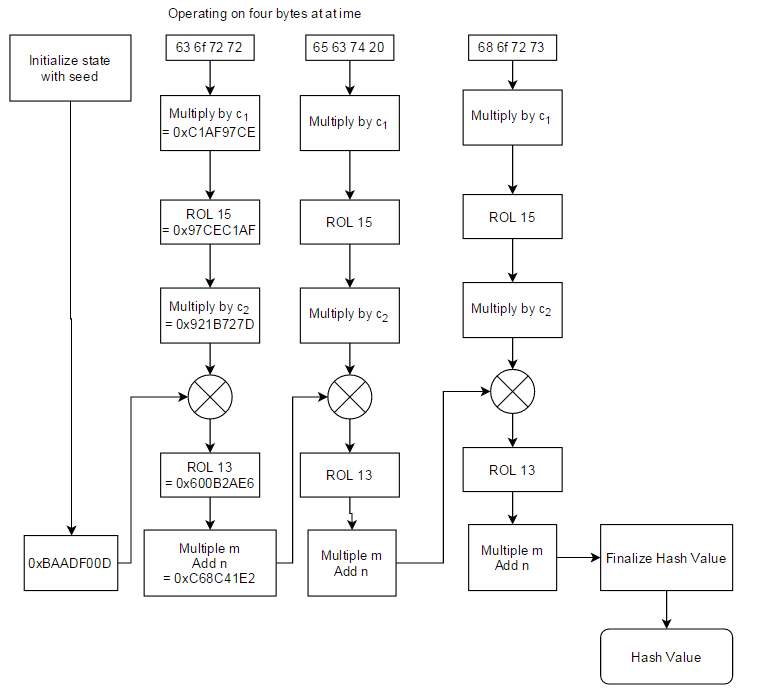
I just found out murmur hash, seems to be the fastest known and quite collision resistant. I tried to dig more about the algorithm or implementation in full source code, but I am having difficulty understanding it. Could someone here explain the algorithm used, or implement it in full source code, preferably in C. I read the C source code from the author website but has no idea, like: What is seed, h, k, m?
What does this mean? :
k *= m;
k ^= k >> r;
k *= m;
h *= m;
h ^= k;
data += 4;
len -= 4;
Reference : http://murmurhash.googlepages.com/