I'm having trouble understanding why "Authorization: Bearer __" is not being sent in my api using Springfox 2.5.0. I have the following configuration:
private ApiKey apiKey() {
return new ApiKey(
"Authorization", // name: My key - Authorization
"api_key", // keyname: api_key
"header");
}
@Bean
SecurityConfiguration security() {
return new SecurityConfiguration(
null, null, null,
"Docserver2_fwk", // app name
"BEARER", // api key value
ApiKeyVehicle.HEADER, "Authorization", ",");
}
It seems I am unable to send "Authorization: Bearer Token" in springfox (2.5.0), is this possible?, is it a known problem?
Similar issue: https://github.com/springfox/springfox/issues/1812
PS: OpenAPI 3.0 allows the "bearer" format, example: https://github.com/OAI/OpenAPI-Specification/blob/master/versions/3.0.1.md#jwt-bearer-sample
Thanks.

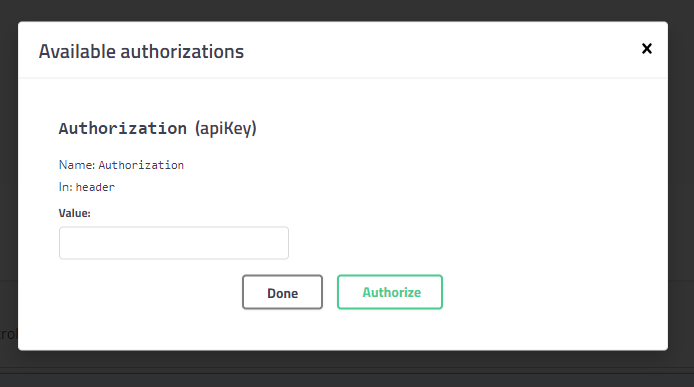
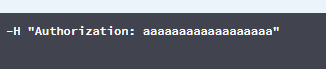
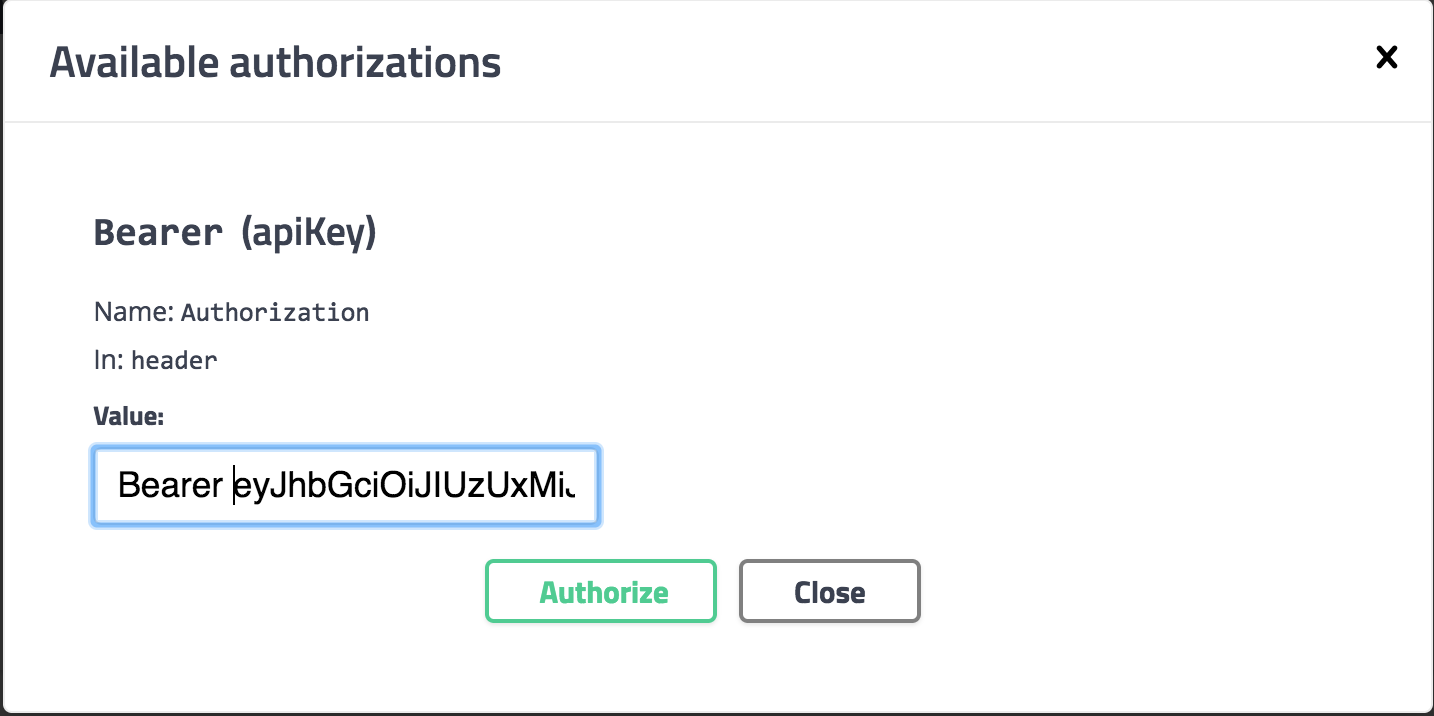
Bearer– MagenmagenaBearer <key>– Magenmagena2.7.0to2.8.0and my working code stopped working i.e. swagger stopped passingAuthorizationheader. I see lots of folks reporting on github for same issue but I am not able to make out any solution. – Zalucki