Google has published the detailed info in this article - Configuring secure remote access for Compute Engine VMs
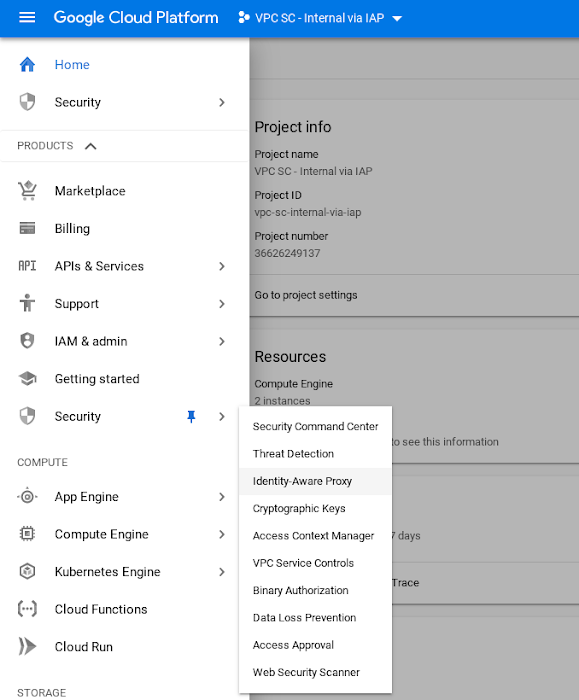
From the admin console, click Security then select Identity-Aware Proxy.
![enter image description here]()
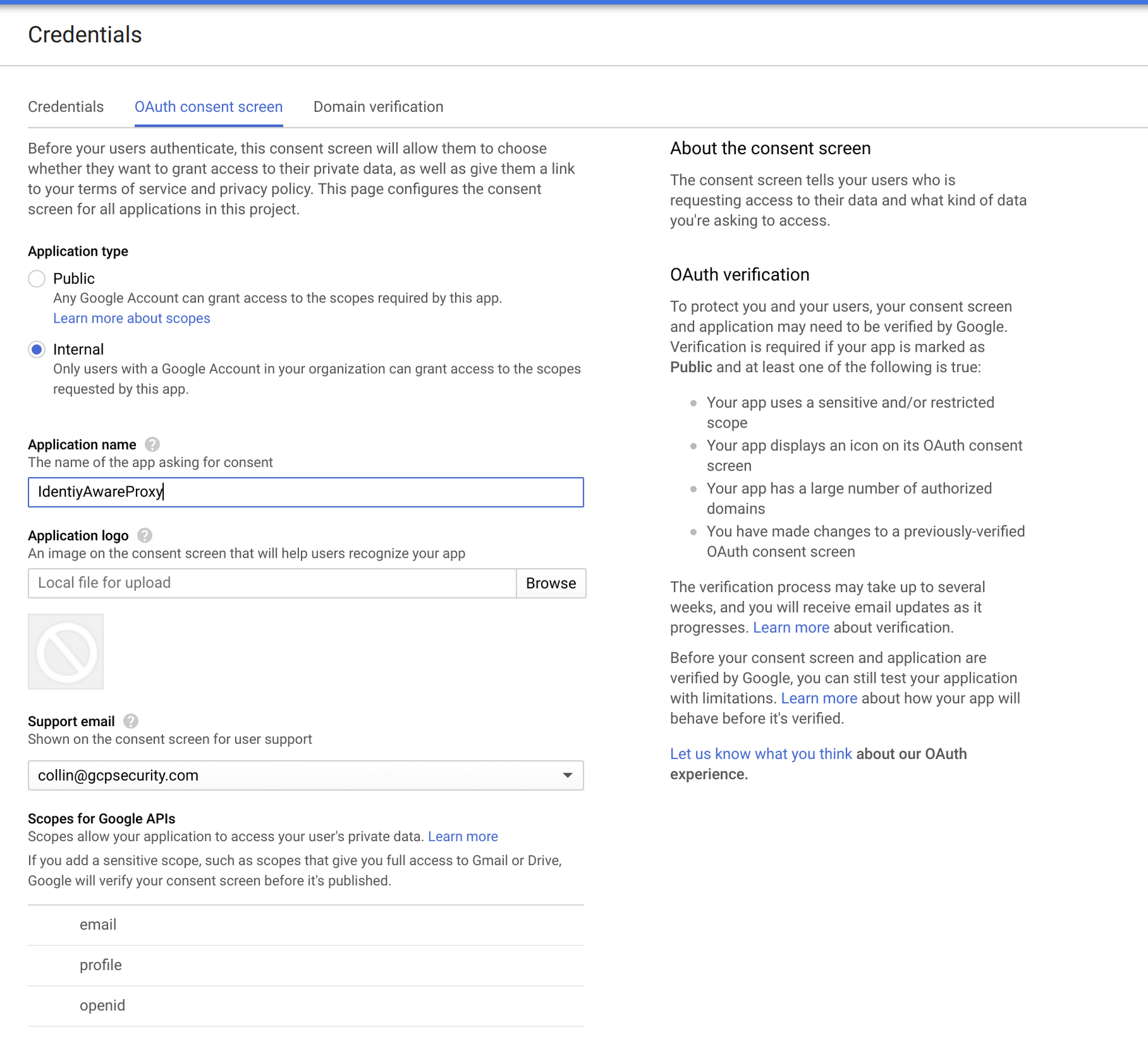
If you haven’t used Cloud IAP before, you’ll need to configure the oAuth screen:
![enter image description here]()
![enter image description here]()
Configure the consent screen to only allow internal users in your domain, and click Save.
Next, you need to define users who are allowed to use Cloud IAP to connect remotely. Add a user to the “IAP-secured Tunnel User” role on the resource you’d like to connect to.
![enter image description here]()
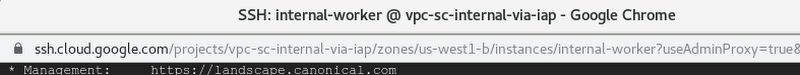
Then, connect to the machine via the ssh button in the web UI or gcloud.
![enter image description here]()
When using the web UI, notice the URL parameter useAdminProxy=true.
![enter image description here]()
Tip: If you don’t have gcloud installed locally, you can also use Cloud Shell:
gcloud beta compute ssh {VM-NAME} --tunnel-through-iap
You should now be connected! You can verify that you don’t have internet connectivity by attempting to ping out. 8.8.8.8 (Google’s Honest DNS) is a good address to try this with.