Below is the error that I am getting on my console today as opposed to yesterday when the same code was working fine.
Error: SAML assertion not yet valid
at SAML.checkTimestampsValidityError
I have verified that I receive a success from the IDP and hence the application gets redirected to the '/home' endpoint in the URL which has been mentioned in the config file.
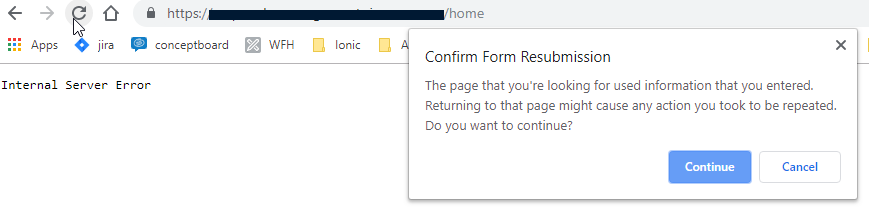
Additionally, when I submit the form, after an auto redirection [which shows me Internal Server Error]
I press refresh button of the browser and a form submission happens and the expected result is achieved.
My problem is, why doesn't this happens automatically or how and where can I do this submission programatically.
passport.js
const SamlStrategy = require('passport-saml').Strategy;
module.exports = function (passport, config) {
passport.serializeUser(function (user, done) {
done(null, user);
});
passport.deserializeUser(function (user, done) {
done(null, user);
});
passport.use(new SamlStrategy(
{
entryPoint: config.passport.saml.entryPoint,
issuer: config.passport.saml.issuer,
cert: config.passport.saml.cert,
path: config.passport.saml.path,
identifierFormat: config.passport.saml.identifierFormat
},
function (profile, done) {
debugger;
return done(null,
{
sessionIndex: profile.sessionIndex,
nameID: profile.nameID,
lastName: profile.lastName,
firstName: profile.firstName,
gid: profile.gid,
county: profile.county,
mail: profile.mail,
companyUnit: profile.companyUnit,
preferredLanguage: profile.preferredLanguage,
orgCode: profile.orgCode,
email: profile.email
});
})
);
};
config.js
module.exports = {
passport: {
strategy: 'saml',
saml: {
callbackUrl: '/home',
path: '/home',
entryPoint: 'https://.../GetAccess/Saml/IDP/SSO/Unsolicited?GA_SAML_SP=APP',
issuer: '...',
cert: '...',
identifierFormat: null
}
}
};
app.js
import express from 'express';
import helmet from 'helmet';
import cookieParser from 'cookie-parser';
import bodyparser from 'body-parser';
import path from 'path';
import logger from 'morgan';
import cors from 'cors';
import passport from 'passport';
import session from 'cookie-session';
const config = require('./config.js');
require('./passport')(passport, config);
var app = express();
app.use(logger('dev'));
app.use(cookieParser());
app.use(bodyparser.json());
app.use(bodyparser.urlencoded({ extended: false }));
app.use('/public', express.static(path.join(__dirname, '../public')));
app.use('/data', express.static(path.join(__dirname, '../uploads/')));
app.use(session(
{
resave: true,
saveUninitialized: true,
secret: 'secret value'
}));
app.use(passport.initialize());
app.use(passport.session());
app.use(helmet());
app.use(cors());
require('../router/routeConfig')(app, config, passport);
module.exports = app;
routeConfig.js
module.exports = function (app, config, passport) {
app.get('/', passport.authenticate(config.passport.strategy, {
successRedirect: '/home',
failureRedirect: 'https://.../GetAccess/Saml/IDP/SSO/Unsolicited?GA_SAML_SP=APP'
}));
app.get('/app', passport.authenticate(config.passport.strategy, {
successRedirect: '/home',
failureRedirect: 'https://.../GetAccess/Saml/IDP/SSO/Unsolicited?GA_SAML_SP=APP'
}));
app.post(config.passport.saml.path,
passport.authenticate(config.passport.strategy,
{
failureRedirect: 'https://.../GetAccess/Saml/IDP/SSO/Unsolicited?GA_SAML_SP=APP',
failureFlash: true
}),
function (req, res) {
debugger;
res.sendFile(path.join(__dirname, "../public/index.html"));
});
};