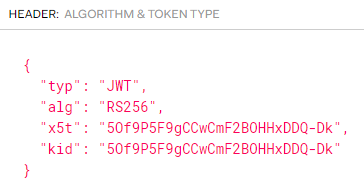
I am trying to implement the "On-Behalf-Of" flow between my Client (ReactJS), Express + Node.js server (API), and Microsoft Graph.
So far I have requested an accessToken from microsoft (Client), and have made a request to my API.
I have ran into the error "AADSTS5002710: Invalid JWT token: header is malformed." when I try to make an Axios post request from my API to https://login.microsoftonline.com/tenantID/oauth2/v2.0/token
Full Error:
{
error: 'invalid_request',
error_description: 'AADSTS5002710: Invalid JWT token: header is malformed.\r\n' +
'Trace ID: 068a382b-6f83-40f6-b1b1-7134223f4500\r\n' +
'Correlation ID: f46a2c03-84e8-46b3-b9d6-467174befa0b\r\n' +
'Timestamp: 2021-01-06 16:26:40Z',
error_codes: [ 5002710 ],
timestamp: '2021-01-06 16:26:40Z',
trace_id: '068a382b-6f83-40f6-b1b1-7134223f4500',
correlation_id: 'f46a2c03-84e8-46b3-b9d6-467174befa0b'
}
The body of my request is according to the tutorial "https://learn.microsoft.com/en-us/azure/active-directory/develop/v2-oauth2-on-behalf-of-flow".
I am constantly getting the error above as the result from microsoft online servers.
I have made the original (Client) request with my own custom scope api://54ee17f...cfe06/Access.Test