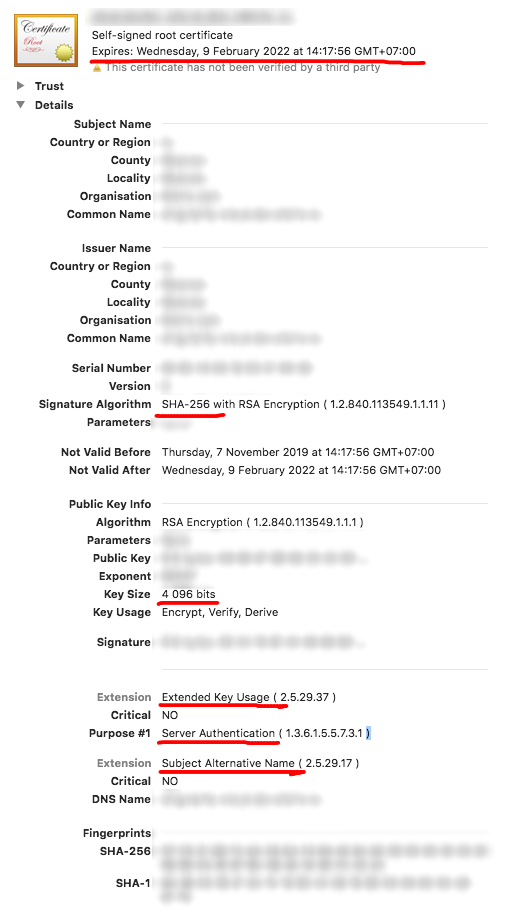
I have installed iOS 13 beta version and run my framework which contains a lot of network requests, but I got this error:
2019-09-19 15:01:33.566811+0200 ---[395:25439] Connection 4: default TLS Trust evaluation failed(-9814)
2019-09-19 15:01:33.567022+0200 ---[395:25439] Connection 4: TLS Trust encountered error 3:-9814
2019-09-19 15:01:33.567110+0200 ---[395:25439] Connection 4: encountered error(3:-9814)
2019-09-19 15:01:33.569824+0200 ---[395:25439] Connection 4: unable to determine interface type without an established connection
2019-09-19 15:01:33.584952+0200 ---[395:25439] Task <D97FD611-0B48-4DCE-99C9-6A971E5E6524>.<4> HTTP load failed, 0/0 bytes (error code: -1202 [3:-9814])
I tried to find out what cause that problem with no success. Can anyone help me?