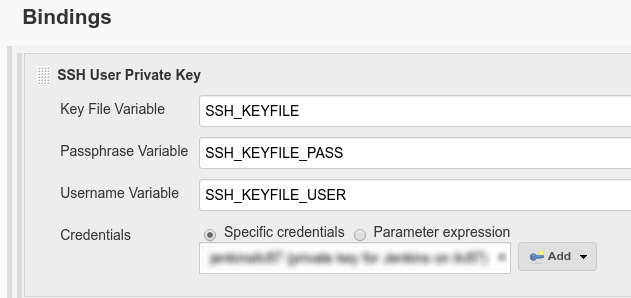
Our build job on Jenkins runs as part of a release build some git commands like git push and git pull, therefore requires a way to run authenticated git commands from the shell during the build.
Our jenkins slaves don't hold any credentials as they are disposable docker containers that are created per build.
The git plugin manages this with the Jenkins credentials and "somehow" sets GIT_SSH to pick up a private key that is configured via the credentials.
I checked the source code and tried to determine how I can get the variable configured so that I can run for example git pull as an SSH script as part of the build. Without success.
Is there a way to run a git command as part of the build steps using the Jenkins credentials?
My current solution is to copy the SSH key to the slave as part of the build environment setup but seems like duplicate work (plus potential security issue).