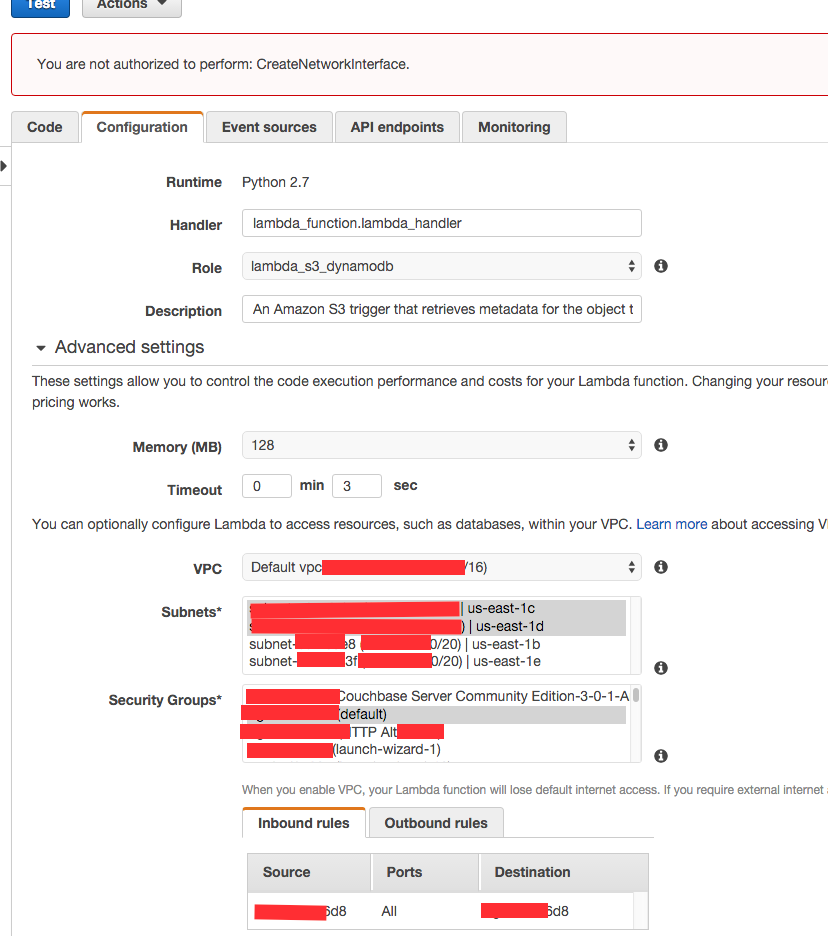
I am trying to setup my Lambda to access my Mongo server on one of the EC2 instances in VPC. After selecting all the subnets and security groups, I get the following error when saving
"You are not authorized to perform: CreateNetworkInterface."
I believe, I need some sort of policy setup in AWS IAM to allow this.
I have "AdministratorAccess" and I am trying to add IAM role to my account.
Does anyone know what policy/role I need for this?