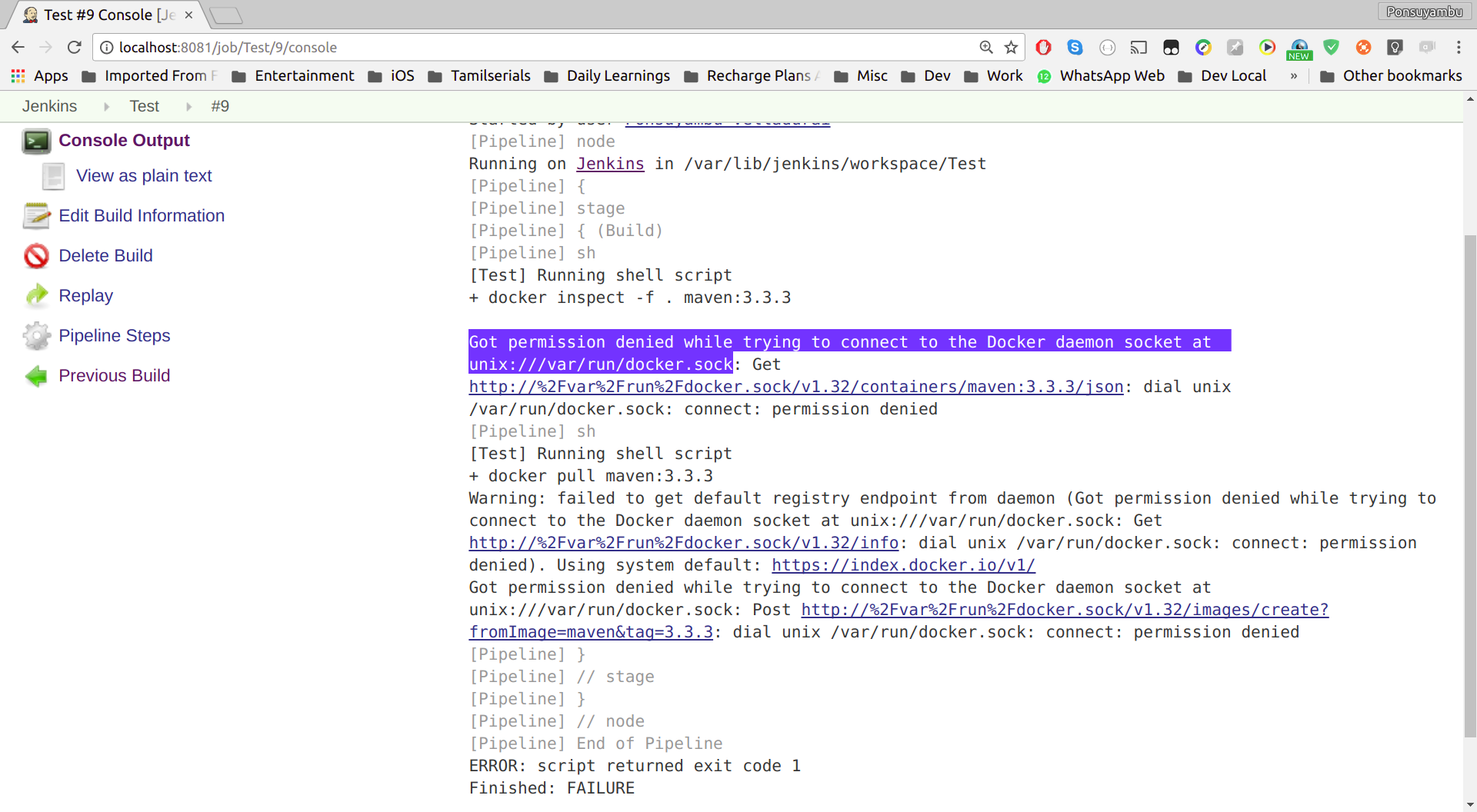
I faced a similar issue, which is a permission issue and the cause of this issue is because the Docker daemon/server always runs as the root user, and wants you to always preface the docker command with sudo.
Docker daemon binds to a Unix socket instead of a TCP port. By default that Unix socket is owned by the user root and other users can only access it using sudo.
To fix this, here's what worked for me:
Firstly, check if you have a docker group already created:
cat /etc/group
If you don't find docker in the list that is displayed, then you will need to create one:
sudo groupadd docker
Next, confirm your user and your group using the command below:
cat /etc/group
Scroll through to see the group for docker. It should be of this format
docker:x:140:promisepreston
where docker is my group and promisepreston is my user
Now we can add your user to the docker group
Also add your user to the “docker” group, If you would like to use Docker as a non-root user:
Copy and run the command below in your terminal exactly how it is stated without modifying it in any way, regardless of the docker image/container/command that you want to run or are trying to run or is causing the permission issue:
sudo usermod -aG docker $USER
After running the command above, you will need to Log out and log back in so that your group membership is re-evaluated. However, on Linux, you can also run the following command below to activate the changes to groups (Copy and run the command below in your terminal exactly how it is stated without modifying it in any way, regardless of the docker image/container/command that you want to run or are trying to run or is causing the permission issue):
newgrp docker
OR
sudo systemctl restart docker
You can now verify that you can run docker commands without sudo permissions, by running the command that is causing the permissions issue again, say (Replace my-command with the name of your image/container/command):
docker run my-command
For Docker and Local filesystem files:
If you have a copy of the files on your local filesystem, then you can change the ownership of the application directory where the application files are stored, using this format:
sudo chown your_user:your_group -R my-app-directory/
So in my case it will be:
sudo chown promisepreston:docker -R my-app-directory/
Note: Please run this command inside the parent directory housing the application directory.
That's all.
I hope this helps