I had the same problem, and it wouldn't let me edit that entry to grant access to %USERS%
I followed this tutorial. It has 3 workarounds for this problem.
For me, Method 2: Changing the owner to Users worked:
Perhaps the most effective fix for this particular issue is to change
the Owner of the folder/file and to take full ownership of it. After
doing this, you should be able to edit the permissions without
encountering the ‘Access Control Entry is Corrupt‘ error.
- Right-click on the folder or file that you’re having issues with and
choose Properties from the context menu.
- Once you’re inside the Properties screen, select the Security tab, click on the
Advanced button associated with Permissions.
- Inside the Advanced Security Settings, click on the Change button associated with the
Owner.
- Inside the Select User or Group, type Users inside the text box, then click
on Check Names to verify. If the syntax is replaced correctly, click
Ok to save the changes. Then click Apply at the previous window to
make the change permanent.
- Try to modify the permissions accordingly
and see if you still see the error message.

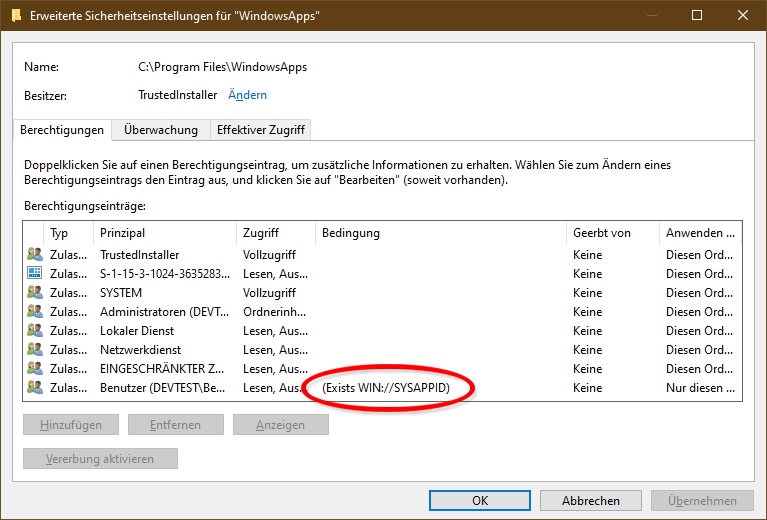
(XA;;0x1200a9;;;BU;(Exists WIN://SYSAPPID))conditionally grants (XA) read and execute access (0x1200a9) to users (BU) when the effective access token has an attribute named "WIN://SYSAPPID". Another example,(XA;OICI;0x1200a9;;;BU;(WIN://SYSAPPID Contains "MICROSOFT.WINDOWSSTORE_8WEKYB3D8BBWE"))uses the "Contains" operator to check for a specific value of the attribute. – FloddenCreateProcessW, which gets the information to create the custom access token from fields in the app execution alias, which, if enabled for an installed app, is in the user's "%LocalAppData%\Microsoft\WindowsApps" directory. – Flodden