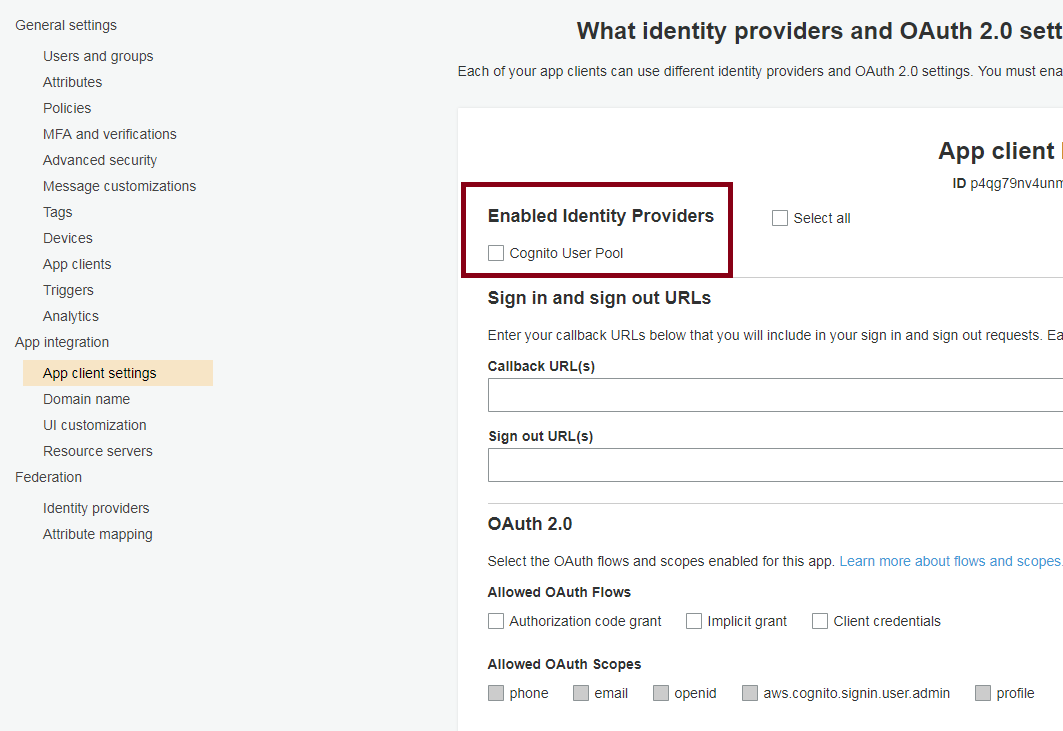
I am trying to run congnito via cloudformation and everything works but there is section in cognito as follows:
As you see there is section "Enable identity providers" and I can not find where I can set it to my cognito user pool in cloudformation!
I tried this attributes but it says not supported.
SupportedIdentityProviders
Here is my code for user pool client:
UserPoolClient:
Type: "AWS::Cognito::UserPoolClient"
Properties:
ClientName: !Sub ${project}-client
ExplicitAuthFlows:
- ADMIN_NO_SRP_AUTH
- USER_PASSWORD_AUTH
GenerateSecret: false
UserPoolId: !Ref UserPool
RefreshTokenValidity: 30
and here is my user pool:
UserPool:
Type: "AWS::Cognito::UserPool"
Properties:
UserPoolName: !Sub ${project}-user-pool-test
AutoVerifiedAttributes:
- email
UsernameAttributes:
- email
MfaConfiguration: "OFF"
LambdaConfig:
CustomMessage:
Fn::ImportValue: !Sub ${project}-${EnvironmentApp}-lambda-cognito-custom-message-post
Policies:
PasswordPolicy:
MinimumLength: !Ref MinimumLength
RequireLowercase: !Ref RequireLowercase
RequireNumbers: !Ref RequireNumbers
RequireSymbols: !Ref RequireSymbols
RequireUppercase: !Ref RequireUppercase
Schema:
-
AttributeDataType: String
DeveloperOnlyAttribute: false
Mutable: true
Name: !Sub ${project}-stg
Required: false
-
AttributeDataType: String
DeveloperOnlyAttribute: false
Mutable: true
Name: !Sub zuora-stg
Required: false
-
AttributeDataType: String
DeveloperOnlyAttribute: false
Mutable: true
Name: !Sub salesforce-stg
Required: false
Is it supported in cloud formation? I appreciate any help?