I have a peculiar problem where a c# app works on all other machines and other client machines I have tested. But does not establish a connection on my clients Windows Server 2012 hosted by his ISP. This app have been working up to about 2 days ago on this machine according to my client and uses .Net4.5.2. I have no idea what changed the last couple of days unfortunately.
What I have tested on this machine:
- Using Chrome the url works
- Using Edge the url works
- hitting the URL with curl works
- Using IE11 the url does not work
- Using our app does not work
- Using a quick test app does not work
This is the same no matter what settings I change on the server or in the app.
Error from my app:
AuthResponse is null: False
AuthResponse ErrorException: System.Net.WebException: The request was aborted: Could not create SSL/TLS secure channel.
at System.Net.HttpWebRequest.GetRequestStream(TransportContext& context)
at System.Net.HttpWebRequest.GetRequestStream()
at RestSharp.Http.WriteRequestBody(HttpWebRequest webRequest)
at RestSharp.Http.PostPutInternal(String method)
at RestSharp.Http.AsPost(String httpMethod)
at RestSharp.RestClient.DoExecuteAsPost(IHttp http, String method)
at RestSharp.RestClient.Execute(IRestRequest request, String httpMethod, Func`3 getResponse)
AuthResponse ErrorMessage: The request was aborted: Could not create SSL/TLS secure channel.
Error from IE11:
Turn on TLS 1.0, TLS 1.1, and TLS 1.2 in Advanced settings and try connecting to again. If this error persists, it is possible that this site uses an unsupported protocol or cipher suite such as RC4 (link for the details), which is not considered secure. Please contact your site administrator.
Errors From Event Viewer:
A fatal alert was received from the remote endpoint. The TLS protocol defined fatal alert code is 40.
A fatal alert was generated and sent to the remote endpoint. This may result in termination of the connection. The TLS protocol defined fatal error code is 40. The Windows SChannel error state is 1205.
A fatal error occurred while creating an SSL client credential. The internal error state is 10013.
There are a lot of these errors in event viewer, I just copied three of them in case they are actually relevant.
What I have tried:
I used IISCrypto to change and configure all manner of settings and testing in between. All with the same results. I have modified my app with quite a few changes I have found by searching all with the same results as well. Some of the code changes I made below:
System.Net.ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls | SecurityProtocolType.Tls11 | SecurityProtocolType.Tls12;
ServicePointManager.Expect100Continue = true;
System.Net.ServicePointManager.ServerCertificateValidationCallback += (sender, cert, chain, sslPolicyErrors) => true;
This is not all the changes I tried. I tried all kinds of different variations as well such as only tls1.2. I have used my little test app as well to connect to other https sites like google and my other rest service and no error is reported on this machine.
Our Auth server uses Lets Encrypts certificates and uses OAth and only accepts tls2.1. I have hit another REST Api that we use that also use Lets Encrypt and that is working. I don't know if I need to update the certificate store (if that is possible), or if there is a setting I'm missing. I'm honestly at a loss here.
Test app source if that helps at all:
static async Task test(string url)
{
// Call asynchronous network methods in a try/catch block to handle exceptions.
try
{
HttpClient httpClient = new HttpClient();
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12;
ServicePointManager.ServerCertificateValidationCallback += (sender, cert, chain, sslPolicyErrors) => true;
var result = await httpClient.GetAsync(url);
MessageBox.Show(result.StatusCode.ToString());
}
catch (HttpRequestException e)
{
MessageBox.Show(e.ToString());
}
}

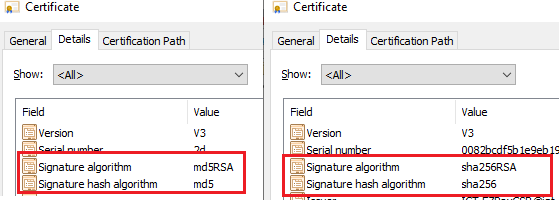
IIS Cryptoshould give you the information. You can try to install .Net Framework 4.8 (which brings in TLS1.3). – Democracy