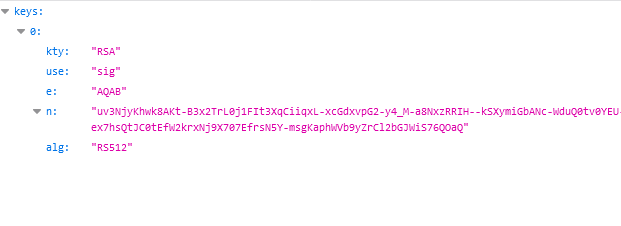
I have an RSA512 JWKS released by Identity Server 4 which is used by clients to validate the token signature. The problem is that I also wanted to validate it on the https://jwt.io/ site but I don't know how to transform the parameters:
in a public key such as this:
-----BEGIN PUBLIC KEY-----
MIIBCgKCAQEA+xGZ/wcz9ugFpP07Nspo6U17l0YhFiFpxxU4pTk3Lifz9R3zsIsu ERwta7+fWIfxOo208ett/jhskiVodSEt3QBGh4XBipyWopKwZ93HHaDVZAALi/2A +xTBtWdEo7XGUujKDvC2/aZKukfjpOiUI8AhLAfjmlcD/UZ1QPh0mHsglRNCmpCw mwSXA9VNmhz+PiB+Dml4WWnKW/VHo2ujTXxq7+efMU4H2fny3Se3KYOsFPFGZ1TN QSYlFuShWrHPtiLmUdPoP6CV2mML1tk+l7DIIqXrQhLUKDACeM5roMx0kLhUWB8P +0uj1CNlNN4JRZlC7xFfqiMbFRU9Z4N6YwIDAQAB
-----END PUBLIC KEY-----
that can be used on the site to validate the Token. Is there any kind of library or something free that I can use to do this? At the moment I found this library, but is it paid.
https://www.example-code.com/mono/publickey_rsa_load_jwk.asp
UPDATE
I have tried this snippet of code:
using var httpClient = new HttpClient();
var json = httpClient.GetStringAsync(
"http://..../.well-known/openid-configuration/jwks").GetAwaiter()
.GetResult();
var jsonWebKeySet = new JsonWebKeySet(json);
var jsonWebKey = jsonWebKeySet.Keys.First();
var rsaProvider = new RSACryptoServiceProvider();
rsaProvider.ImportParameters(new RSAParameters
{
Modulus = Base64Url.Decode(jsonWebKey.N),
Exponent = Base64Url.Decode(jsonWebKey.E)
});
var publicKey = Base64Url.Encode(rsaProvider.ExportRSAPublicKey());
Using the Base64Url class of the Jose library, but I get a public key in Base64Url that is not safe, that is, containing the characters _ and -. I also tried to do the substitution of the relative characters with / and +, but anyway and I always get Invalid Signature, while with the other library everything works. What am I doing wrong? Thanks
UPDATE Thanks to @Topaco's suggestion I modified the last line of code like this:
var publicKey = Convert.ToBase64String(rsaProvider.ExportSubjectPublicKeyInfo());
and after having correctly indented the key and inserted the header
-----BEGIN PUBLIC KEY-----
and footer
-----END PUBLIC KEY-----
the validation of the JWT on the site https://jwt.io/ is done correctly. Thanks

ExportSubjectPublicKeyInfo().Also, jwt.io expects a PEM encoded key and PEM does not use Base64url but standard Base64 (e.g. withConvert.ToBase64String()). – MononuclearPemWriterclass for this purpose, which generates the PEM encoded key from the DER encoded key (= return value ofExportSubjectPublicKeyInfo()). – Mononuclear