I just signed up for Amazon's new Elastic Beanstalk offering. What I can't figure out is how to SSH to a Beanstalk instance. I don't have a private key because Beanstalk generated the instance on my behalf.
I found it to be a 2-step process. This assumes that you've already set up a keypair to access EC2 instances in the relevant region.
Configure Security Group
In the AWS console, open the EC2 tab.
Select the relevant region and click on Security Group.
You should have an
elasticbeanstalk-defaultsecurity group if you have launched an Elastic Beanstalk instance in that region.Edit the security group to add a rule for SSH access. The below will lock it down to only allow ingress from a specific IP address.
SSH | tcp | 22 | 22 | 192.168.1.1/32
Configure the environment of your Elastic Beanstalk Application
- If you haven't made a key pair yet, make one by clicking Key Pairs below Security Group in the ec2 tab.
- In the AWS console, open the Elastic Beanstalk tab.
- Select the relevant region.
- Select relevant Environment
- Select Configurations in left pane.
- Select Security.
- Under "EC2 key pair:", select the name of your keypair in the
Existing Key Pairfield.
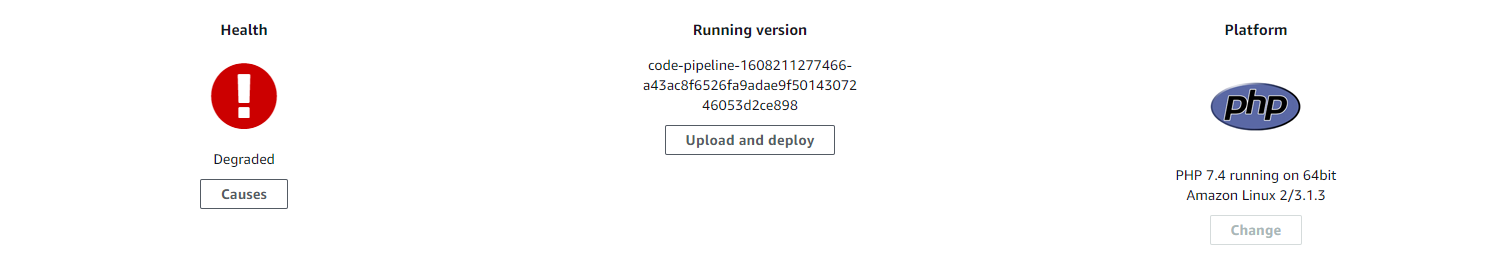
If after these steps you see that the Health is set Degraded
that's normal and it just means that the EC2 instance is being updated. Just wait on a few seconds it'll be Ok again
Once the instance has relaunched, you need to get the host name from the AWS Console EC2 instances tab, or via the API. You should then be able to ssh onto the server.
$ ssh -i path/to/keypair.pub [email protected]
Note: For adding a keypair to the environment configuration, the instances' termination protection must be off as Beanstalk would try to terminate the current instances and start new instances with the KeyPair.
Note: If something is not working, check the "Events" tab in the Beanstalk application / environments and find out what went wrong.
Elastic beanstalk CLI v3 now supports direct SSH with the command eb ssh. E.g.
eb ssh your-environment-name
No need for all the hassle of setting up security groups of finding out the EC2 instance address.
There's also this cool trick:
eb ssh --force
That'll temporarily force port 22 open to 0.0.0.0, and keep it open until you exit. This blends a bit of the benefits of the top answer, without the hassle. You can temporarily grant someone other than you access for debugging and whatnot. Of course you'll still need to upload their public key to the host for them to have access. Once you do that (and as long as you're inside eb ssh), the other person can
ssh [email protected]
eb ssh production. You can also set up a specific environment with the setup option: eb ssh production --setup –
Bombshell My experience in August 2013 with a linux client and a simple AWS Beanstalk installation (single EC2 instance) is as follows (based on Community Wiki above)
Configure Security Group
- In the AWS console, select EC2 to go to the EC2 Dashboard
- Discover the security group to which your EC2 instance belongs by clicking Instances in the left hand panel and then selecting the instance you want to connect to (in my case there is only one - called Default Environment). The details are shown at the base of the page - You should see a field for Security Groups - make a note of the name - in my case "awsweb...".
- From the left hand panel select Security Groups.
- Select the
awsweb...security group and the details should show at the base of the page - Select the Inbound tab and choose SSH from the "Create a New Rule" drop down. Insert the ip address/CIDR of your local machine (from which you intend to connect), e.g. 192.168.0.12/32 and click Add Rule and Apply Rule Changes.
Create Public-Private Key Pair
- From the EC2 dashboard select Key Pairs from the left hand panel
- Click Key Pair (at top) and enter a name such as myname-key-pair-myregion or whatever valid key name you like.
- Confirm and then accept the download of the private key from the browser saving it for instance to your home directory or wherever you fancy. Make sure the directory only has write permissions for you.
Associate the Public Private Key Pair with the Elastic Beanstalk EC2 Server
- To add a public-private key pair to an Elastic Beanstalk EC2 instance do: Services -> Elastic Beanstalk -> My App -> Default Environment takes you to the default environment (the one where you upload your app)
- Click Configuration (on left hand panel) and then on the gear/cog associated with "Instances"
- A page entitled "Server" is displayed
- Select your prebuilt key par from EC2 Key Pair and do Save
- Some warning message is displayed so do Save again.
Connect to AWS EC2 Instance using SSH
- In a terminal session change to the directory containing your private key (.pem file).
- If you've had a few goes at this you should probably do something about .ssh/known_hosts if you have one such as renaming it. Otherwise you may get an error about the host's identity having changed.
- Do: ssh -i ./myname-key-pair-my-region.pem [email protected]
Good luck
I have been playing with this as well.
- goto your elastic beanstalk service tab
- on your application overview goto action --> edit configuration
- add the name of a key as it appears in your EC2 tab (for the same region) to the existing keypair box and hit apply changes
The service will be relaunched so make a coffee for 5 mins
On your ec2 tab for the same region you'll see your new running instance. ssh to the public dns name as ec2-user using the key added in 3 e.g. ssh [email protected]
There is a handy 'Connect' option in the 'Instance Actions' menu for the EC2 instance. It will give you the exact SSH command to execute with the correct url for the instance. Jabley's overall instructions are correct.
Above answers are bit old.
Firstly create a key-pair and then attach it to Elastic Beanstalk environment.
Steps to create a key-pair
- Login to AWS
- Services -> EC2
- In left under NETWORK & SECURITY select key pairs
- Select Create new Key Pair, type key name and click on create. The key will be automatically downloaded to your system.
Steps to attach created key pair to Elastic Beanstalk environment
AWS -> Services -> Elastic Beanstalk
Select your environment and click on the configuration in left.
In Configuration overview select modify from Security.
Under Virtual machine permissions select key-pair that we created.
Click on save and then on save configuration.
This will take some time to reflect to your EC2 instance.
Amazon has released a better way to SSH into instances via SSM (Simple Systems Manager). The Session Manager tool within SSM lets you SSH using just AWS API keys. It's better than regular SSH because:
- It doesn't require opening port 22.
- It keeps a logs of SSH sessions.
- It doesn't require shared SSH keys. Credentials are tied to IAM users like they should be.
- It works with instances that have no public IP address and are in private subnets.
Set up your Elastic Beanstalk Environment to allow SSH via AWS SSM
The following steps need to be done once per environment.
Go to Elastic Beanstalk > ENVIRONEMNT_NAME > Configuration > Security and find the "IAM instance profile" (by default, this is "aws-elasticbeanstalk-ec2-role"). This is ROLE_NAME in step 2.
Go to IAM > Roles > ROLE_NAME. Under permissions, add "AmazonSSMManagedInstanceCore".
Go to Systems Manager > Session Manager > Preferences > Edit. Enable "Run As Support" and set the "Run As Defualt User" to be "ec2-user" (or whatever the default user for your Elastic Beanstalk servers is).
Note that it may take some time (~10 minutes) for the IAM changes to propagate. If you have completed the AWS setup and get a "TargetNotConnected" error, wait 10-15 minutes and try again.
SSH with AWS SSM
Having set this up, you now have three options for how to SSH into your instance:
Through the AWS web console. Go to AWS Systems Manager > Session Manager > Start Session. Pick the machine you want to SSH into. This will start an SSH terminal in your browser.
Use the AWS CLI. See the instructions for "AWS CLI Setup" below.
Use eb-ssm. eb-ssm is a command line tool that is a drop-in replacement for the EB CLI command
eb ssh. It does this by wrapping the AWS CLI and piggybacking on your EB CLI config. Note that eb-ssm also requires the "AWS CLI Setup" steps below
AWS CLI Setup
If you want to SSH from your terminal using either the AWS CLI or eb-ssm, do the following steps. These steps need to be done once per computer.
Install the AWS CLI: https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-files.html
Install the Session Manager Plugin: https://docs.aws.amazon.com/systems-manager/latest/userguide/session-manager-working-with-install-plugin.html
Disclaimer: I am the primary author of eb-ssm.
If you are using elastic bean and EB CLI, just use eb ssh to login to instance. You can use options as specified in the following link
http://docs.aws.amazon.com/elasticbeanstalk/latest/dg/eb3-ssh.html
On mac you can install the cli using brew:
brew install awsebcli
With the command line tool you can then ssh with:
eb ssh environment-name
and also do other operations. This assumes you have added a security group that allows ssh from your ip.
You need to connect to the ec2 instance directly using its public ip address. You can not connect using the elasticbeanstalk url.
You can find the instance ip address by looking it up in the ec2 console.
You also need to make sure port 22 is open. By default the EB CLI closes port 22 after a ssh connection is complete. You can call eb ssh -o to keep the port open after the ssh session is complete.
Warning: You should know that elastic beanstalk could replace your instance at anytime. State is not guaranteed on any of your elastic beanstalk instances. Its probably better to use ssh for testing and debugging purposes only, as anything you modify can go away at any time.
The direction to set the key-pair for an ElasticBeanstalk ec2 instance with the current UI is: Warning: This will require an update of EC2 instances in your ElasticBeanstalk App. Note: You will need to have created a key-pair in the EC2 dashboard prior to this.
1) In AWS Dashboard, Select the ElasticBeanstalk service 2) Select the Application you want to use. 3) Select 'Configuration' 4) Select the gear (settings) icon on the 'Instances' configuration box. 5) This will take you to a page titled 'Server', where you can update the 'EC2 key pair' drop-down field with your desired key-pair and select 'Save'.
One thing to note is that this may not work for Applications with multiple instances (but I believe it's likely if they are all in the same region as the key-pair).
I came here looking for a way to add a key to an instance Beanstalk creates during provisioning (we're using Terraform). You can do the following in Terraform:
resource "aws_elastic_beanstalk_environment" "your-beanstalk" {
...
setting {
namespace = "aws:autoscaling:launchconfiguration"
name = "EC2KeyName"
value = "${aws_key_pair.your-ssh-key.key_name}"
}
...
}
You can then use that key to SSH into the box.
If you have set up the CLI using eb init to your environment then it should be as
simple as
eb ssh --setup which will allow you to create a new key pair or use an existing one if one exists.
You may also be able to just connect to the existing environment with eb use although I have not done that.
For details on installing the CLI - https://docs.aws.amazon.com/console/elasticbeanstalk/eb-cli-install
Depending on your environment configuration, you may not have a public IP address on the EC2 instance that was created for your environment. You can check by:
- Go to the EC2 Console
- Find your instance and check the Description tab
- If there is no Public IP...
- Click Elastic IPs on the Navigation
- Click Allocate new address
- Choose Amazon for the pool
- Click Allocate
Finally, select your new EIP and choose Associate address from the action menu. Associate that IP with your EC2 instance. You should be able to connect using eb ssh now.
You can reset the connection details by running eb ssh --setup.
Elastic Beanstalk can bind a single EC2 keypair to an instance profile. A manual solution to have multiple users ssh into EBS is to add their public keys in authorized_keys file.
Don't add your ssh key to elastic beanstalk
As others pointed out, these days, you can use the elastic beanstalk cli eb ssh to connect to your ec2 instance.
If you can't use the eb cli, but awscli, or came here looking for a simple way to ssh into any ec2 instance without the main key pair, you can also use the aws cli aws ec2-instance-connect as described here.
Note that the cli approach requires you to modify the security policies to allow the ssh connection, while eb handles both for you.
Both approaches require an AMI with EC2 Instance connect, which is the default these days and are preferred over associating the key directly, because you can allow multiple users to connect that way, the keys are only added for a short time, you don't need to consider it upfront and you stay in central control permission wise through IAM. No additional removal, if the key holder leaves the team. In general, I'd advise against setting up ssh key pairs these days on ec2
I also ran into the same problem awhile ago. I wanted to use the key file, but Amazon says somewhere that you cannot add a key file to an existing EC2 server. For the first Beanstalk application, Amazon preconfigures the application for you. You need to create a new application, and you can configure the EC2 server that runs the Beanstalk app to use an old pem file (ppk if using Putty), or you can create a new one. Now you should be able to SSH.

Then configure, then delete your old app.
© 2022 - 2024 — McMap. All rights reserved.

eb ssh– Univalent