Scenario
I want to use virtual network in order to limit access to Azure Database only from my App Service, so that I can turn of "Allow access to App Services" in firewall settings
What I have done:
- I went to App Service -> Networking -> VNET Integration -> Setup -> Create New Virtual Network
- I've created new VNET with default settings.
- When VNET was created I went to App Service -> Networking -> VNET Integration and ensured that the VNET is connected
- I went to SQL Firewall settigs -> Virtual Network -> Add existing Virtual Newtork and selected my VNET. I've left default subnet and address space: "default / 10.0.0.0/24" and I've left IgnoreMissingServiceEndpoint flag unchecked.
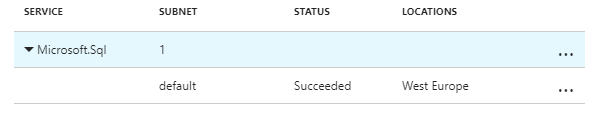
I can now see Microsoft.Sql service endpoint in my VNET:
Question
However, I'm still getting
SqlException: Cannot open server 'my-sqlserver' requested by the login. Client with IP address '52.233..' is not allowed to access the server.:
What am I missing?


