This happens because personal accounts cannot manage administrative permissions, Microsoft has determined that personal accounts are not administrators:
To allow users to request an administrator's review and approval of an application that the user isn't allowed to consent to, enable the admin consent workflow. For example, you might do this when user consent has been disabled or when an application is requesting permissions that the user isn't allowed to grant.
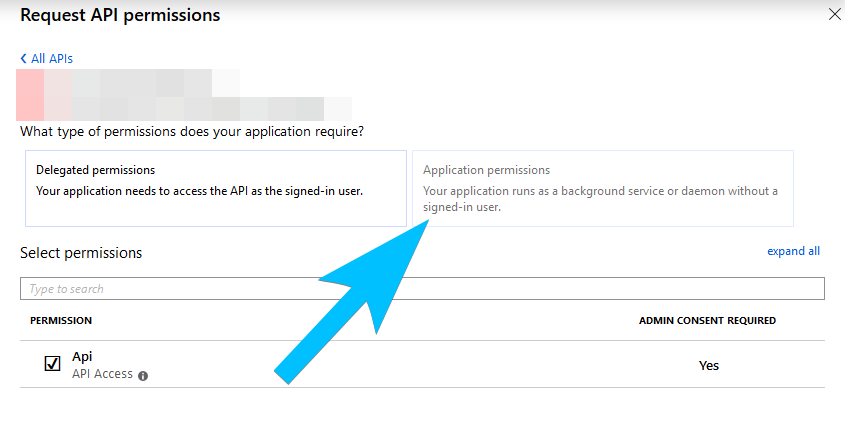
Apps that sign in to personal Microsoft accounts do not support permissions that require administrator consent.
By example: Directory.ReadWrite.All require administration consentimient. Alll application permissions need administration consentimients. Only the basic permissions are enabled for a personal account.
If you try add the permission in the manifest like as:
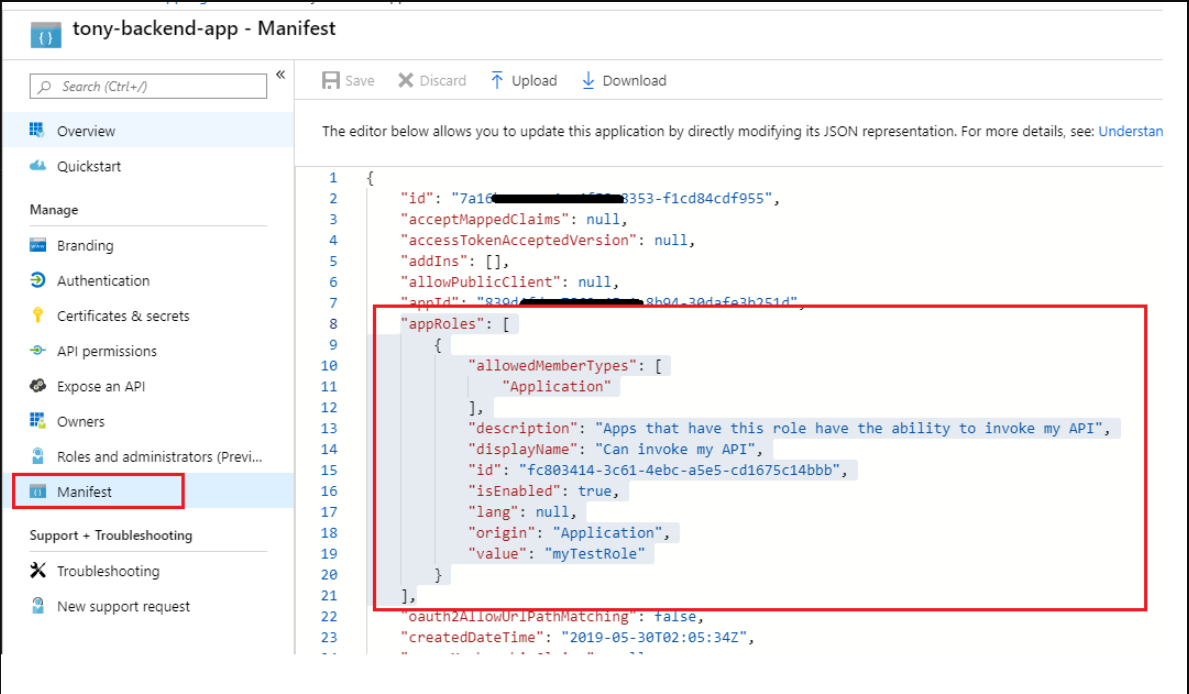
"appRoles": [
{ "allowedMemberTypes": [ "Application" ],
...
Says:
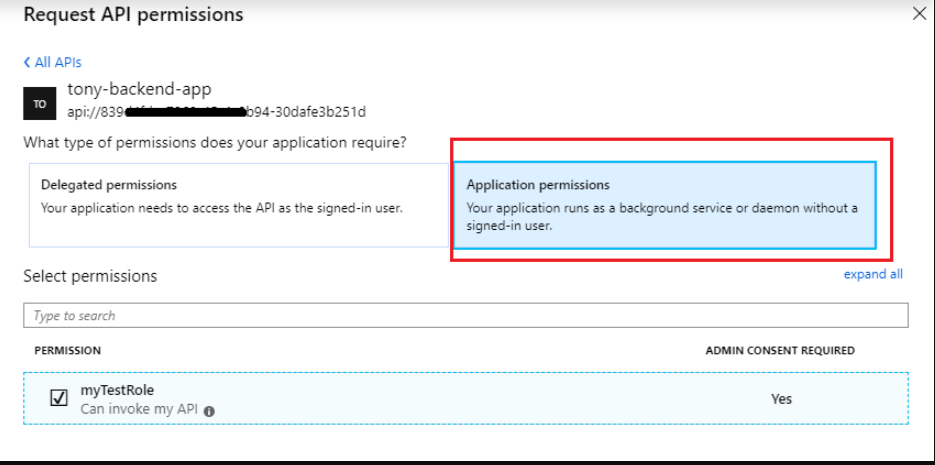
The signInAudience property is set to PersonalMicrosoftAccounts and application permissions or app roles cannot be exposed for applications that only support personal Microsoft accounts.
When you try modify the permissions from Permission Manager menu says:
interaction_required: AADSTS16000: User account '{EUII Hidden}' from identity provider 'live.com' does not exist in tenant 'Microsoft Services' and cannot access the application '7655d621-3c86-4a9a-92f8-47244f293b55'(Microsoft_Entra_PM) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account.
But for add other users you need administration roles, but for administration roles you need a organization, but to create a organization with administration roles need a enterprise account.
If you try modify the identification type in the Identification section, says:
failedAdminServiceApiCall 0 undefined
Error code: failedAdminServiceApiCall
In other words, you must pay for a Microsoft Azure enterprise account, have an Active Directory, and be an administrator of an organization with a paid plan to enable this option.
If you can't, you have more options, such as using the Google Drive API, it gives you full access without the need to have a paid account, but with certain limits on access use, but as long as you don't make hundreds of thousands of requests a day no problem.