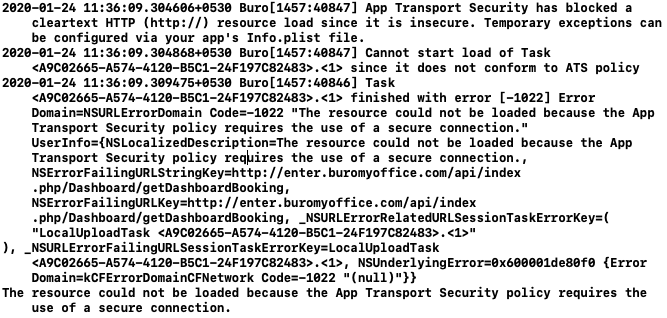
For those of you who want a more context on why this is happening, in addition to how to fix it, then read below.
With the introduction of iOS 9, to improve the security of connections between an app and web services, secure connections between an app and its web service must follow best practices. The best practices behavior is enforced by the App Transport Security to:
- prevent accidental disclosure, and
- provide a default behavior that is secure.
As explained in the App Transport Security Technote, when communicating with your web service, App Transport Security now has the following requirements and behavior:
- The server must support at least Transport Layer Security (TLS) protocol version 1.2.
- Connection ciphers are limited to those that provide forward secrecy (see the list of ciphers below.)
- Certificates must be signed using a SHA256 or better signature hash algorithm, with either a 2048 bit or greater RSA key or a 256 bit or
greater Elliptic-Curve (ECC) key.
- Invalid certificates result in a hard failure and no connection.
In other words, your web service request should: a.) use HTTPS and b.) be encrypted using TLS v1.2 with forward secrecy.
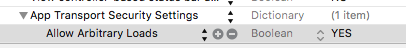
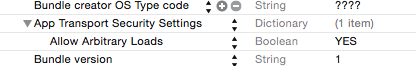
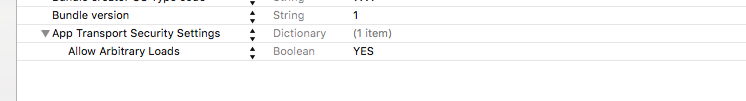
However, as was mentioned in other posts, you can override this new behavior from App Transport Security by specifying the insecure domain in the Info.plist of your app.
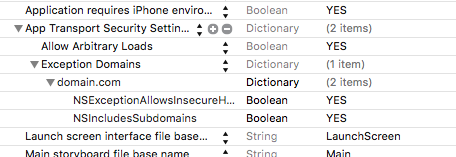
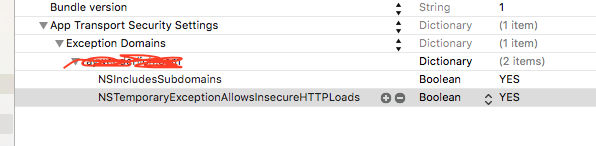
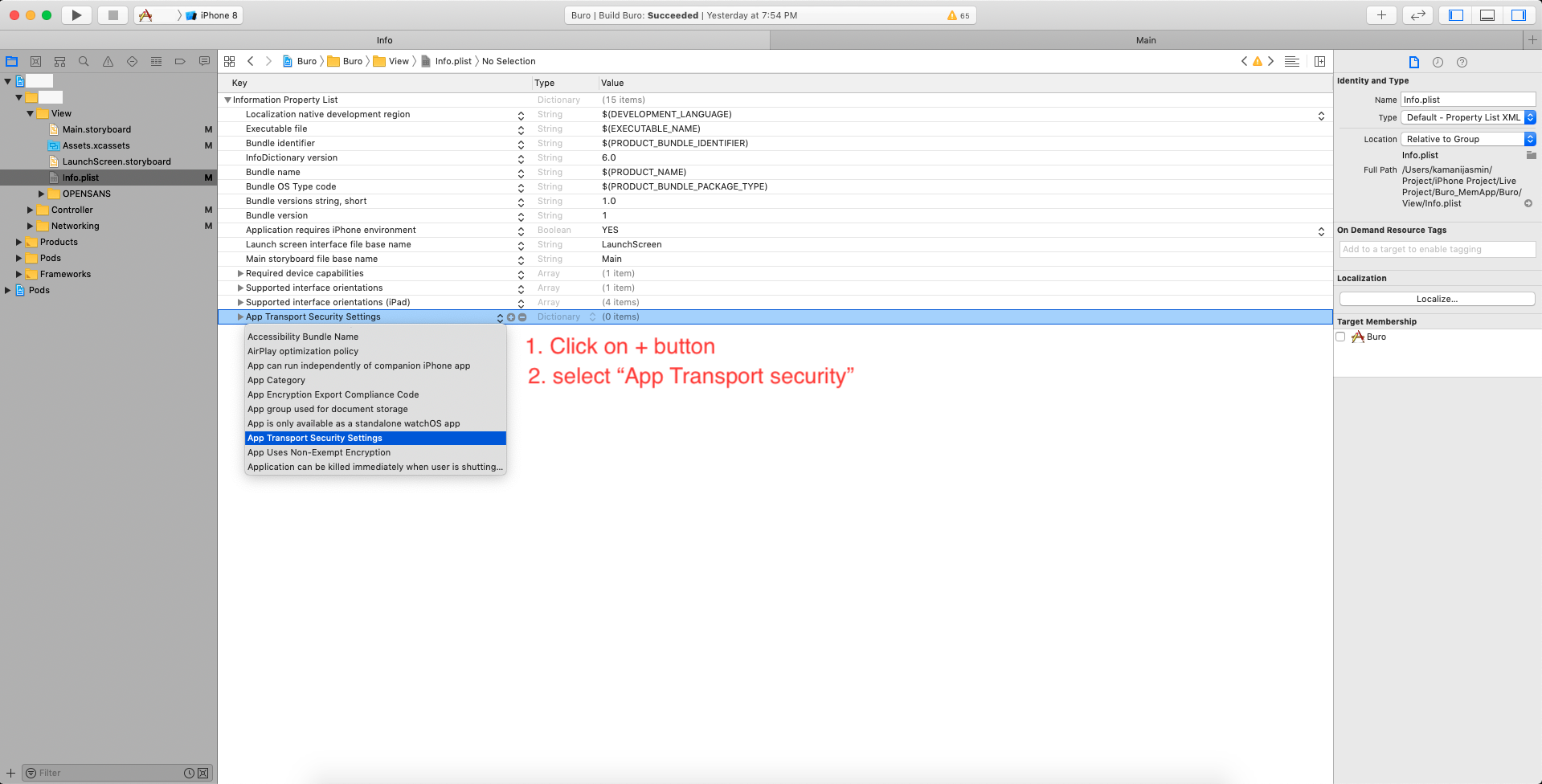
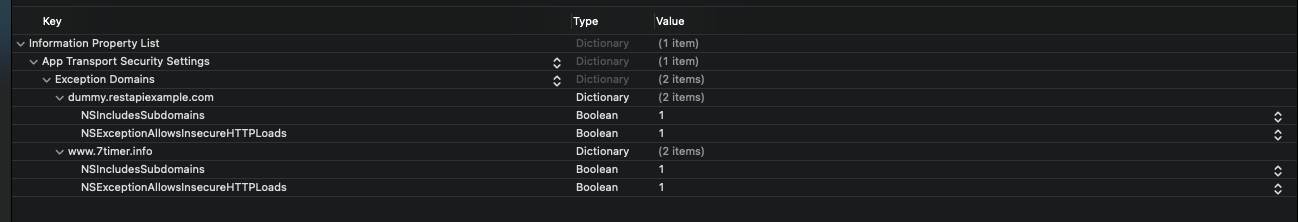
To override, you will need to add the NSAppTransportSecurity > NSExceptionDomains dictionary properties to your Info.plist. Next, you will add your web service's domain to the NSExceptionDomains dictionary.
For example, if I want to bypass the App Transport Security behavior for a web service on the host www.yourwebservicehost.com then I would do the following:
Open your app in Xcode.
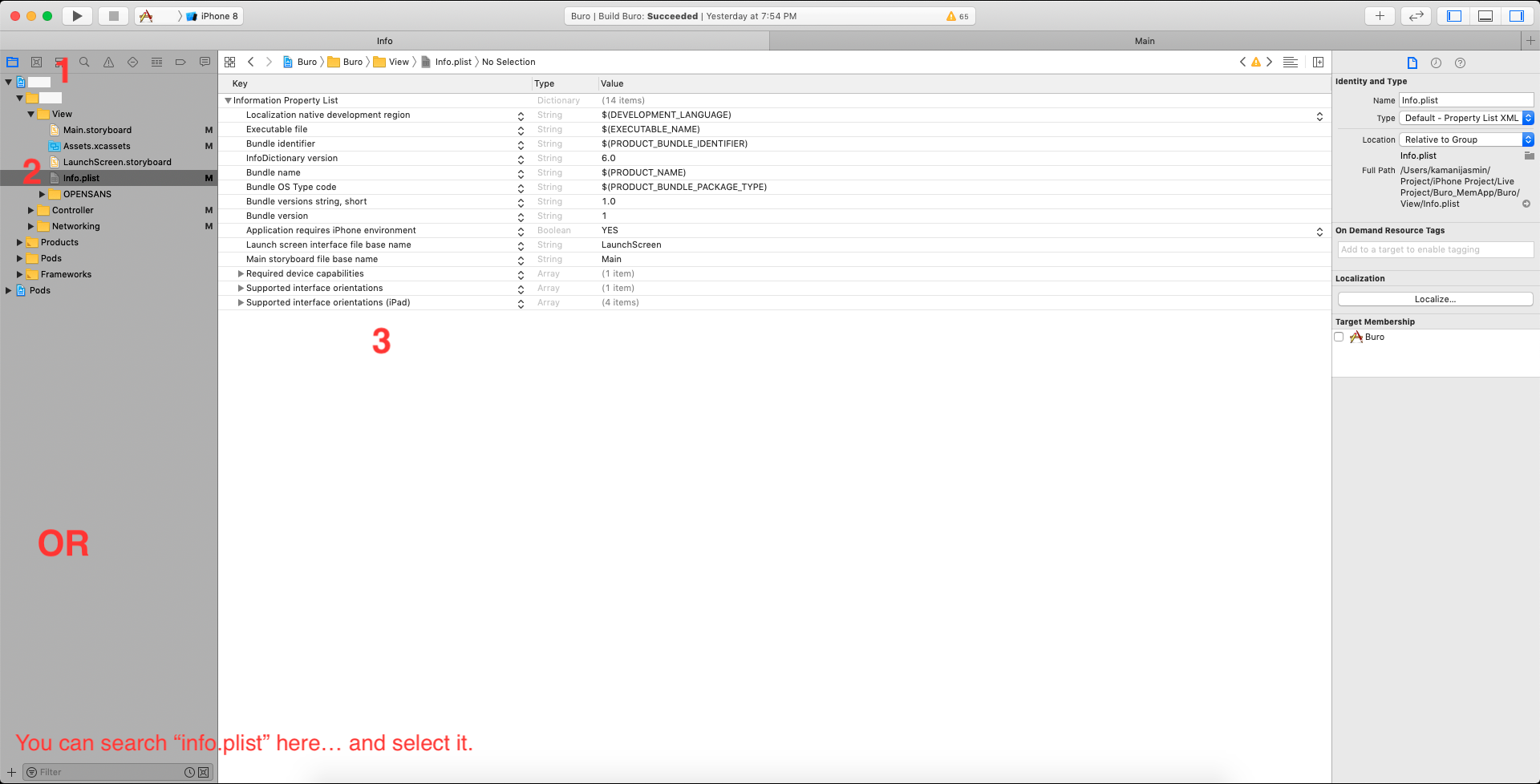
Find the Info.plist file in Project Navigator and "right-mouse" click on it and choose the Open As > Source Code menu option. The property list file will appear in the right pane.
Put the following properties block inside of the main properties dictionary (under the first <dict>).
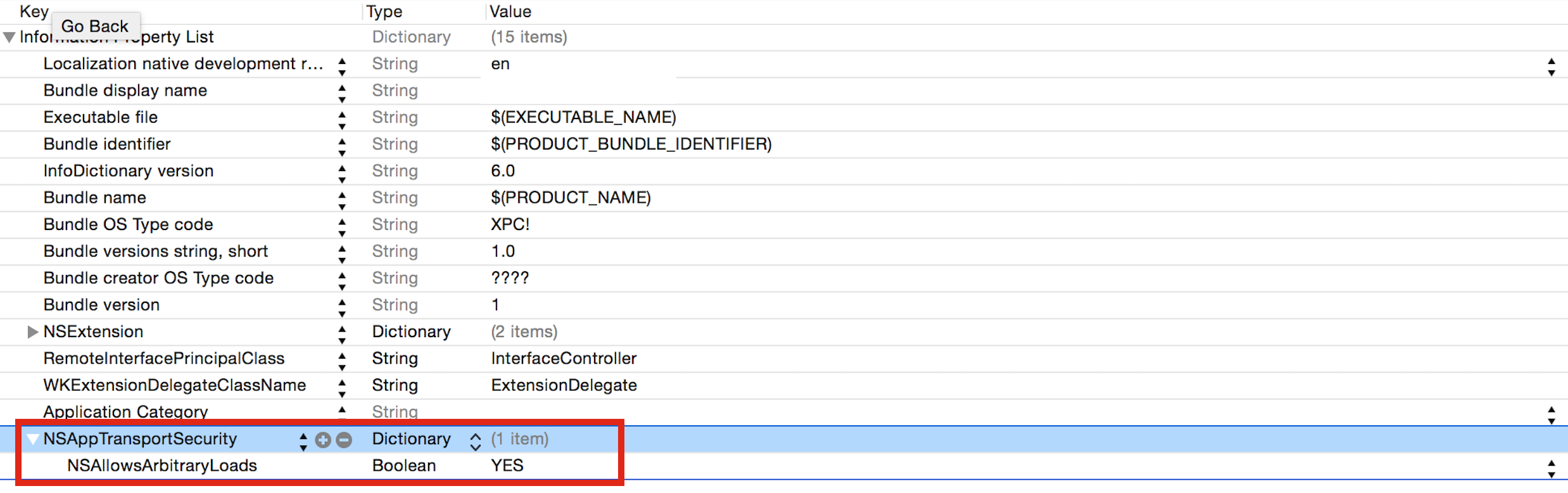
<key>NSAppTransportSecurity</key>
<dict>
<key>NSExceptionDomains</key>
<dict>
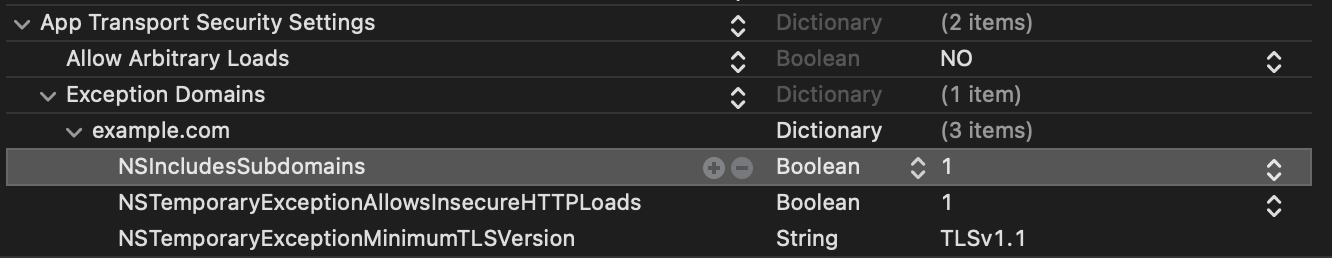
<key>www.example.com</key>
<dict>
<key>NSExceptionAllowsInsecureHTTPLoads</key>
<true/>
<key>NSExceptionMinimumTLSVersion</key>
<string>TLSv1.1</string>
<key>NSIncludesSubdomains</key>
<true/>
</dict>
</dict>
</dict>
If you need to provide exceptions for additional domains then you would add another dictionary property beneath NSExceptionDomains.
To find out more about the keys referenced above, read this already mentioned technote.









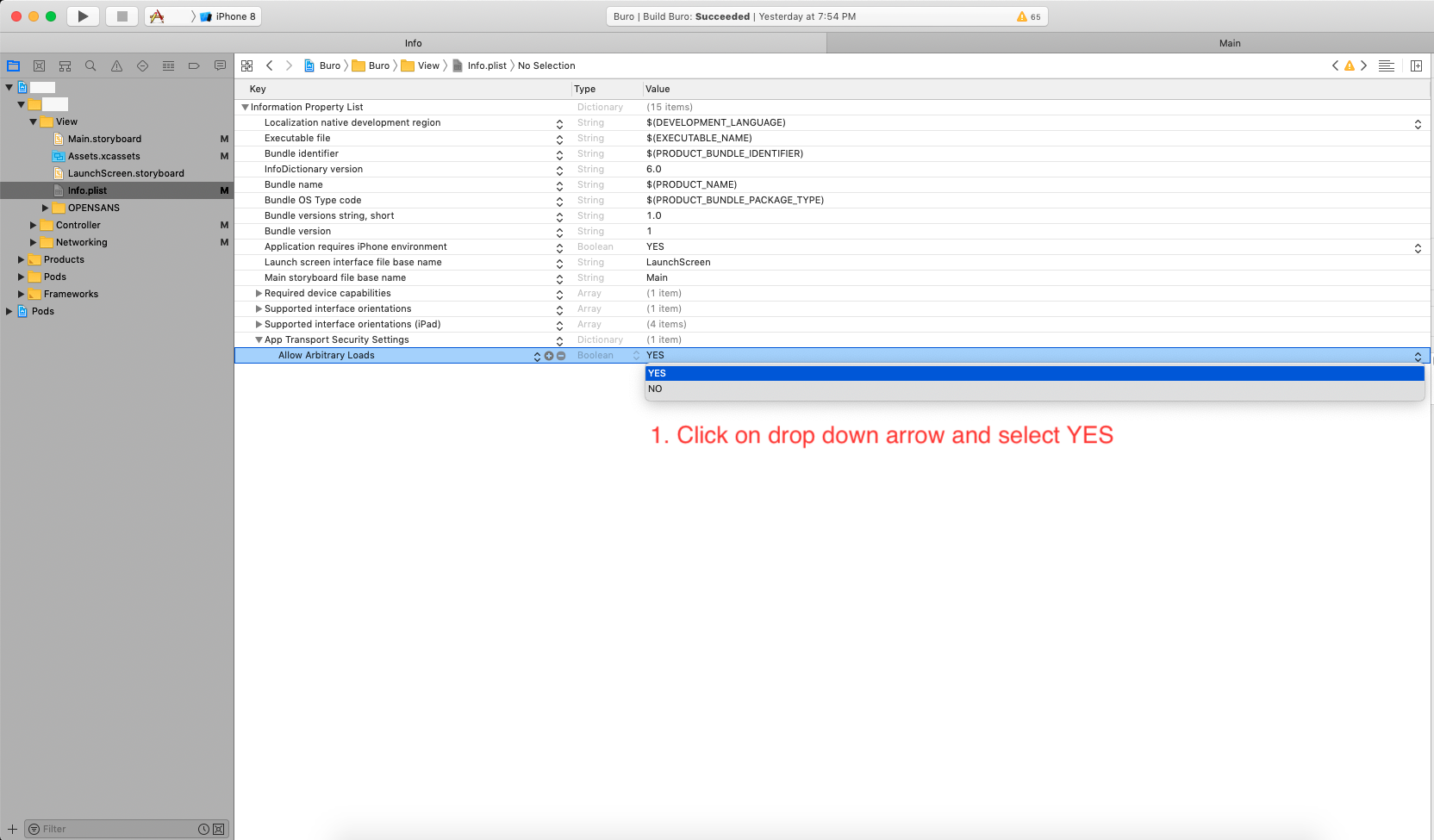
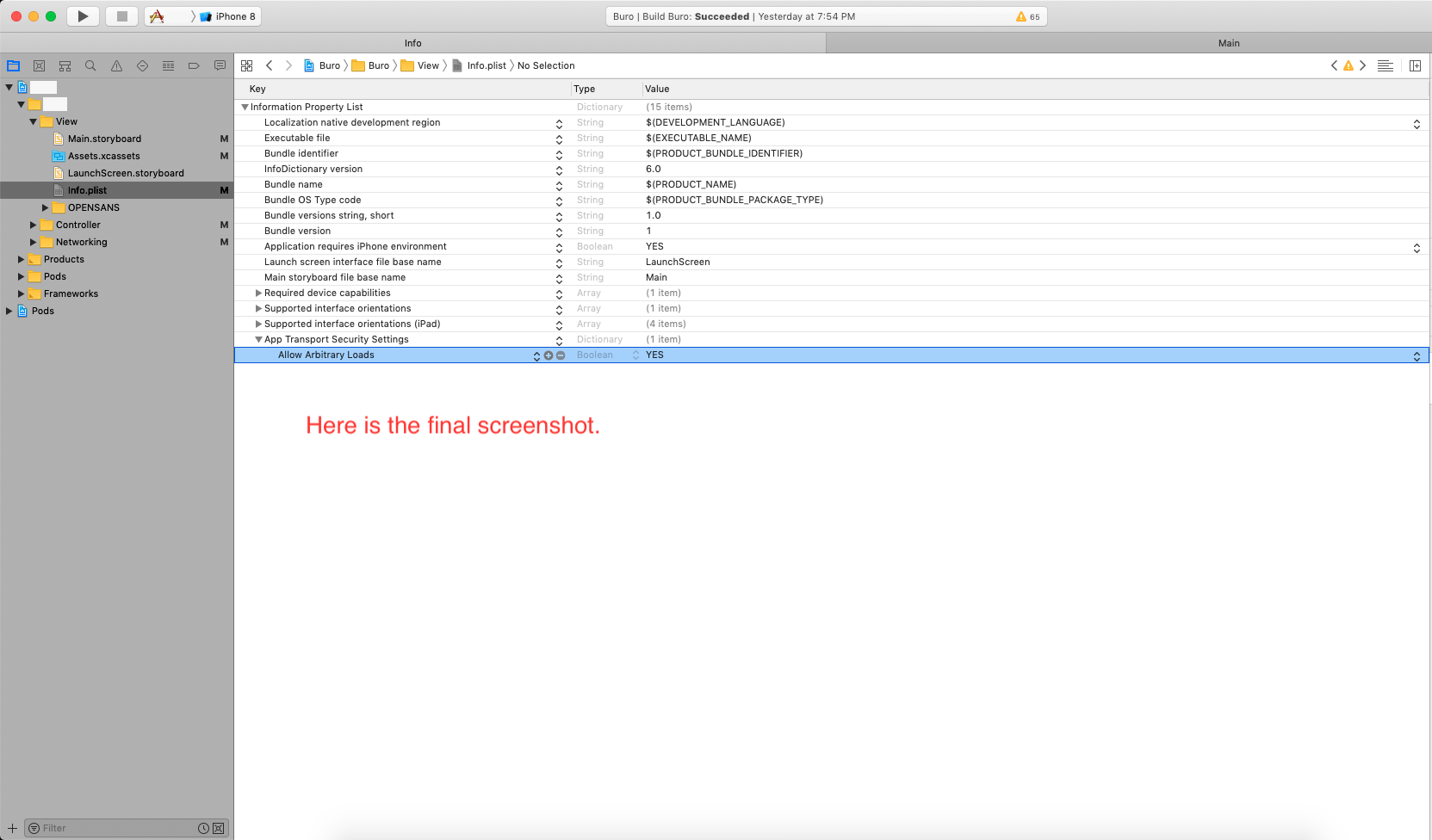
![sandbox settings]](https://static.mcmap.net/file/mcmap/ZG-AbGLDKwfpKnMAWVMrKmltX1ywKmMva3/jlgoZ.png)

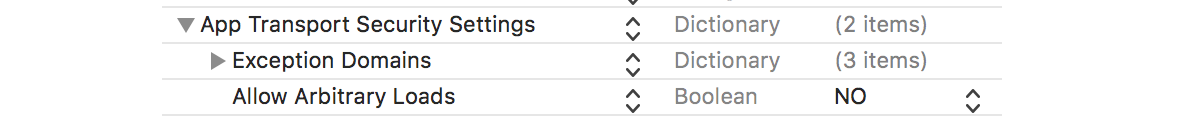
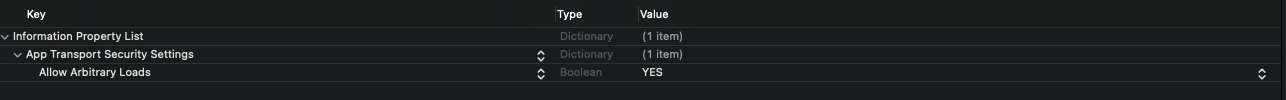

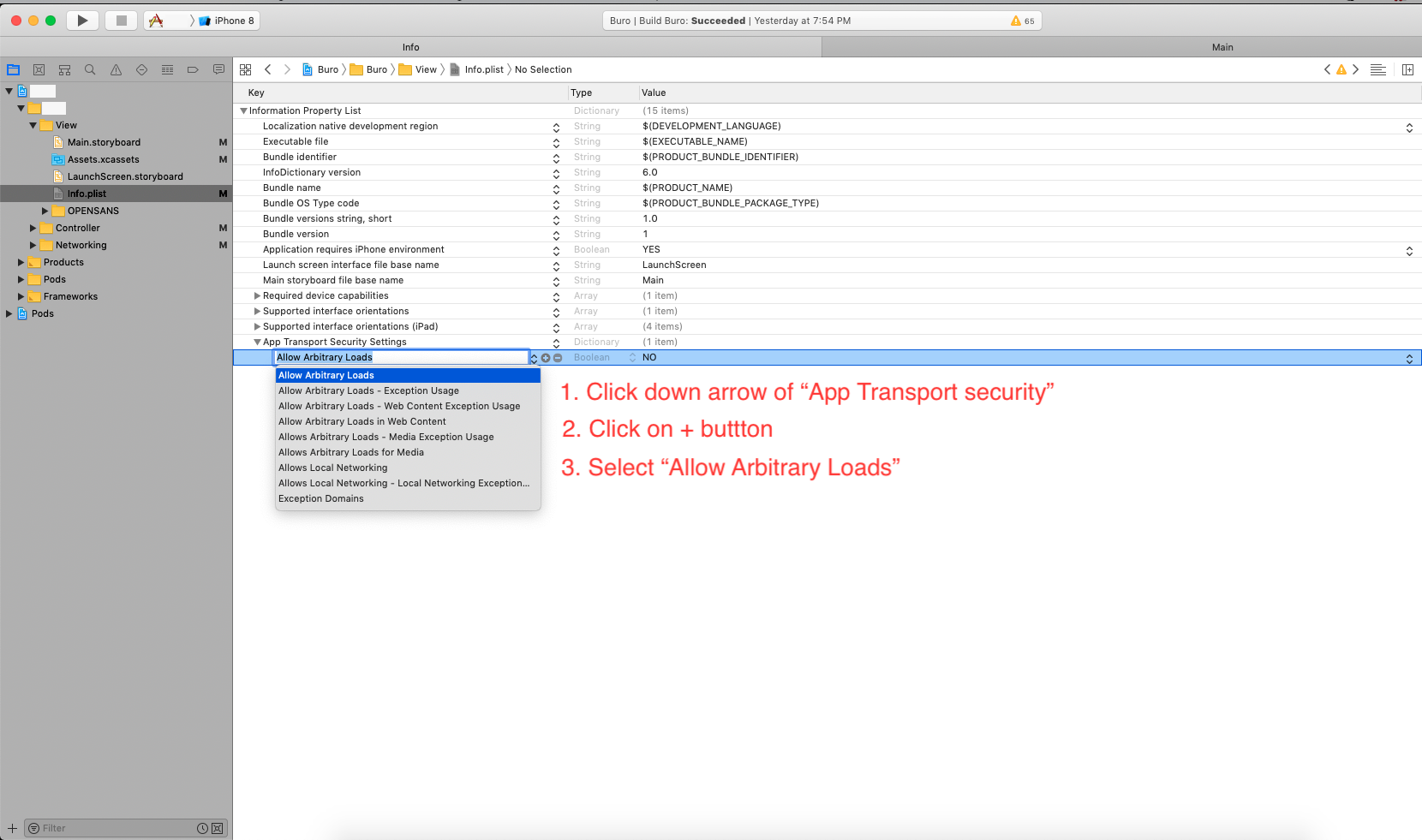
Allow arbitary loads). Soon this won't be possible since Apple will require ATS (Originally the end of the year - deadline has been extended) - developer.apple.com/news/?id=12212016b – Marden