I have a docker 1.12 running on CentOS. I am trying to add insecure registry to it and things mentioned in documentation just don't work. The system uses systemd so I created a /etc/systemd/system/docker.service.d/50-insecure-registry.conf file.
$ cat /etc/systemd/system/docker.service.d/50-insecure-registry.conf
[Service]
Environment='DOCKER_OPTS=--insecure-registry="hostname.cloudapp.net:5000"'
After loading daemon and restarting docker service, systemd shows that the environment variable is there
$ sudo systemctl show docker | grep Env
Environment=DOCKER_OPTS=--insecure-registry="hostname.cloudapp.net:5000"
But when I run docker info I don't see that insecure registry added
$ docker info
........
Registry: https://index.docker.io/v1/
WARNING: bridge-nf-call-iptables is disabled
WARNING: bridge-nf-call-ip6tables is disabled
Insecure Registries:
127.0.0.0/8
Pushing images to hostname.cloudapp.net fails with
Pushing application (hostname.cloudapp.net:5000/application:latest)...
The push refers to a repository [hostname.cloudapp.net:5000/mozart_application]
ERROR: Get https://hostname.cloudapp.net:5000/v1/_ping: http: server gave HTTP response to HTTPS client
Is there something that could be done ? Am I missing something ?
UPDATE
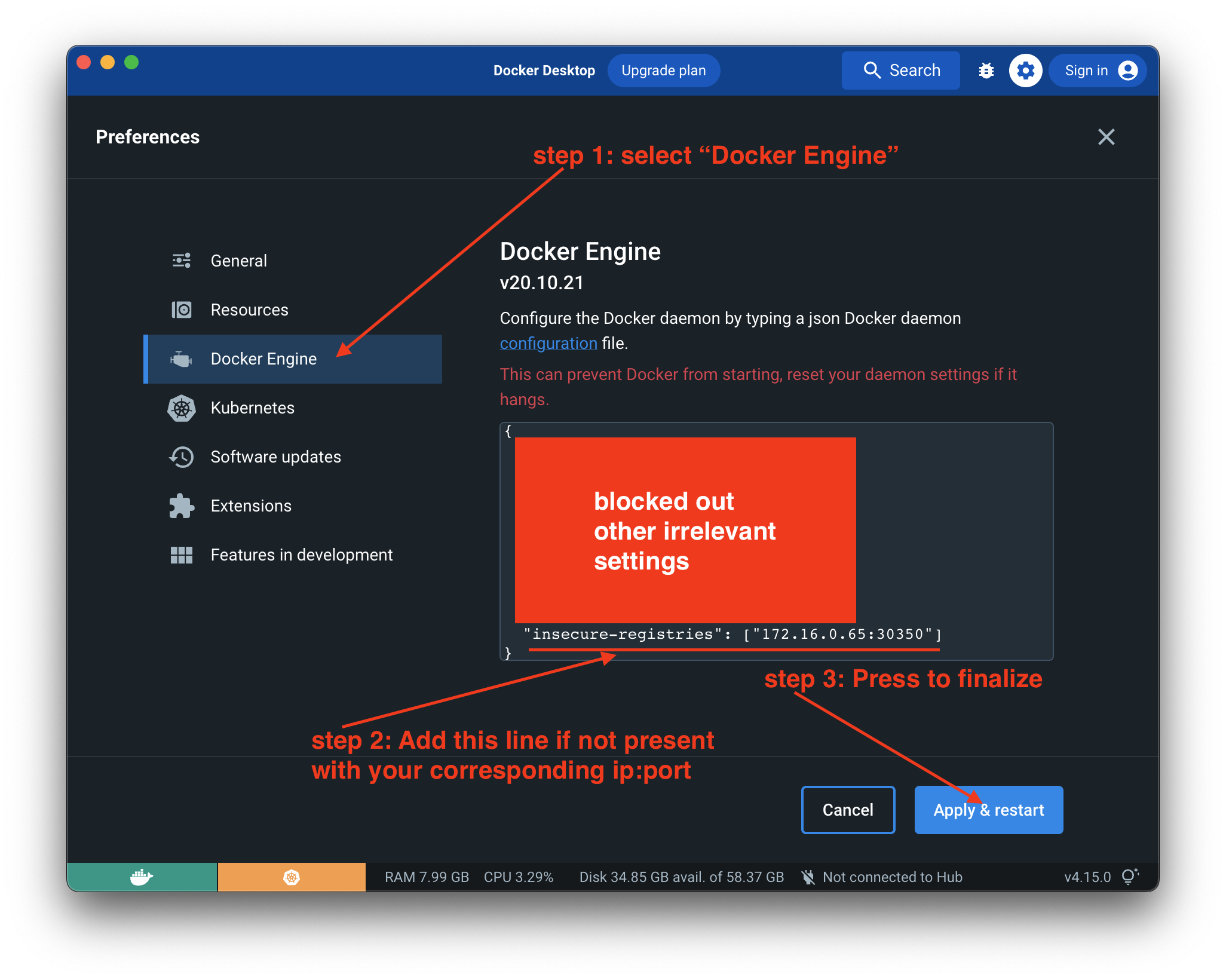
Resolved the issue by adding a file /etc/docker/daemon.json with following content
{
"insecure-registries" : [ "hostname.cloudapp.net:5000" ]
}
And then restart docker
sudo systemctl daemon-reload
sudo systemctl restart docker
After that insecure registry hostname.cloudapp.net:5000 works.

hostanemeis likely a typo. – Prole