I installed MSYS2-64bits on my Windows Server 2016 to support some Linux librairies, such as OpenSSL, which I need in my Ruby on Rails development. MSYS2 has been partially installed with Ruby 2.7, but did not complete due to certificates error messages.
I first downloaded and install msys2-x86_64-20210725.exe. It took a very long time and finished after a few messages about Updating the trust database:
==> Generating pacman master key. This may take some time.
==> Updating trust database...
==> Appending keys from msys2.gpg...
==> Locally signing trusted keys in keyring...
-> Locally signed 6 keys.
==> Importing owner trust values...
==> Disabling revoked keys in keyring...
-> Disabled 1 keys.
==> Updating trust database...
It stayed about 10 minutes at this stage, but finally declared a successful installation.
Then I tried to update the existing software by running pacman -Syuu. I restarted MSYS2 as requested, typed the statement, and got lots of errors such as the following, repeatedly:
$ pacman -Syuu
:: Synchronizing package databases...
mingw32.db failed to download
mingw64.db failed to download
ucrt64.db failed to download
clang64.db failed to download
msys.db failed to download
error: failed retrieving file 'mingw32.db' from mirror.msys2.org : SSL certificate problem: self signed certificate in certificate chain
error: failed retrieving file 'mingw64.db' from mirror.msys2.org : SSL certificate problem: self signed certificate in certificate chain
error: failed retrieving file 'ucrt64.db' from mirror.msys2.org : SSL certificate problem: self signed certificate in certificate chain
warning: too many errors from mirror.msys2.org, skipping for the remainder of this transaction
I am afraid that the corporate proxy could refuse self-signed certificates. Is there a way to obtain correctly signed certificates and finalise the installation of all the packages?
Thanks for your help!

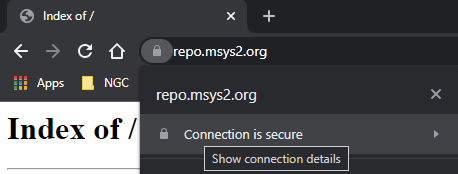
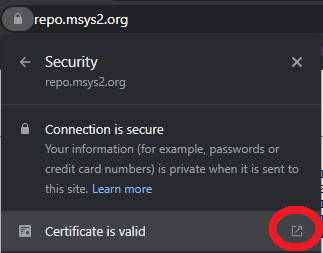
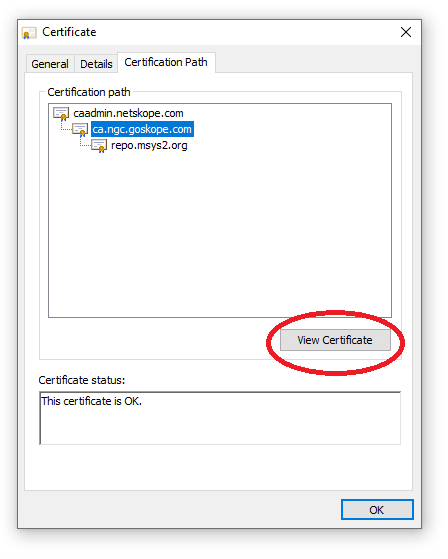
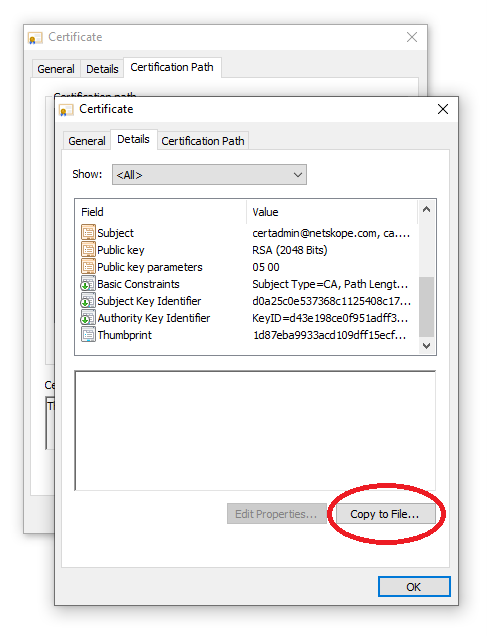
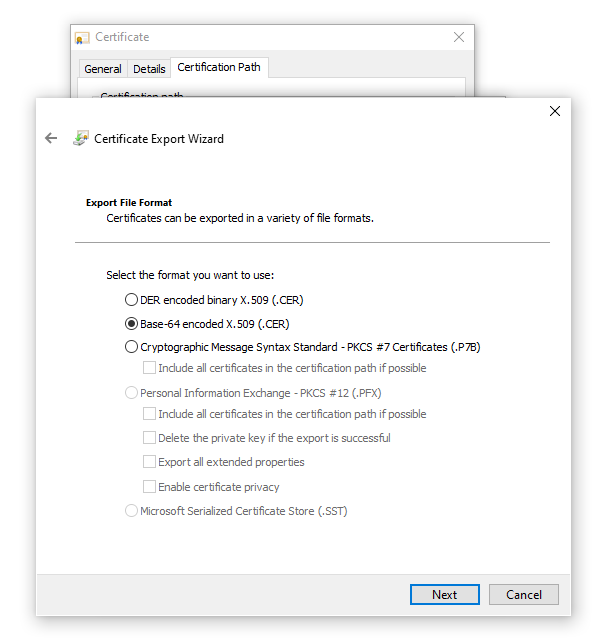
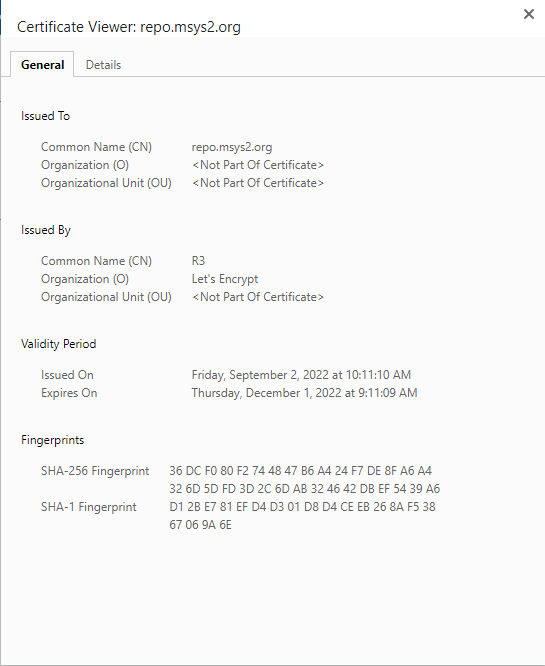
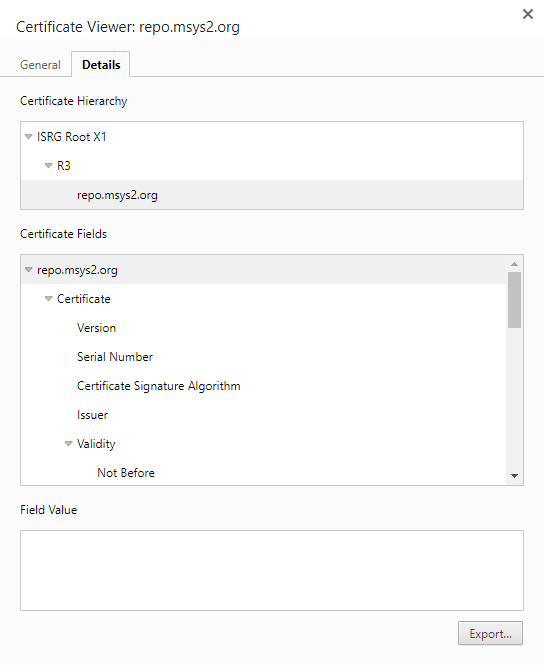
.crtand need to rename toca-bundle.crtthen put inC:\msys64\usr\ssl\certs. relative github.com/msys2/MSYS2-packages/issues/2529 – Speos