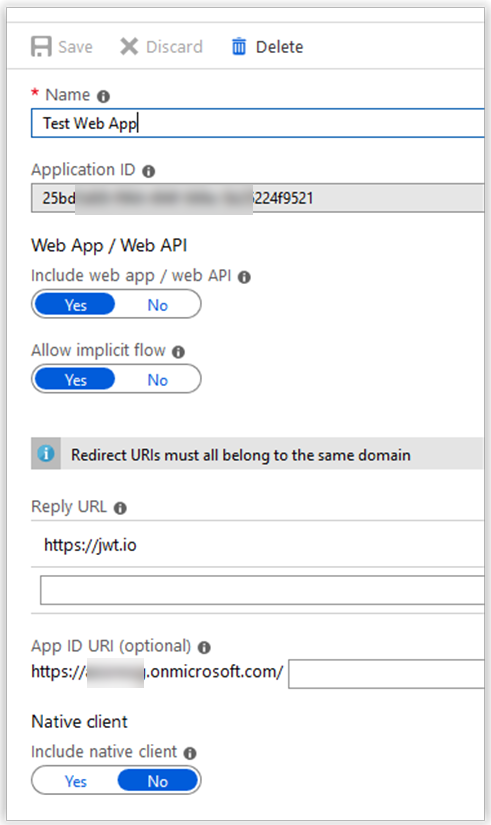
Our team is building an Angular app that is gonna use B2C for authentication/authorization purposes and in this app we would like to build the OpenID integration using the authorization code flow with PKCE.
Azure B2C seems to support PKCE however for some reason it also requires that we send the client_secret when requesting the access token. Is this correct? Shouldn't PKCE eliminate the need of a static client secret when dealing with the authorization code flow?