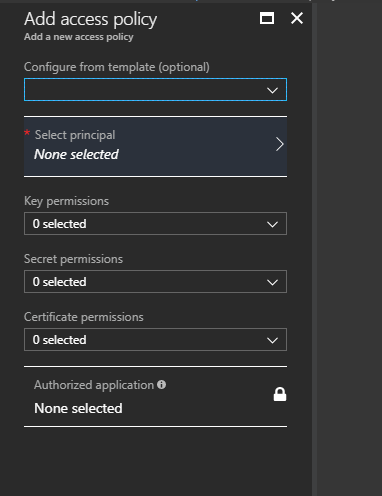
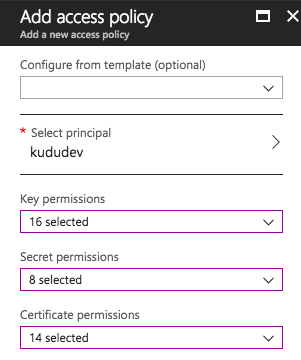
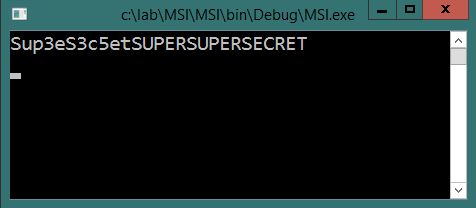
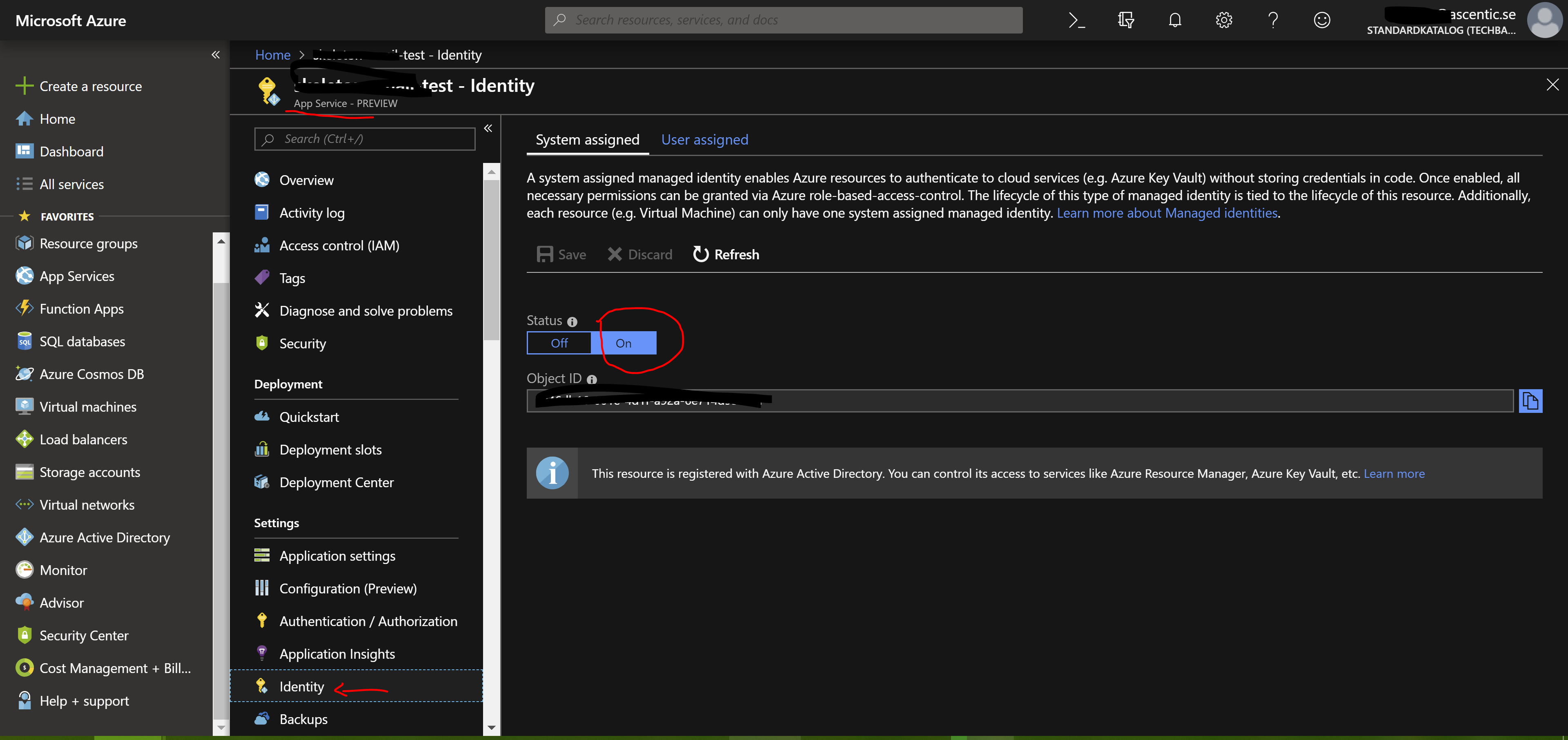
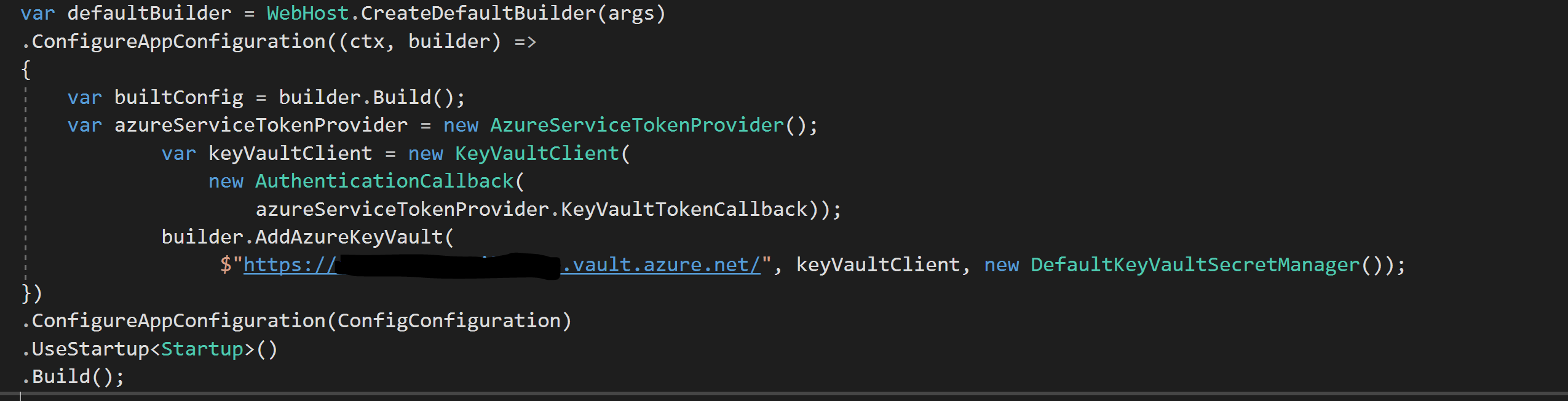
I am trying to connect to my azure vault from a console application with using MSI
For this vault i have added my user as the Selected Principle
the code i am using to connect is
var azureServiceTokenProvider = new AzureServiceTokenProvider();
var keyVaultClient = new KeyVaultClient(new KeyVaultClient.AuthenticationCallback(azureServiceTokenProvider.KeyVaultTokenCallback));
var secret = await keyVaultClient.GetSecretAsync("https://<vaultname>.vault.azure.net/secrets/<SecretName>").ConfigureAwait(false);
I get the following exception
Microsoft.Azure.Services.AppAuthentication.AzureServiceTokenProviderException: Parameters: Connectionstring: [No connection string specified], Resource: https://vault.azure.net, Authority