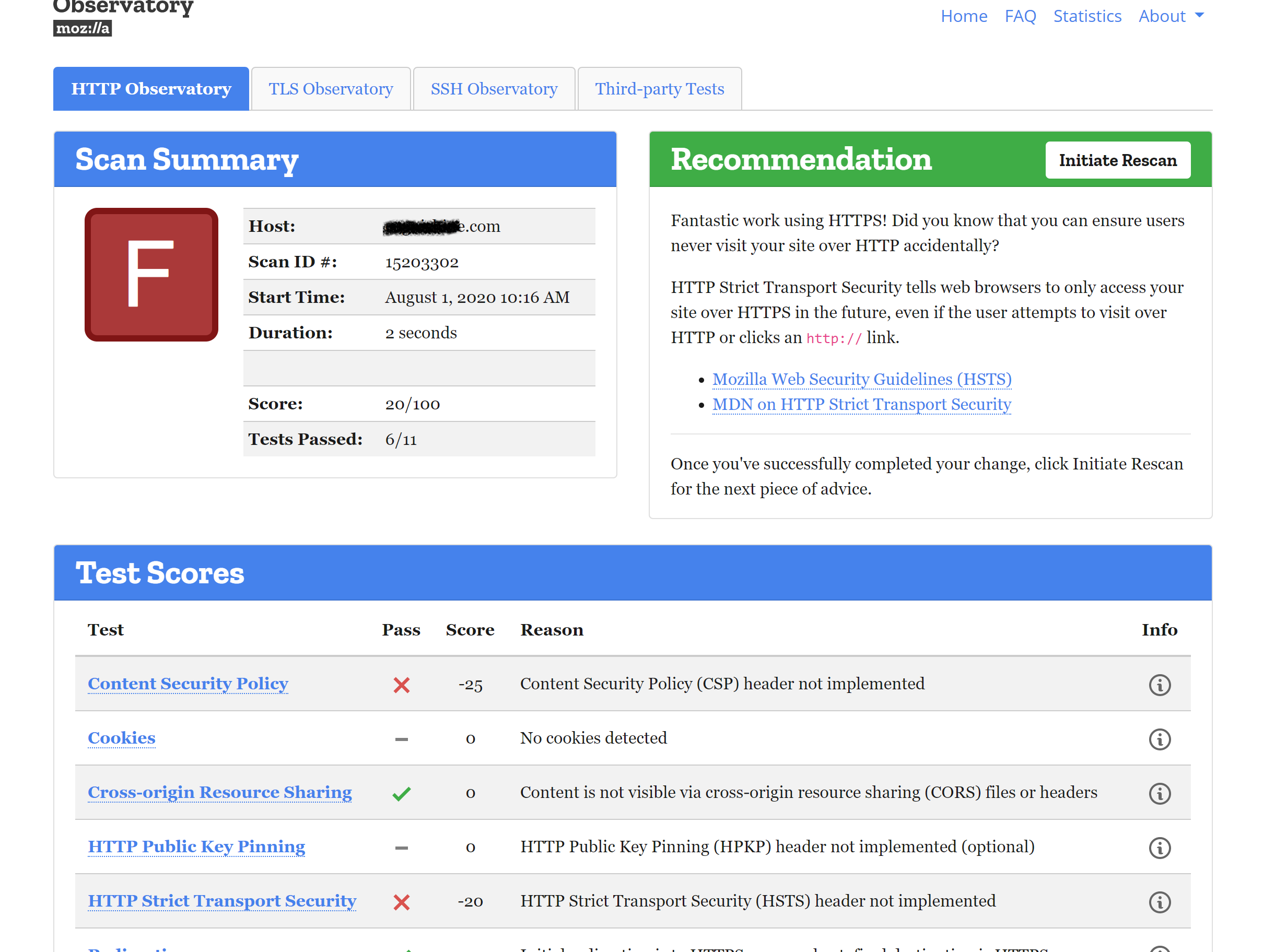
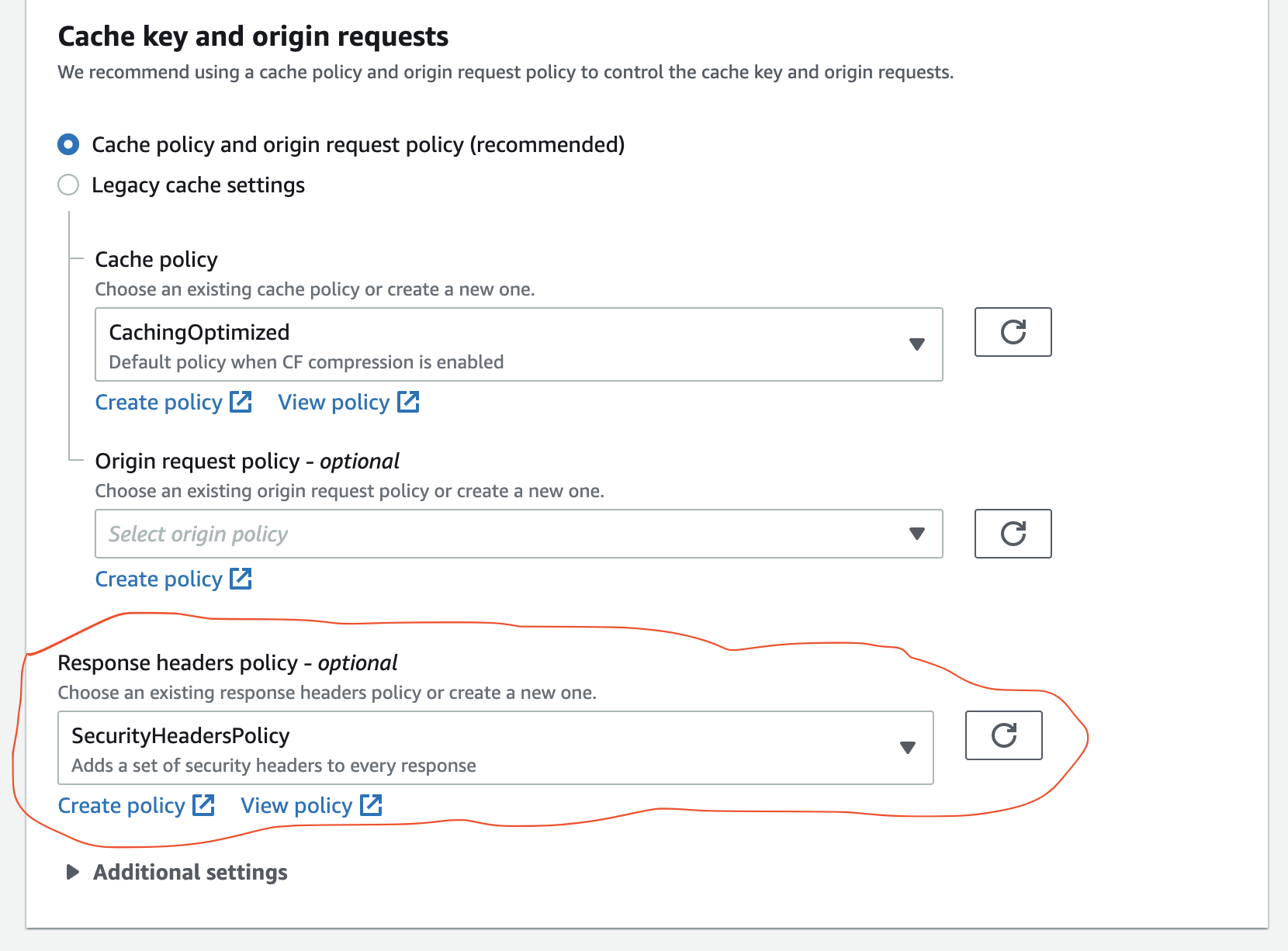
I would recommend using Lambda@Edge to append any headers that you're looking for to your origin response before it is returned to the viewer.
It can be done as simply as the below example when added as a Origin Response event.
import json
def lambda_handler(event, context):
response = event["Records"][0]["cf"]["response"]
headers = response["headers"]
headers['strict-transport-security'] = [{key: 'Strict-Transport-Security', value: 'max-age=63072000; includeSubdomains; preload'}];
headers['content-security-policy'] = [{key: 'Content-Security-Policy', value: "default-src 'none'; img-src 'self'; script-src 'self'; style-src 'self'; object-src 'none'"}];
headers['x-content-type-options'] = [{key: 'X-Content-Type-Options', value: 'nosniff'}];
headers['x-frame-options'] = [{key: 'X-Frame-Options', value: 'DENY'}];
headers['x-xss-protection'] = [{key: 'X-XSS-Protection', value: '1; mode=block'}];
headers['referrer-policy'] = [{key: 'Referrer-Policy', value: 'same-origin'}];
response['headers'] = headers
return response
For more information take a look at the Adding HTTP Security Headers Using Lambda@Edge and Amazon CloudFront blog post.