There are 6 kinds of namespaces in linux: Network, UTS, Users, Mount, IPC, Pid. I know that all the containers share the same network namespace with the pause container in a Kubernetes pod. And by default, different containers have different PID namespaces because they have different init process. However, how about other namespaces and why?
According to this article:
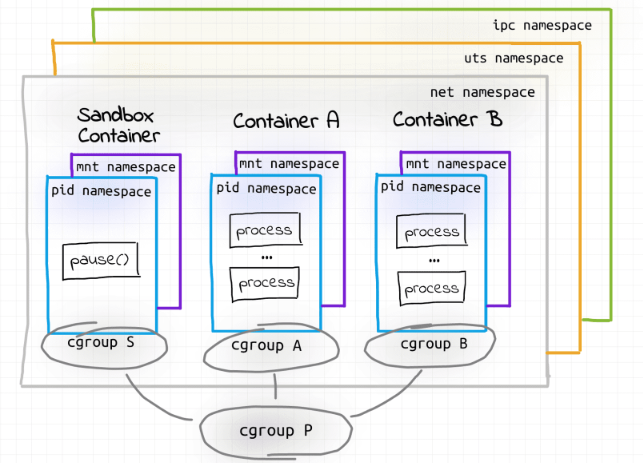
Containers in a Pod run on a “logical host”; they use the same network namespace (in other words, the same IP address and port space), and the same IPC namespace.
Containers in a Pod share the same IPC namespace, which means they can also communicate with each other using standard inter-process communications such as SystemV semaphores or POSIX shared memory.
Containers in a Pod are accessible via “localhost”; they use the same network namespace. Also, for containers, the observable host name is a Pod’s name. Because containers share the same IP address and port space, you should use different ports in containers for incoming connections. In other words, applications in a Pod must coordinate their usage of ports.
You can also enable sharing Process namespace between containers in a Pod by specifying v1.PodSpec.shareProcessNamespace: true.
ipc, net and uts namespace are shared.
pid: By default its not shared. However the namespace sharing can be enabled in the pod spec.
mnt: Not shared. Different containers are built from different images. From each container only its own root directory will be visible.
user: This is not supported by k8s and some form of user namespace sharing could be implemented in the future as mentioned here.
© 2022 - 2024 — McMap. All rights reserved.