We are unable to connect to an HTTPS server using WebRequest because of this error message:
The request was aborted: Could not create SSL/TLS secure channel.
We know that the server doesn't have a valid HTTPS certificate with the path used, but to bypass this issue, we use the following code that we've taken from another StackOverflow post:
private void Somewhere() {
ServicePointManager.ServerCertificateValidationCallback += new RemoteCertificateValidationCallback(AlwaysGoodCertificate);
}
private static bool AlwaysGoodCertificate(object sender, X509Certificate certificate, X509Chain chain, SslPolicyErrors policyErrors) {
return true;
}
The problem is that server never validates the certificate and fails with the above error. Does anyone have any idea of what I should do?
I should mention that a colleague and I performed tests a few weeks ago and it was working fine with something similar to what I wrote above. The only "major difference" we've found is that I'm using Windows 7 and he was using Windows XP. Does that change something?


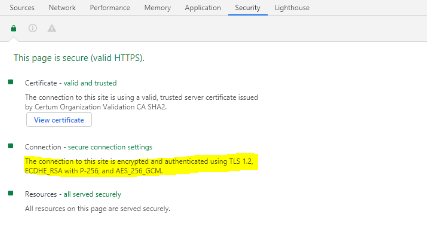
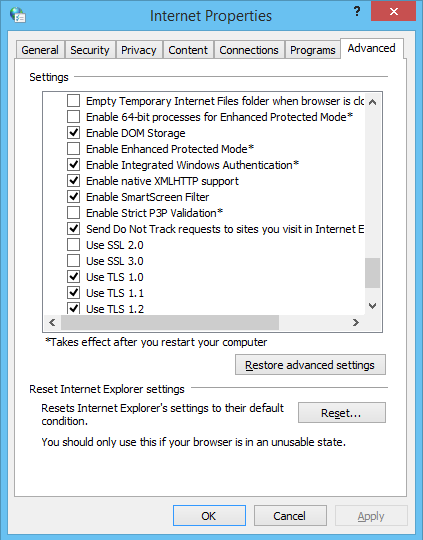

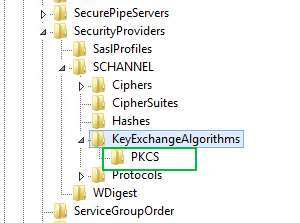
The request was aborted: Could not create SSL/TLS secure channelis a very generic one. It basically says, "the SSL/TLS/HTTPS connection initialization failed for one of many possible reasons". So if you get it regularly in a specific situation, your best option is to ask a specific question giving specific details about that situation. And checking the Event Viewer for more information. And/or enable some .NET client-side debugging to get more details (is the server cert not trusted? is there a cipher mismatch? SSL/TLS protocol version mismatch? etc). – Bribe