Signature, Certificate
[Encoding Encryption Hashing]
[ASN.1, DER, PEM]
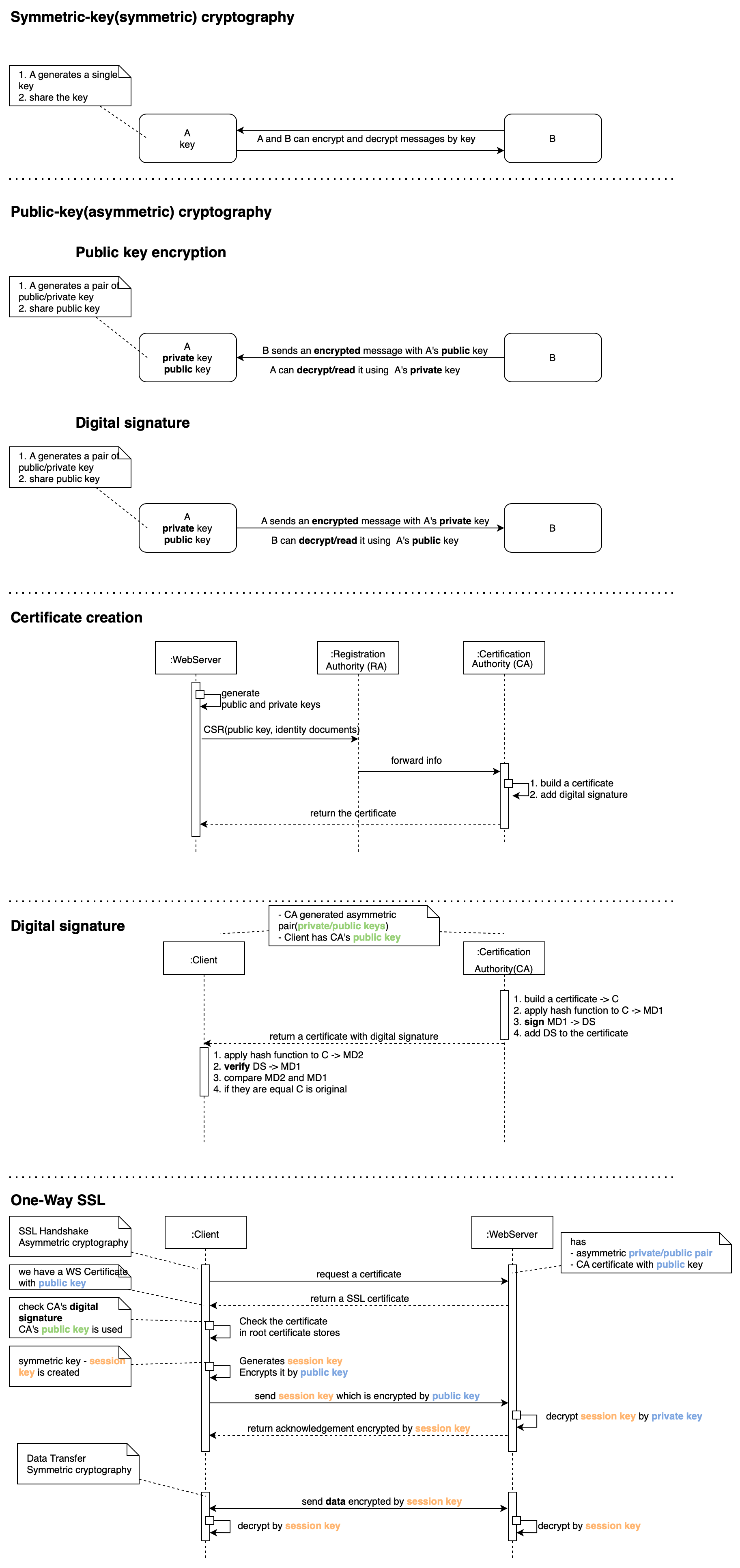
Digital Signature
Digital signature - ensures that some data(like message, document, file...) is sent by the intended side - verify Integrity, authenticity, Non-repudiation. Digital signatures can be attached(data is a part of signature) or detached[Example](data is not a part of signature and they are transported separately) to message.
//Create a signature by owner
1. owner of asymmetric key pair(private/public keys)
2. calculate a check sum of data: Message(M) -> Hash message by some hash algorithm -> message digest(MD1)
3. encode(**sign**) calculated check sum: encrypt message digest(MD1) by private key -> Digital signature(DS)
//Check a signature
1. calculate a check sum of data: Message(M) -> Hash message by some hash algorithm -> message digest(MD2)
2. decode(**verify**) digital signature: decrypt Digital signature(DS) by owner's public key -> message digest(MD1)
3. compare check sums from step 1 and 2: is MD2 == MD1
Digital Certificate
Certificate - is a file which contains owner's public key and other owner's info. This file is signed by Certificate Authority(CA) with digital signature - the entire certificate is converted to .der and hash sum is calculated
Subject - owner' data(from CSR)
Issuer - CA who issued a certificate
Serial Number - CA's unique identifier
Valid From/To
Public Key
Signature Algorithm
Signature Value
version
extension
//fingerprint - it is not a part of certificate, which is calculated by demand and can be used as unique identifier. It is a hash of the entire certificate in DER(.der) format
...
certificate authority(CA) certificate guarantees that you are who you are.
- Public certificate authority(CA)
- Private certificate authority(CA)
Self-signed certificate is a certificate which is not issued by certificate authority(CA) and where subject name is equals issuer name. Please note that Root certificate is self signed.
You are able to create Self-signed certificate on Mac:
Keychain Access -> Certificate Assistant -> Create a Certificate
mySelfSignedCertificate.pem
-----BEGIN CERTIFICATE-----
MIIDIjCCAgqgAwIBAgIBATANBgkqhkiG9w0BAQsFADAvMSAwHgYDVQQDDBdteVNl
bGZTaWduZWRDZXJ0aWZpY2F0ZTELMAkGA1UEBhMCVUEwHhcNMjMwMjE4MTMyOTIz
WhcNMjQwMjE4MTMyOTIzWjAvMSAwHgYDVQQDDBdteVNlbGZTaWduZWRDZXJ0aWZp
Y2F0ZTELMAkGA1UEBhMCVUEwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIB
AQDcMHHA0U2zk62XL698SdM2SmmZ6+sA0AsTb9MUx/tj3kNaOWBZEB82XGxoo09L
OlPgUJ94wMiLQ0JFYu4jDP6qb1ORUnIfI2SwuNQw61Xd+IpiP4hJG14KAGysUdc9
zEsA1PnWooLFdKDape/GdjSRGsr1vcTYBDWvjtYJrh0aXSGgWvo9zJ8snztqtRpJ
gn2JH0AR5RzJwdv8RYTGQdR5oQnUc8oaKCm2gCxWEmvdOkQyFoJQHw/kZgRKcMag
1wAofdDrESDINiih48r5cKqRD3R+y2MKlvVz0UoSAE5WqD1Oce4gnO90tpZv1ZlB
XxGAelLO8ZeZW+xG4wJad+XdAgMBAAGjSTBHMA4GA1UdDwEB/wQEAwIHgDAWBgNV
HSUBAf8EDDAKBggrBgEFBQcDAzAdBgNVHQ4EFgQUTTfu7fJusZPrR/mlhfFh7Xhd
2rEwDQYJKoZIhvcNAQELBQADggEBAMNZ10eVU7dGpok1JkYOwYcFamzFFdL5GVYj
xM5+mkI4G9BfFQxbutZFbiC44Fidp4fCp+ED7OAGErSBML5M4QBIwhic0ix/lAj6
LF6ZTJy9lwNGtgLTi7KM8kbIhJxzppeuzuaD1C+ttOgugAd99jRyBmkHInGBPNQ2
R4xbgYh7/pNiWmkjxMTYrN8rQqPYvhZy3XMoNTZ7OjOy6851TDFLlsHU8ocJqkhY
Jdar1j7k4GqEqe4cjLNfaqHzQQcvVOPEYo96+bzB6JlH0hQLHrBMrTuOv+EfLK1J
ONvvR94pEFKTO7Vg5F/lx5o0KPbDavNcgacAU4EDjxR3rUmMeos=
-----END CERTIFICATE-----
![]()
Verified certificate is a certificate which is a part of trusted certificate chains, where root certificate already was added in your keychain(trusted store)(by System, browser, you...)
Chain of trust (Certificate chain) - is a hierarchy of certificates to validate an issuer. Every certificate in this hierarchy is signed and issued by patent certificate
Root(trust anchor) Certificate - [Intermediate(subordinate, issuing) Certificate] - End-user(end-entity, leaf, subscriber) Certificate
- Root certificate - signs and issues only Intermediate certificates.
- Intermediate certificate - signs and issues other Intermediate certificate and End-user Certificate.
- End-user certificate - cannot sign and issue certificates.
[OpenSSL verify certificate chain]
Mac Keychain propose you next certificate validation options:
//System trust
This certificate is valid
//Manually added self-signed certificate and manually trusted
This certificate is masked as trusted for this account
//Manually added self-signed certificate
This certificate has not been verified by a third party
Validation/verification algorithm - Since child certificate is signed by parent(using parent's private key) and root certificate is self signed, and every child certificate has a link to it's parent(child's Issuer name equals to parent's Subject name) and root's certificate Issuer name equals to root's certificate Subject name. It means that the simplest way(without extensions and it's constraints) is just name matching. Don't forger that root certificate is usually pre-downloaded and intermediate and user-ended are usually downloaded during handshake
Charles Proxy uses self-signed certificate to sniff a traffic using Man-in-the-middle(MITM) proxy - Https ProxyServer
client - with added Charles Certificate and encrypt messages by Charles public key
Https ProxyServer - has Server's Certificate and proxy message and encrypt it by Server public key
Server
SSL Pinning is a mechanism when a client during handshake check/validate a retrieved certificate and compare it with local copy and fail the connection if it is not verified
[Certificate Signing Request(CSR)] - Info with a public key and other data which is send to CA
![enter image description here]()