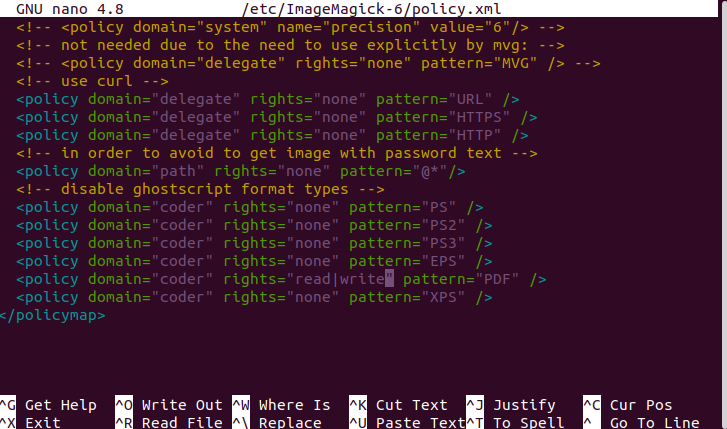
The ImageMagick change was kept after Ghostscript was fixed because applications (especially web applications) often feed arbitrary user-supplied files to ImageMagick, don't always enforce format restrictions properly, and, since Postscript (which PDF uses) is a turing-complete programming language running in a sandbox, there's always the possibility of another hole in the sandbox.
It's much better to leave things configured so ImageMagick refuses to process files that require running a program and, instead, just invoke Ghostscript directly when you intentionally want to permit Postscript rendering.
That would be accomplished by a Ghostscript command like this:
gs -dSAFER -r600 -sDEVICE=pngalpha -o foo.png myfile.pdf
Yes, this is a variation on the GhostScript command ImageMagic calls. (see ImageMagick's delegates.xml. -o is shorthand for -dBATCH -dNOPAUSE -sOutputFile=)
What's important is that ImageMagick stays locked down, you don't needlessly invoke an intermediate program, and you get more control over the rendering parameters. (eg. -r600 is the DPI to render at and changing -sDEVICE=pngalpha allows you to render directly to your desired format)