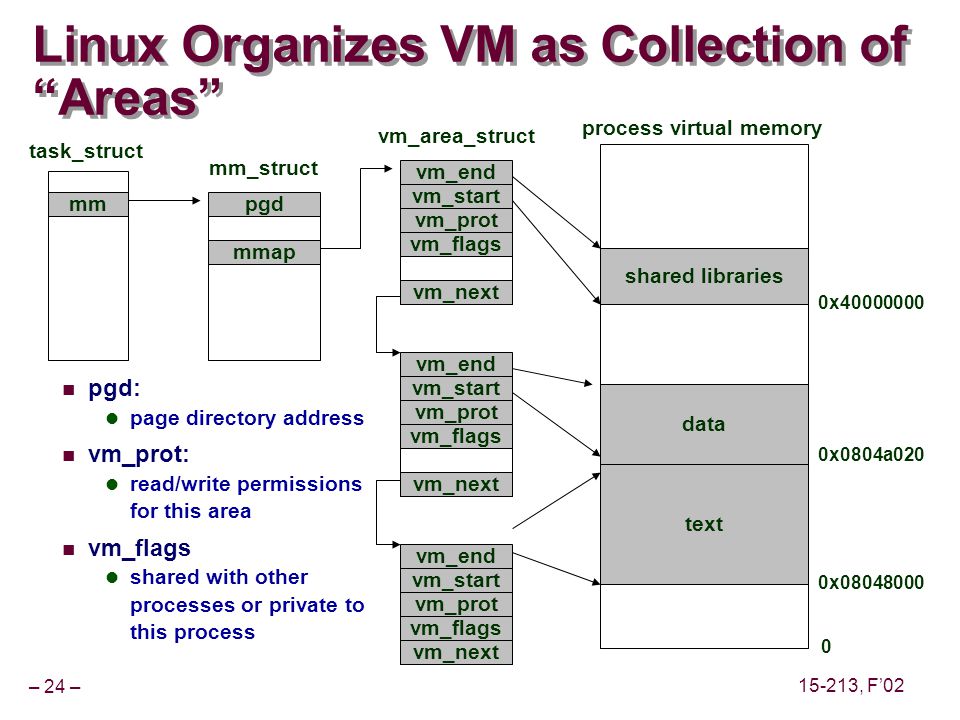
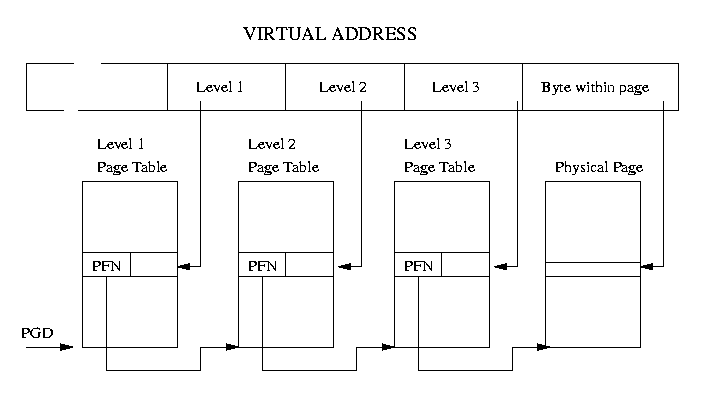
The internal bookkeeping with PTE objects explained by Peter Teoh 2012 is just how it is, so that the Linux kernel runs on various, current hardware. But the TO asked specifically about (1) character device drivers and (2) memory protection and pgprot_t objects.
When a user land process accesses memory it does not own the hardware creates a page fault. The kernel catches it and in do_page_fault either makes the page available to the process, or kills it to prevent damage because there clearly is a programming error.
We can prevent that by remapping kernel virtual addresses (e.g. converted from known physical addresses, static memory or memory allocated by kmalloc, get_free_page and friends) to the user space process. But when and where exactly? The TO mentioned a character driver that implements mmap, which is a function pointer in the file_operations object that the driver fills in when it loads. When a user land process calls mmap from the Standard C Library passing it the file path of the device driver as an argument, the kernel calls the registered mmap function.
It is within that function that remap_pfn_range is called. And the TO’s question was how exactly this works: "Can anyone explain precise steps?"
Well, this is where words start to fail and we have to turn to source code. Here is the mmap implementation of /dev/mem by Torvalds himself. As you can see it's basically a wrapper around remap_pfn_range. Unfortunately, if you look into the code you don't see any magic happening, just more bookkeeping. It reserves the page for the user process and modifies the pgprot_t value.
This is probably how it works: the first access to the mapped memory from the process initially generates a page fault, but now do_page_fault knows which process the page belongs to.
To return the page to the kernel, the process calls munmap.
This is a complex topic and so it would be good if someone would confirm/criticize/expand on my statements.