I'm trying to setup a scheduled task with ECS Fargate but I cannot figure out why it is not running. I can confirm the task works correctly using RunTask but when I try to trigger it on a schedule all I get is a bunch of 'FailedInvocations' with no explanation.
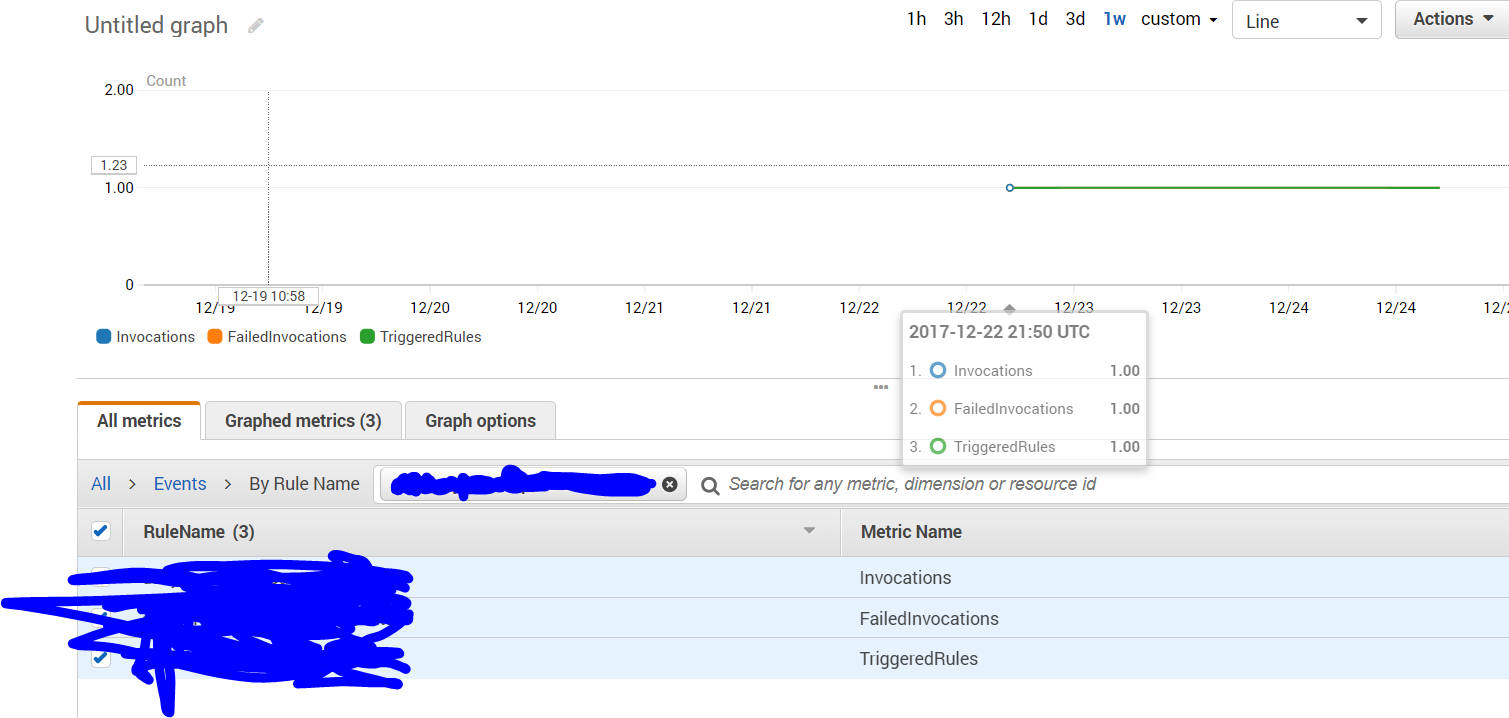
I do know though that the rule is being triggered so this is a good sign. See the screenshot below:
But everytime it is triggered there is just a 'FailedInvocation'. Here's the scheduling rule:
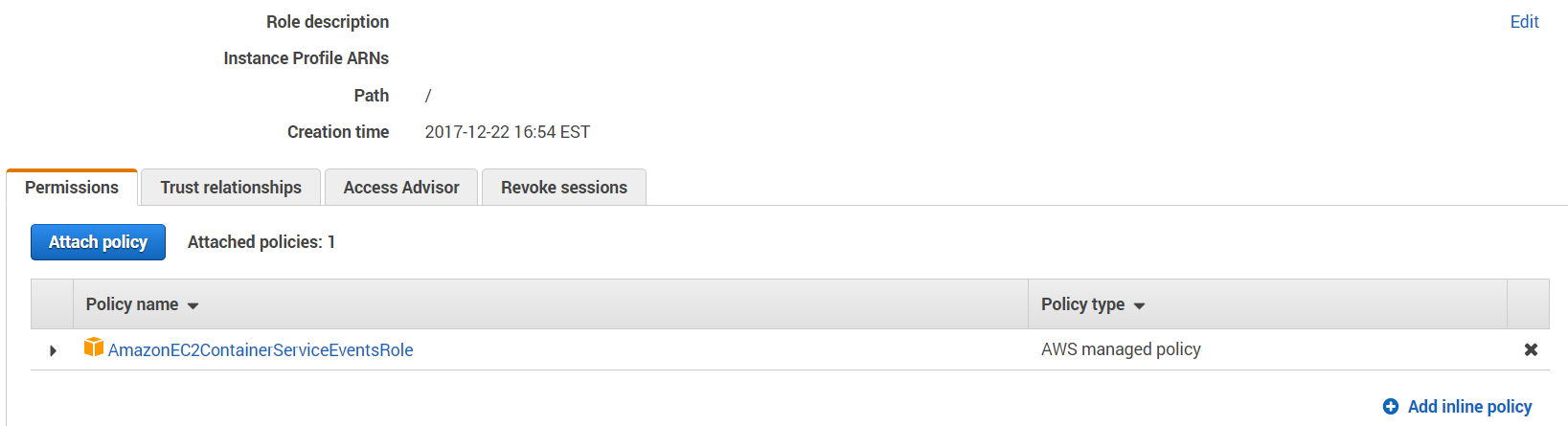
And the default permissions on the ecsEventRole with just ecs:runTask:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ecs:RunTask"
],
"Resource": [
"*"
]
}
]
}
My hunch says that this ecsEventsRole doesn't have enough permissions. Should I try to give it the ones that ecsTaskExecutionRole has?
Thanks
EDIT: This is now supported in us-east-1 region. See comments.