I had installed a c++ compiler for windows with MinGW. I tried to make a simple program:
#include <iostream>
using namespace std;
int main() {
cout << "Hello World!";
return 0;
}
And saved it as try.cc. Afterwards I opened cmd in the folder and ran g++ try.cc -o some.exe. It generated some.exe but my antivirus (avast) recognized it as malware. I thought it could be a false positive, but it specifically said it's a trojan.
I removed the file from the virus chest and uploaded it to "https://www.virustotal.com/"
The result:
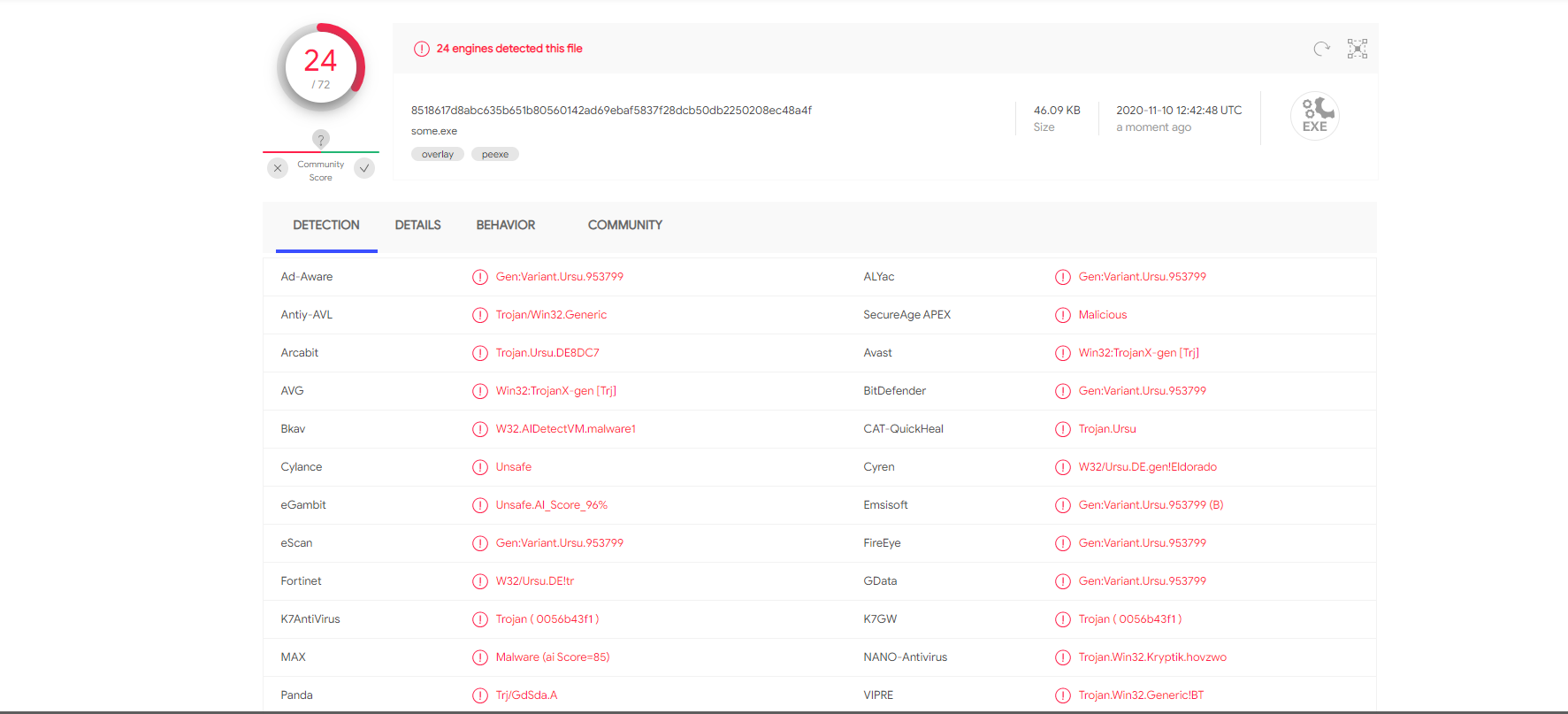
24 out of 72 engines detected it as malware and a lot of them as a trojan.
Is this a false positive? Why would it get detected as a trojan? If it is, how do I avoid getting this warning every time I make a new program?
Edit:
Thanks all for the help, I ran a full scan of my computer, with 2 antivirus and everything seemed clean. I also did a scan on the MinGW folder and nothing.
The problem keeps appearing each time I make a new c++ program. I tried modifying the code and the name but the AV kept detecting it as a virus. Funny thing is that changing the code changed the type of virus the av reported.
I'm still not 100% sure that the compiler is clean so I dont know if I should ignore it and run the programs anyway. I downloaded MinGW from "https://osdn.net/projects/mingw/releases/"
If anyone knows how to be completely sure that the executables created are not viruses, only false positives I would be glad they share it.
Edit 2:
It occurred to me that if the compiler is infected and it's adding code, then I might be able to see it with a decompiler/disassembler, feeding it the executable. I downloaded a c++ decompiler I found here "snowman" and used it on the file. The problem is that the code went from 7 lines in the original executable to 5265 and is a bit hard to make sense of it. If someone has some experience with reverse engineering, a link to the original file is in the comments below.

exejust happens to share the same fingerprint as some trojans. See ifg++ -O3 -g0 try.cc -o some.exemakes a difference. – Gladisgladney