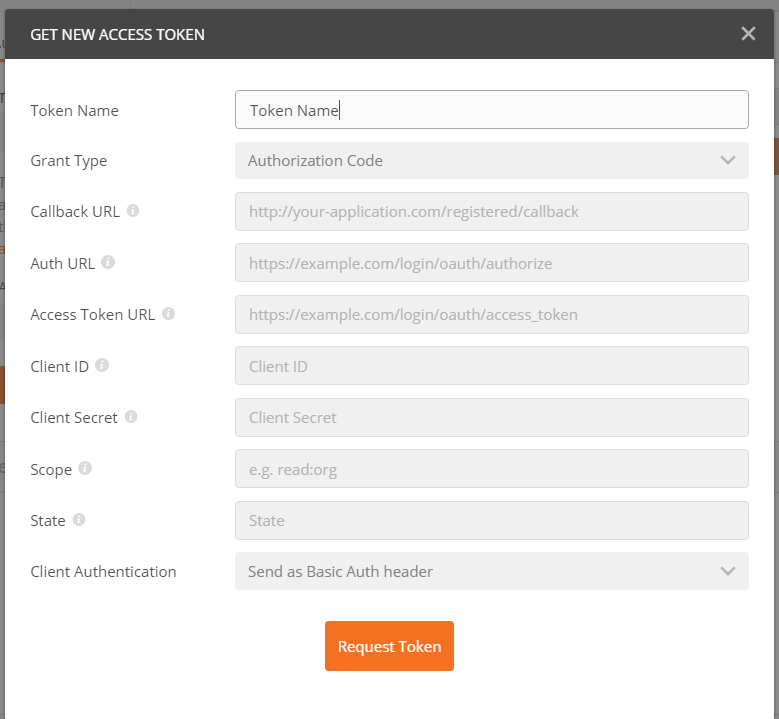
How can I request an Access Token in Postman against an Azure AD B2C tenant?
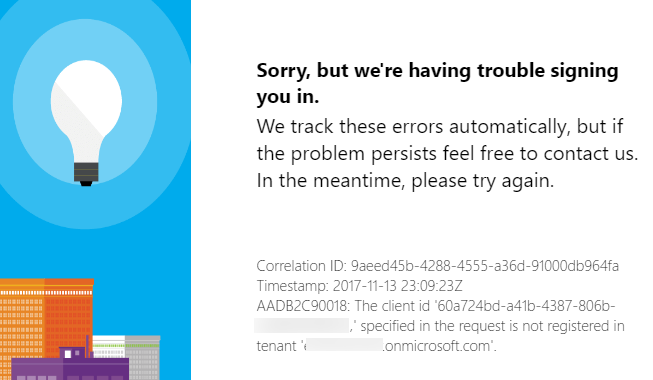
I tried taking the url from Run Now in the Azure portal and putting that in the Auth Url but that produces the following error:
Update
Following Chris's answer, I'm now past the above error. I'm able to sign-in but still can't get an access token:
AADB2C90085: The service has encountered an internal error. Please reauthenticate and try again. Correlation ID: 45c56d47-4739-465f-8e02-49ba5b3a1b86 Timestamp: 2017-11-16 15:27:52Z