Our site is not currently safe from clickjacking, so I went into the web.config and added
<system.webServer>
<httpProtocol>
<customHeaders>
<add name="X-Frame-Options" value="DENY" />
</customHeaders>
</httpProtocol>
</system.webServer>
This is very straight forward code. My issue is that it's just not working. The questions I have are:
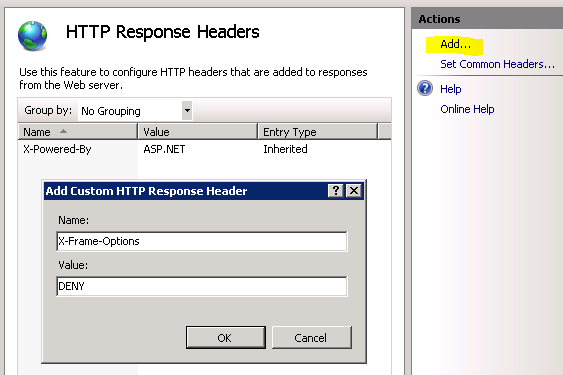
- Is there a way for me to see if the
X-Frame-Optionsis in the header response? I looked for it with httpfox and got nothing, so I can't verify if theweb.configis actually putting things in the header. - Why is this not working? What can I do to test or move forward?
I did try to add it in the Global.asax in the Application_Start method, but I cant seem to "hit" this method when I debug; it does not hit breakpoints.
private void Application_Start(object sender, EventArgs e)
{
// Code that runs on application startup
HttpContext.Current.Response.AddHeader("x-frame-options", "DENY");
LogHelper.Info("Cost of Care Web Application Starting");
}
I would like to add that I have tried to add it straight into the head tag and I've also tried to add it in a meta tag like so
<meta http-equiv="X-Frame-Options" content="deny">

X-Frame-Optionsdirectly in code:Response.AddHeader("X-Frame-Options", "DENY");I couldn't tell you why it doesn't work though as the documentation makes it look like it should. – Zooplastyprotected void Application_BeginRequest(){}method in Global.asax and add it in there. – Zooplasty