AWS recently announced the need to:
Update Your Amazon RDS SSL/TLS Certificates by October 31, 2019
I have a Rails application hosted with a classic Elastic Beanstalk load balancer, which connects to a Postgres DB using RDS.
The required steps according to Amazon are:
- Download the new SSL/TLS certificate from Using SSL/TLS to Encrypt a Connection to a DB Instance.
- Update your database applications to use the new SSL/TLS certificate.
- Modify the DB instance to change the CA from rds-ca-2015 to rds-ca-2019.
(https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/UsingWithRDS.SSL-certificate-rotation.html)
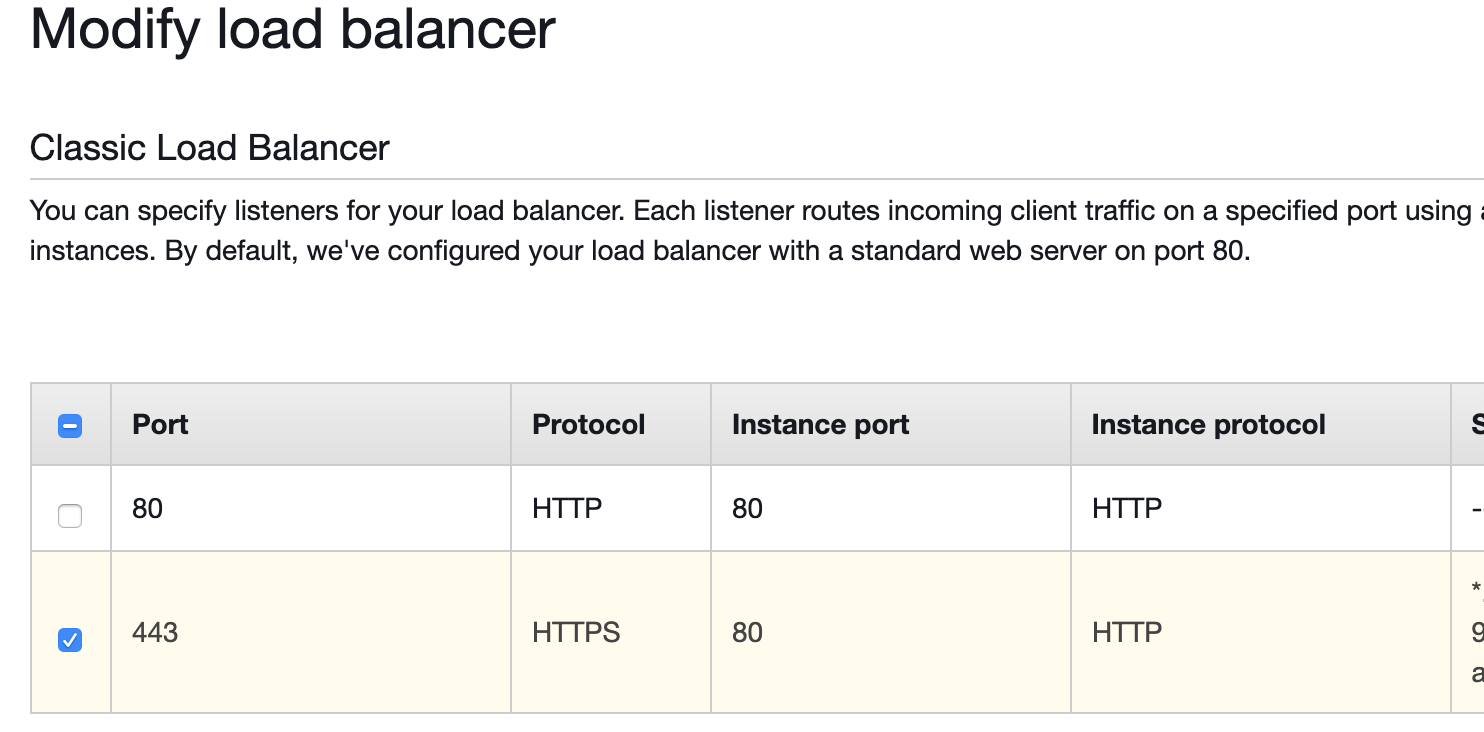
Since I have my load balancers set up like this (connecting to my EC2 instances via HTTP port 80 (not SSL), does this mean I don't need to follow steps 1 and 2? And only follow step 3?
Or do I have to download the updated certificates and install/add them to my Load balancer or EC instances manually? Not sure how to do that.

.ebextensions. In the end after testing it, I could confirm that they did automatically trust the new RDS connection. If the RDS DB instance was decoupled from the EB environment as described herehttps://docs.aws.amazon.com/elasticbeanstalk/latest/dg/AWSHowTo.RDS.html, then I'm not sure of the outcome. – Studner