For my application, I want users to be able to sign in with their Azure Account (Single Sign On). I also need an access token to access the secured backend.
So I can get both, the id_token and the access_token, with a request to this url:
https://login.microsoftonline.com/MY_TENANT_ID/oauth2/authorize?response_type=id_token+token&client_id=MY_CLIENT_ID&state=SOME_STATE&redirect_uri=MY_REDIRECT_URI&scope=openid profile&resource=MY_CLIENT_ID&nonce=SOME_NONCE
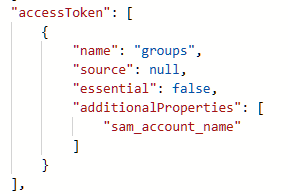
This basically works, but I also want to have the roles in the access token (and in the id token), but the roles are not included in the tokens I receive.
When I use this Url to only get an id_token, the role claims are included:
https://login.microsoftonline.com/MY_TENANT_ID/oauth2/authorize?response_type=id_token&client_id=MY_CLIENT_ID&state=SOME_STATE&redirect_uri=MY_REDIRECT_URI&scope=openid profile&nonce=SOME_NONCE
The difference is I request only the id_token and not the token and I leave out the resource parameter.
My questions are: Why are the role claims not included in the tokens of the first request? What are my options to get id_token and the access_token with the roles claims?
edit: This is how the approles are defined in the app's manifest:
{
"appId": "MY_CLIENT_ID",
"appRoles": [
{
"allowedMemberTypes": [
"User"
],
"displayName": "Admin",
"id": "c200e304-fff3-49f1-a4df-e406741ea690",
"isEnabled": true,
"description": "Bla bla",
"value": "admin"
},
{
"allowedMemberTypes": [
"User"
],
"displayName": "Reader",
"id": "c534f351-b343-48d0-9dd7-ecb4c5cb402d",
"isEnabled": true,
"description": "Bla bla",
"value": "reader"
}
],
"availableToOtherTenants": false,
...
}

tokenparameter used actually. Have you tried to do the same thing with authorization code grant flow? I.e.response_type=id_token+code, and then exchanging the code for an access token. – Spectacledresponse_type=id_token+code. With the code I grabbed the tokens from the token endpoint which gave me the access_token, refresh_token and id_token. Bothaccess_tokenandid_tokenare lacking the role claims again. :( – Fleisig