I've just moved away from IIS6 on Win2003 to IIS8 on Win2012 for hosting ASP.NET applications.
Within one particular folder in my application I need to Create & Delete files. After copying the files to the new server, I kept seeing the following errors when I tried to delete files:
Access to the path 'D:\WebSites\myapp.co.uk\companydata\filename.pdf' is denied.
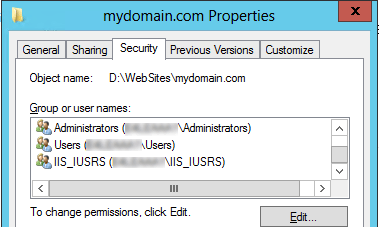
When I check IIS I see that the application is running under the DefaultAppPool account, however, I never set up Windows permissions on this folder to include IIS AppPool\DefaultAppPool
Instead, to stop screaming customers I granted the following permissions on the folder:
IUSR
- Read & Execute
- List Folder Contents
- Read
- Write
IIS_IUSRS
- Modify
- Read & Execute
- List Folder Contents
- Read
- Write
This seems to have worked, but I am concerned that too many privileges have been set. I've read conflicting information online about whether IUSR is actually needed at all here. Can anyone clarify which users/permissions would suffice to Create and Delete documents on this folder please? Also, is IUSR part of the IIS_IUSRS group?