Push and image to Azure Container Registry task in Azure DevOps pipeline fails. Previous tasks are executed fine ie. docker image is created and login to ACR is successful. However, push-task fails with the following result:
unauthorized: authentication required
[error]unauthorized: authentication required
[error]/usr/bin/docker failed with return code: 1
[section]Finishing: Push Docker image
docker push to that given acr works fine from local command line.
# Docker image
# Build a Docker image to deploy, run, or push to a container registry.
# Add steps that use Docker Compose, tag images, push to a registry, run an image, and more:
# https://learn.microsoft.com/azure/devops/pipelines/languages/docker
trigger:
- master
pool:
vmImage: 'Ubuntu-16.04'
variables:
imageName: 'renamed:$(build.buildId)'
azureSubscriptionEndpoint: Renamed
azureContainerRegistry: renamed.azurecr.io
steps:
- task: Docker@1
displayName: Build docker image
inputs:
command: Build an image
dockerFile: Dockerfile
imageName: $(imageName)
containerregistrytype: Azure Container Registry
azureSubscriptionEndpoint: $(azureSubscriptionEndpoint)
azureContainerRegistry: $(azureContainerRegistry)
- task: Docker@1
displayName: Login to container registry
inputs:
command: login
containerregistrytype: Azure Container Registry
azureSubscriptionEndpoint: $(azureSubscriptionEndpoint)
azureContainerRegistry: $(azureContainerRegistry)
dockerFile: Dockerfile
imageName: $(imageName)
- task: Docker@1
displayName: Push Docker image
inputs:
command: Push an image
containerregistrytype: Azure Container Registry
azureSubscriptionEndpoint: $(azureSubscriptionEndpoint)
azureContainerRegistry: $(azureContainerRegistry)
imageName: $(imageName)

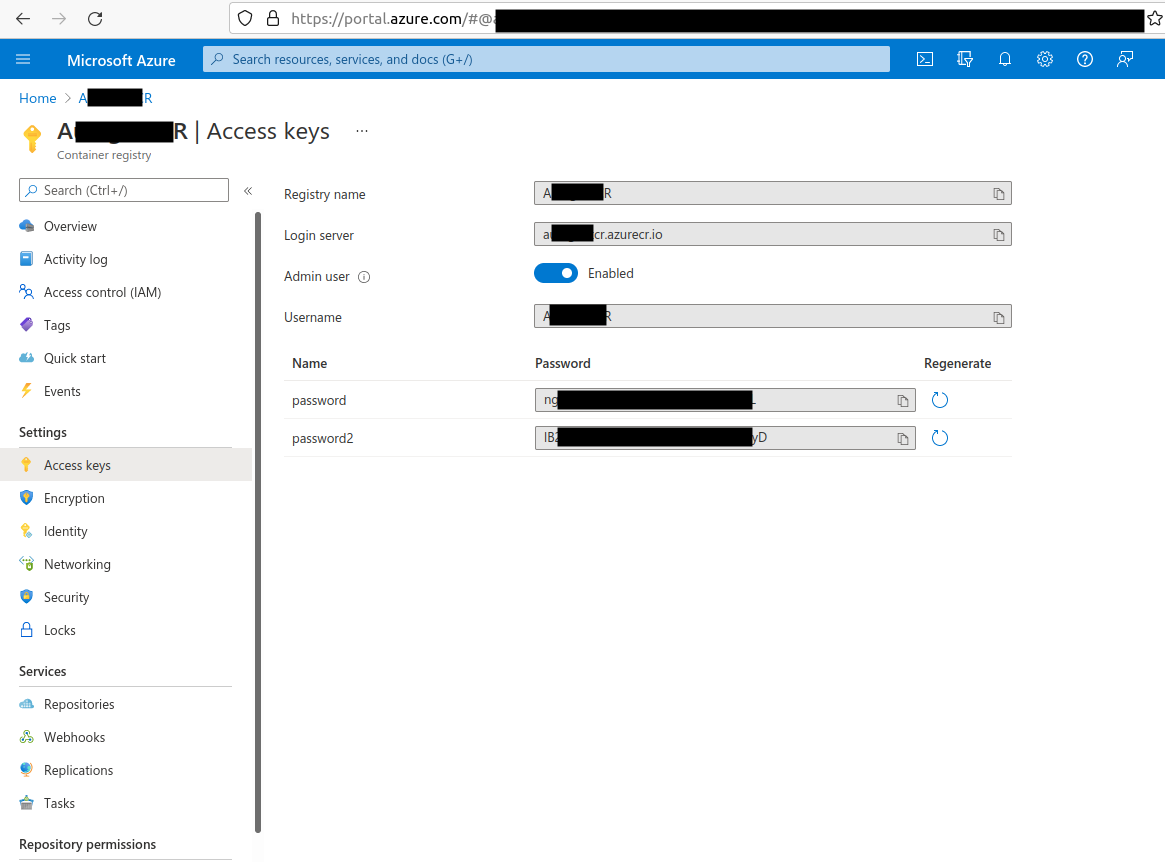
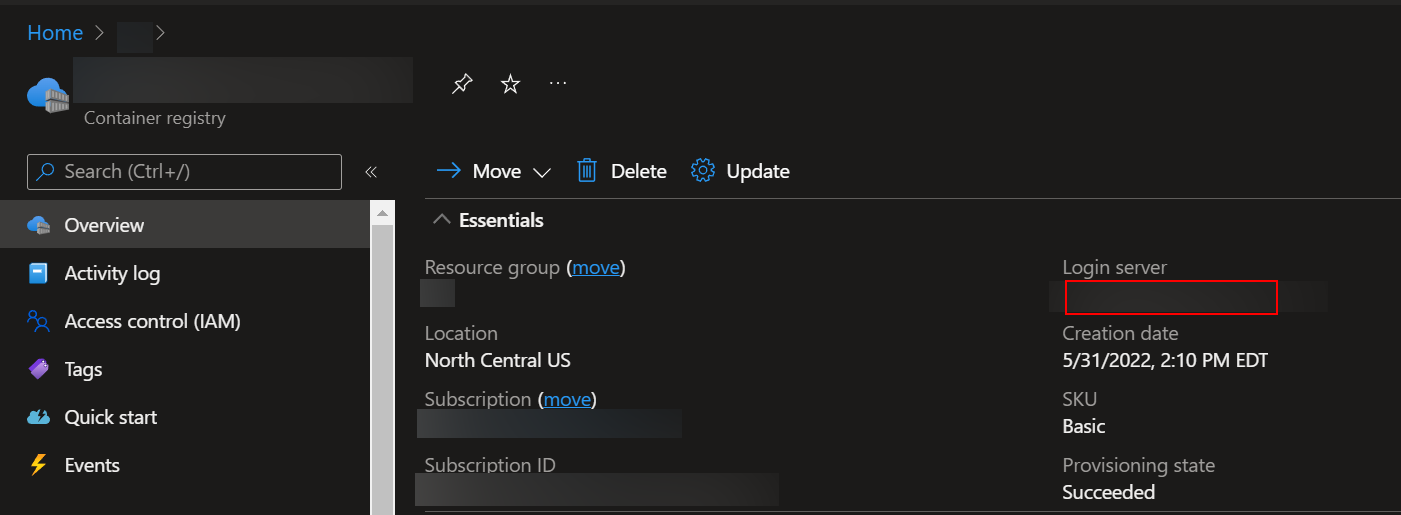
https://yourregistry.azurecr.io. – Nihon