Earlier Elastic Beanstalk used to create a default EC2 instance profile named aws-elasticbeanstalk-ec2-role the first time an AWS account create an environment. This instance profile included default managed policies. However, recent AWS security guidelines don’t allow an AWS service to automatically create roles with trust policies to other AWS services, EC2 in this case. Because of these security guidelines, Elastic Beanstalk no longer creates a default aws-elasticbeanstalk-ec2-role instance profile.
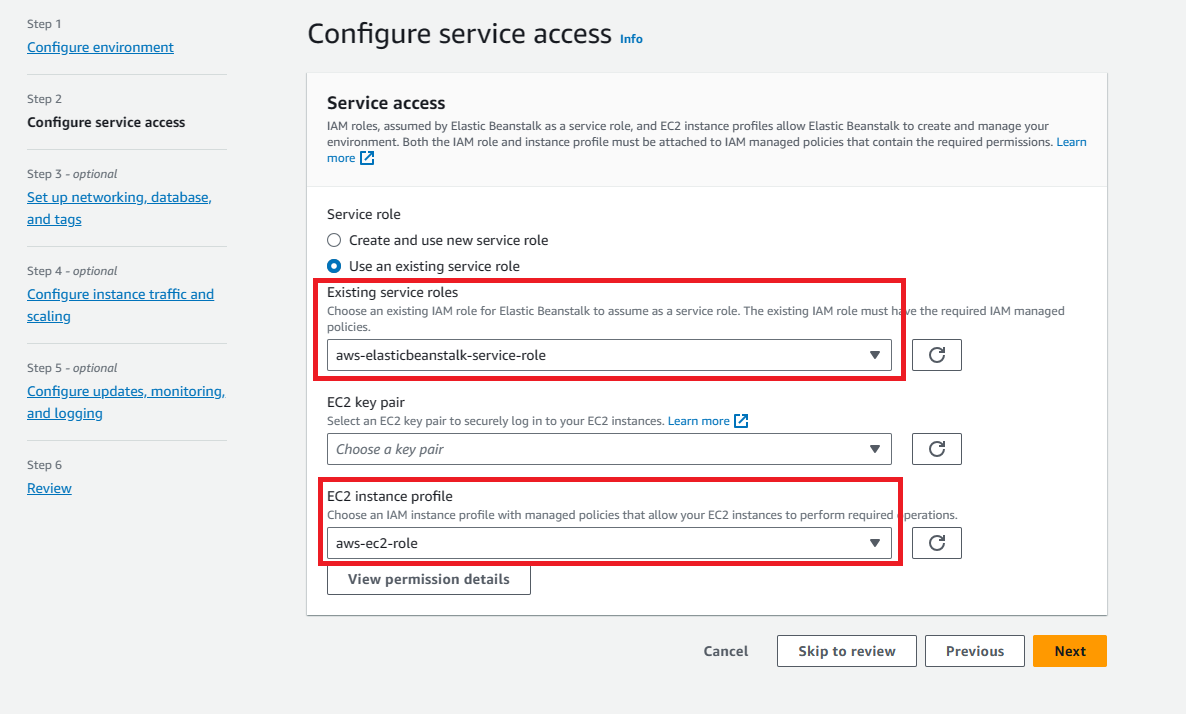
So if your AWS account doesn’t have an EC2 instance profile, you must create one using the IAM service. You can then assign the EC2 instance profile to the new environments that you create.
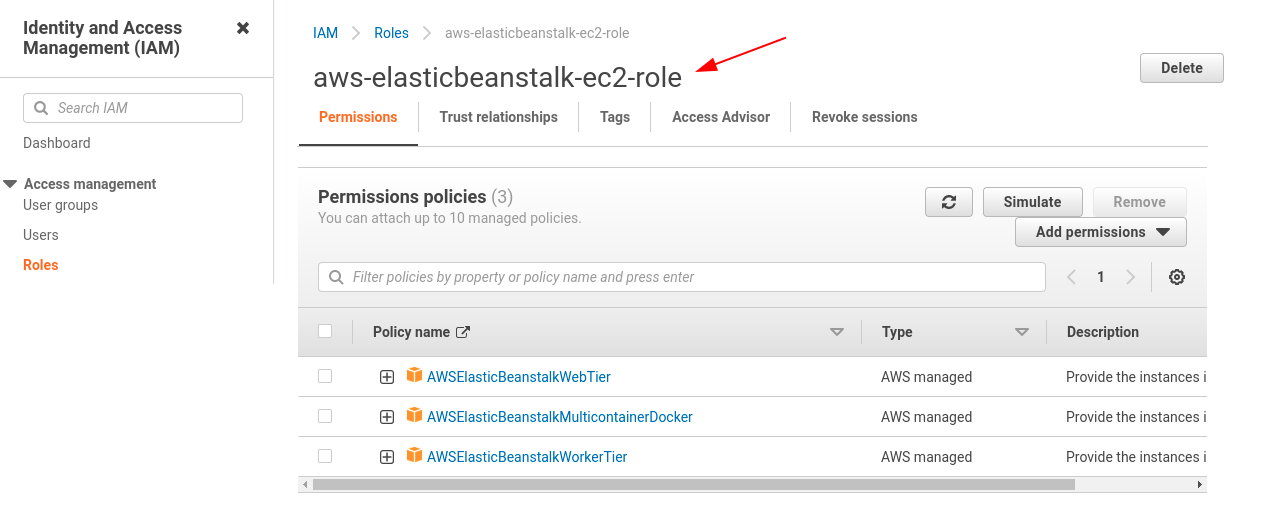
Open IAM Console → In the navigation pane of the console, choose Roles and then create role → Under Trusted entity type, choose AWS service → Under Use case, choose EC2 → Choose Next → Attach- AWSElasticBeanstalkWebTier, AWSElasticBeanstalkWorkerTier, AWSElasticBeanstalkMulticontainerDocker → Choose Next → Enter a name for the role - aws-elasticbeanstalk-ec2-role → Choose Create role.
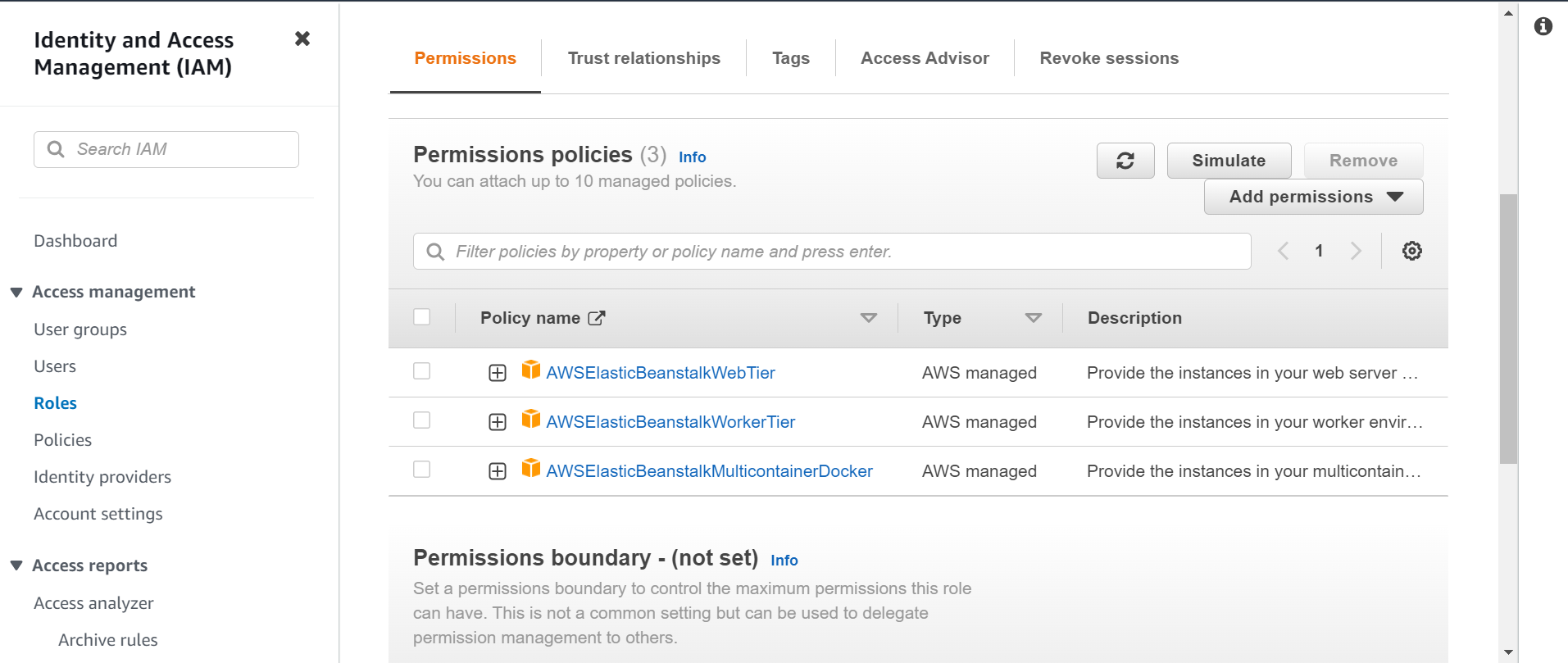
If you already have an instance profile, make sure you have below-required policies. To meet the default use cases for an environment, these policies must be attached to the role for the EC2 instance profile:-
Role name: aws-elasticbeanstalk-ec2-role
Permission policies attached:-
AWSElasticBeanstalkWebTierAWSElasticBeanstalkWorkerTierAWSElasticBeanstalkMulticontainerDocker
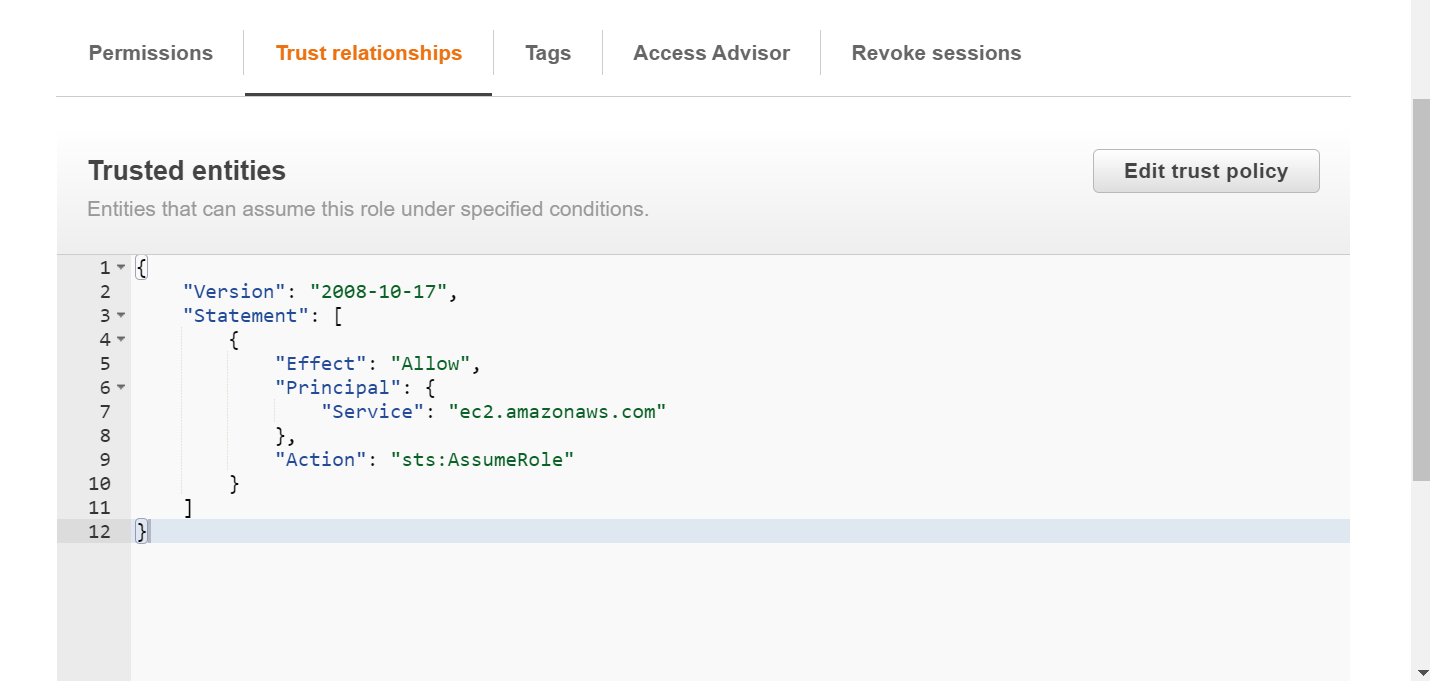
Trust relationship policy for EC2:-
{
"Version": "2008-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
![enter image description here]()
![enter image description here]()
Hope this helps.