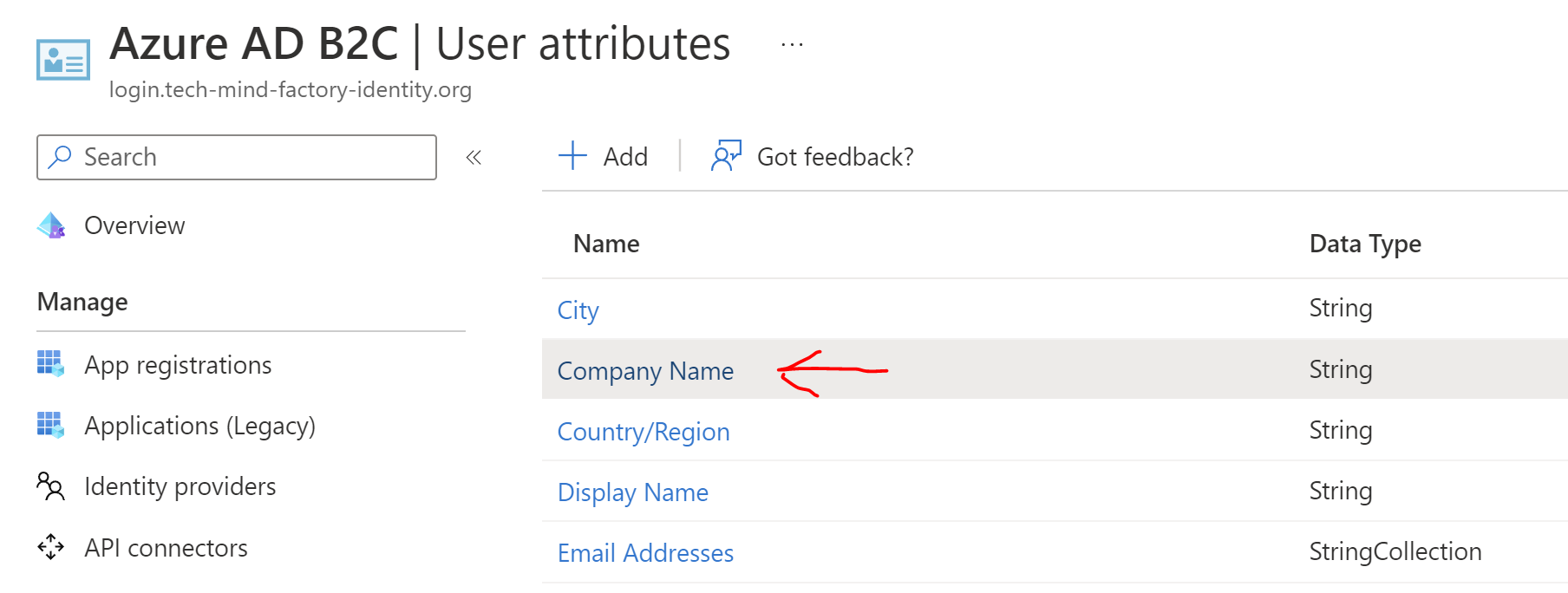
I have added a custom User Attribute named Company Name via:
Azure AD B2C > User attributes
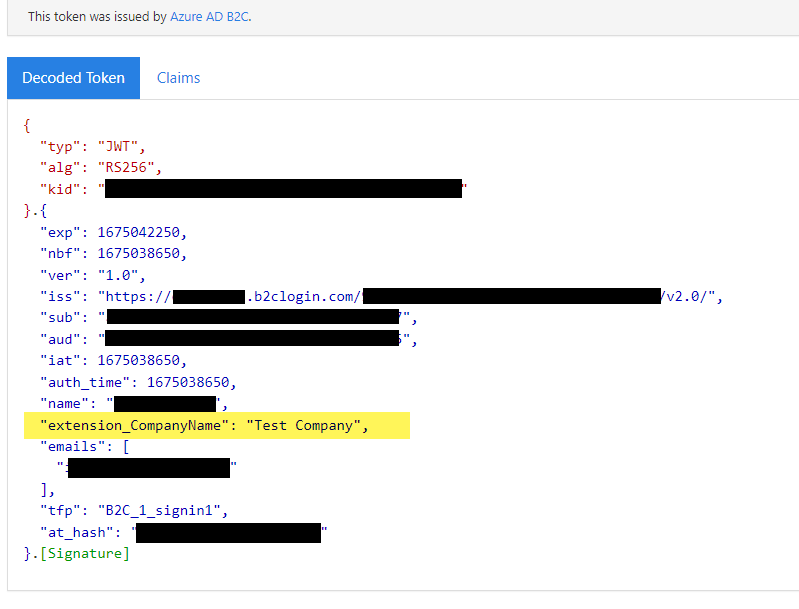
so that this information can be returned in the identity token after successful sign in.
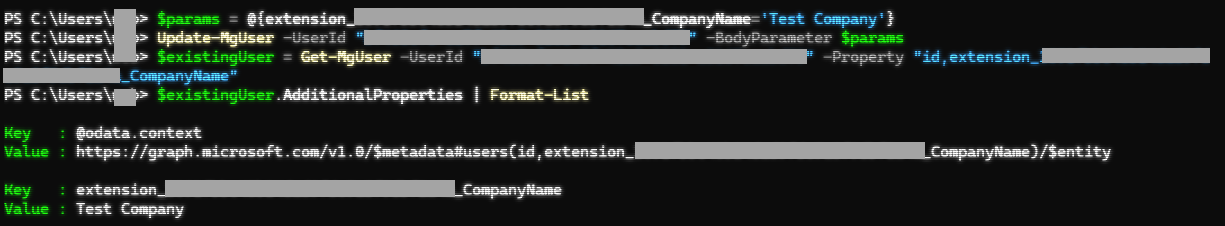
I want to update these values for each user in the Azure AD B2C tenant.
As I understand it:
I cannot update these values via Azure Portal
The only way to update these values is via Microsoft Graph, specifically these methods:
I don't want to have to create an application just to be able to perform this basic administrative task.
So I am looking at:
Microsoft Graph PowerShell SDK
I installed the Microsoft Graph PowerShell SDK in PowerShell 7.
I was prompted to sign in via the browser after running this command:
Connect-MgGraph -Scopes "User.Read.All","Group.ReadWrite.All"
At this point I was confused which credentials to login with.
I logged in using my 'home tenant' Azure AD credentials.
(i.e the admin credentials of the Azure AD tenant from which I created the Azure AD B2C tenant - which then automatically created a guest account in the B2C tenant with the user principal name of info_my-home-tenant.onmicrosoft.com#EXT#@my-dev-tenant.onmicrosoft.com).
I made the decision because I don't think I have any Azure AD B2C credentials.
(to access Azure AD B2C when I am logged into Azure Portal with my Azure AD credentials, I just click on 'switch directory').
I then ran:
Get-MgUser
And it, predictably, returned the users from my home Azure AD tenant, not the Azure AD B2C tenant.
So my question is:
In PowerShell 7, with the Microsoft Graph PowerShell SDK installed, how do I sign in so that I can interact with the Azure AD B2C tenant users, rather than my 'home' directory tenant users.
EDIT:
I started trying to follow the process described here:
Use app-only authentication with the Microsoft Graph PowerShell SDK
The first step is:
You'll need an X.509 certificate installed in your user's trusted store on the machine where you'll run the script
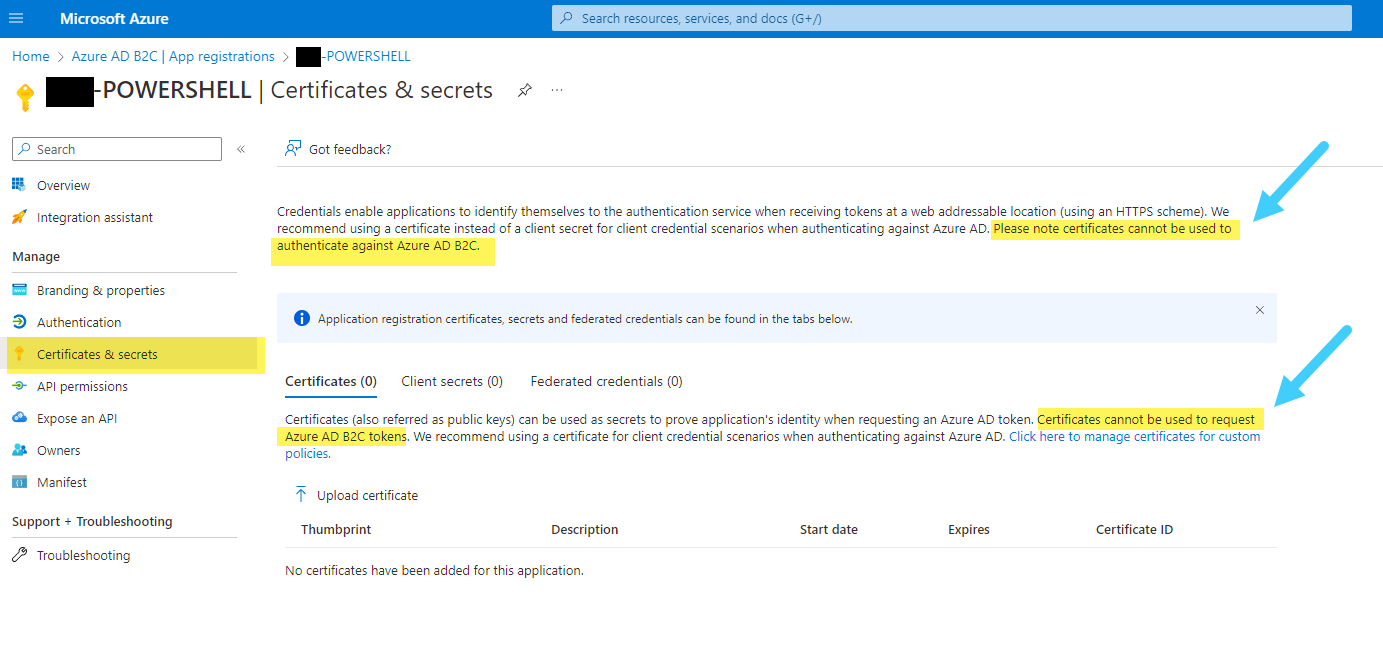
I created an Application Registration, however in the Certificates & secrets section it says:
Please note certificates cannot be used to authenticate against Azure AD B2C.