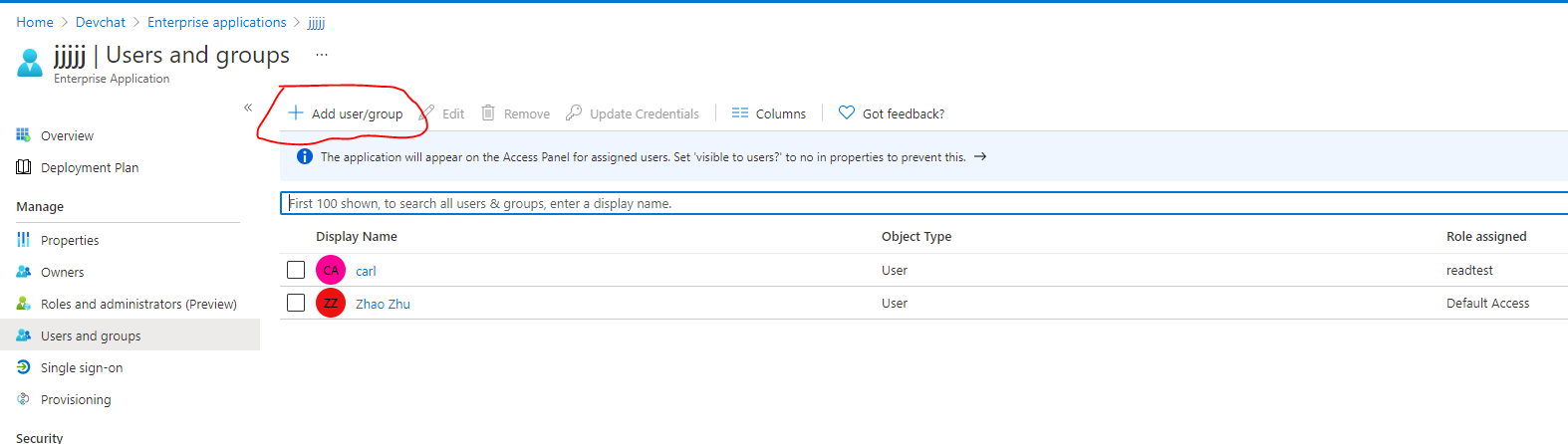
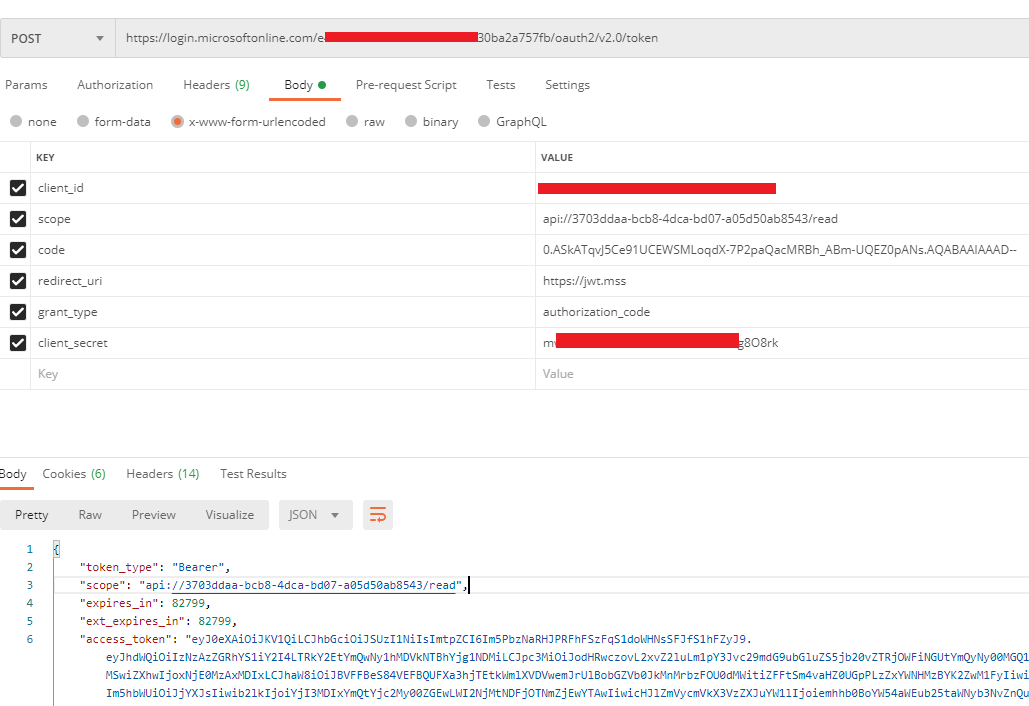
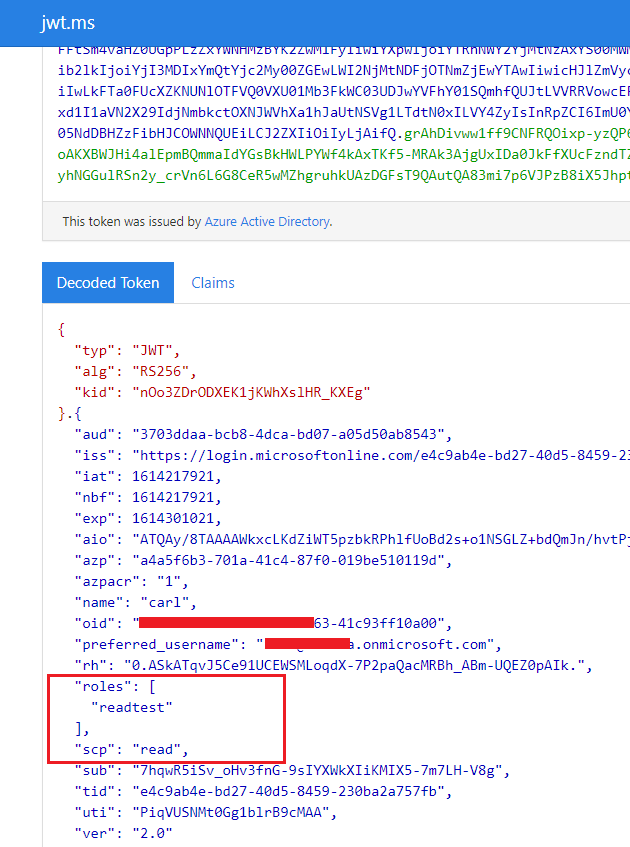
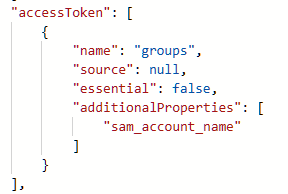
I'm using https://login.microsoftonline.com/.../oauth2/v2.0/token to authenticate (authorization_code grant) to azure Ad using the scopes: offline_access, openid, profile, User.Read
According to the documentation the Access Token I receive should contain the roles of the user: https://learn.microsoft.com/en-us/azure/active-directory/develop/access-tokens
However only the identity token returns the roles:
--Access Token
{
"typ": "JWT",
"nonce": "IWTwK2P0vzHoNnv1vvvSsjZSbAYPpSIk8MozY0A4WR0",
"alg": "RS256",
"x5t": "nOo3ZDrODXEK1jKWhXslHR_KXEg",
"kid": "nOo3ZDrODXEK1jKWhXslHR_KXEg"
}.{
...
"rh": "0.ASgASPp-HouAsUyXCdG05vvfeHAoPPG46TFOoWYsil-LDcsoADw.",
"scp": "User.Read profile openid email",
...
}.[Signature]
--Identity Token
{
"typ": "JWT",
"alg": "RS256",
"kid": "nOo3ZDrODXEK1jKWhXslHR_KXEg"
}.{
...
"rh": "0.ASgASPp-HouAsUyXCdG05vvfeHAoPPG46TFOoWYsil-LDcsoADw.",
"roles": [
"MyApp.Read",
"MyApp.Admin",
"MyApp.Write",
],
...
}.[Signature]
Is there a way to make the access token also include the roles?