I was checking out different keyloggers for research purposes and stumbled upon Refog:
https://www.refog.com/keylogger/
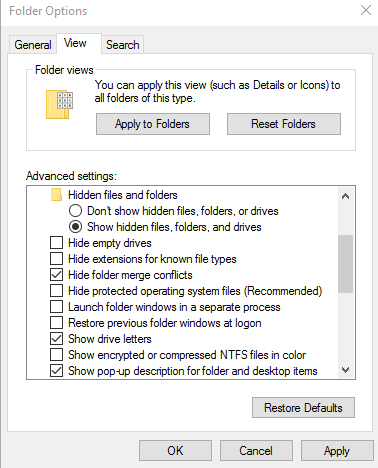
This program could catch a lot of system events, but what really caught my attention was something else. The program created a hidden folder called Mpk, path C:\Windows\SysWOW64\Mpk. It was marked as an operating system files folder, because it was not visible until I unmarked Hide protected operating system files (recommended). This, I guess, can be done via the attrib command like this attrib +s +h "C:\Windows\SysWOW64\Mpk" so nothing revolutionary.
However they also added an exclusion to Windows Defender for this folder. How can they do this programmatically? I'm running Windows 10 Pro x64.

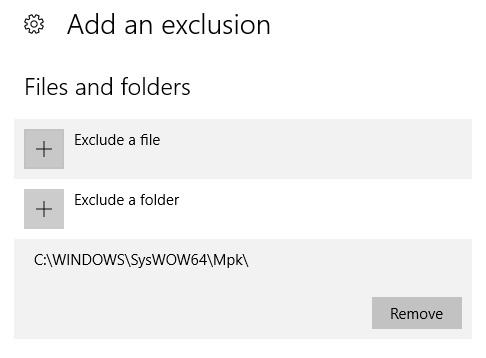
powershell -inputformat none -outputformat none -NonInteractive -Command "Add-MpPreference -ExclusionPath 'C:\Program Files (x86)\sysconfig'"– Cammack