The https://jwt.io debugger works in both directions, you can inspect and verify tokens or create and sign tokens.
Esp. when you have a token signed with a symmetric algorithm (i.e. HS256, HS384, or HS512), you can easily get a false verification because there's only one key for signing and verifying the token.
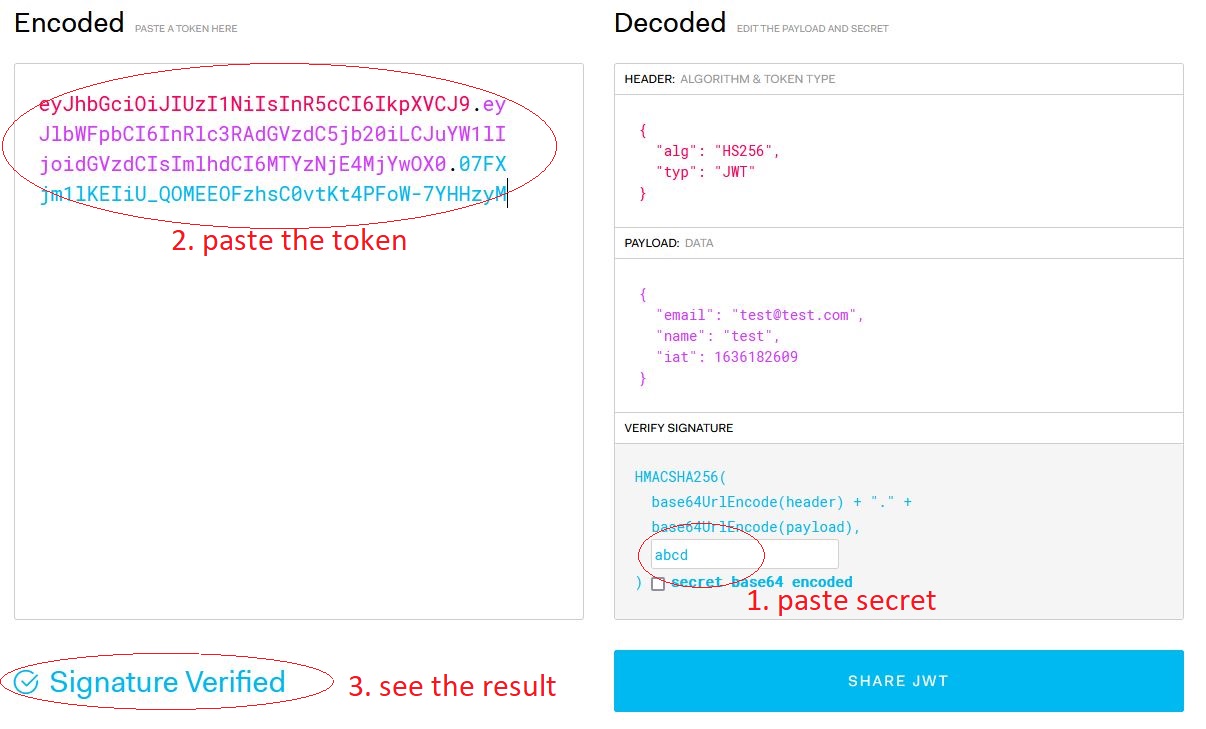
When you first paste your token on the left side and then paste the secret or key into the field under 'verify signature' in the right column, the signature will be recreated and it might change if the secret is not the one that was used to create the original token. In this case, the result is always 'signature verified', because the signature was just calculated based on the entered secret.
The correct way to verify a signature is to first paste the key into the secret key field and then paste the token to the left part of the debugger. Always make sure, that any other content in the input fields is overwritten. If your key is actually Base64 encoded (i.e. a binary secret that is stored in Base64 encoded form), you should tell jwt.io by checking the "secret base64 encoded" checkbox.
![enter image description here]()
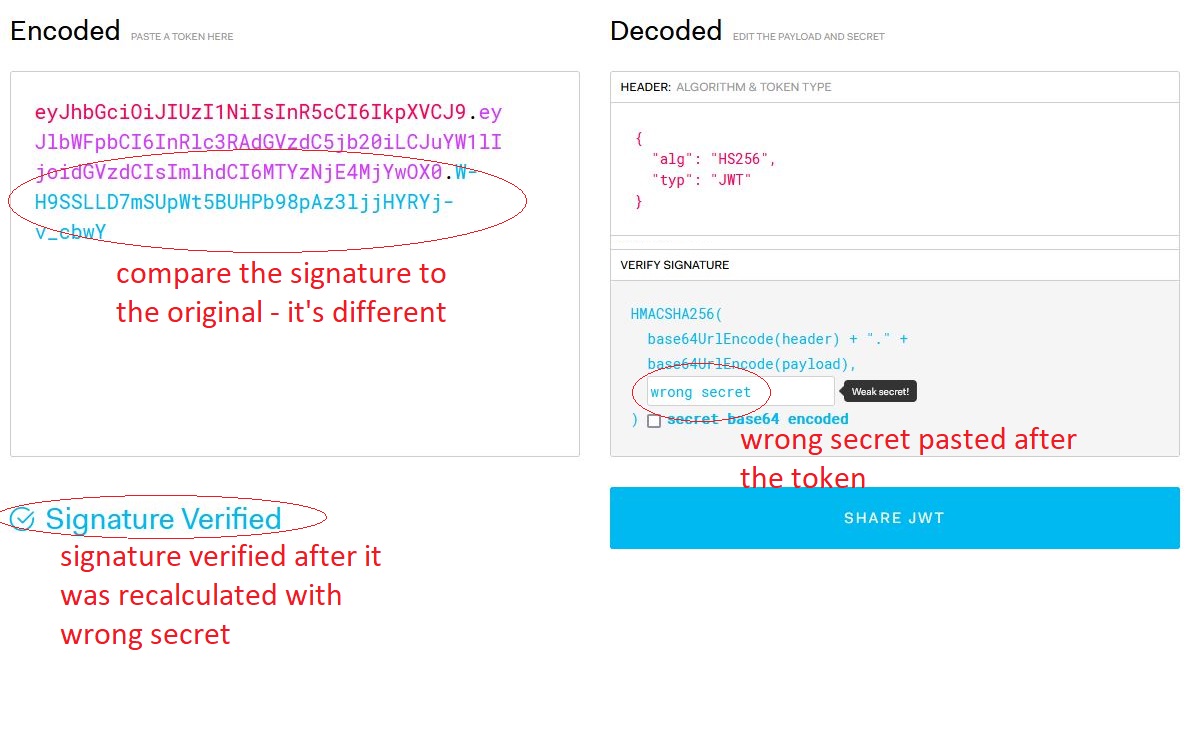
Then the result, either 'signature' verified' or 'invalid signature', will be correct.
Every secret that you enter after that causes a recalculation of the signature and then it's always verified (with the new secret). Also clicking on the "secret bas64 encoded" checkbox causes recalculation.
![enter image description here]()
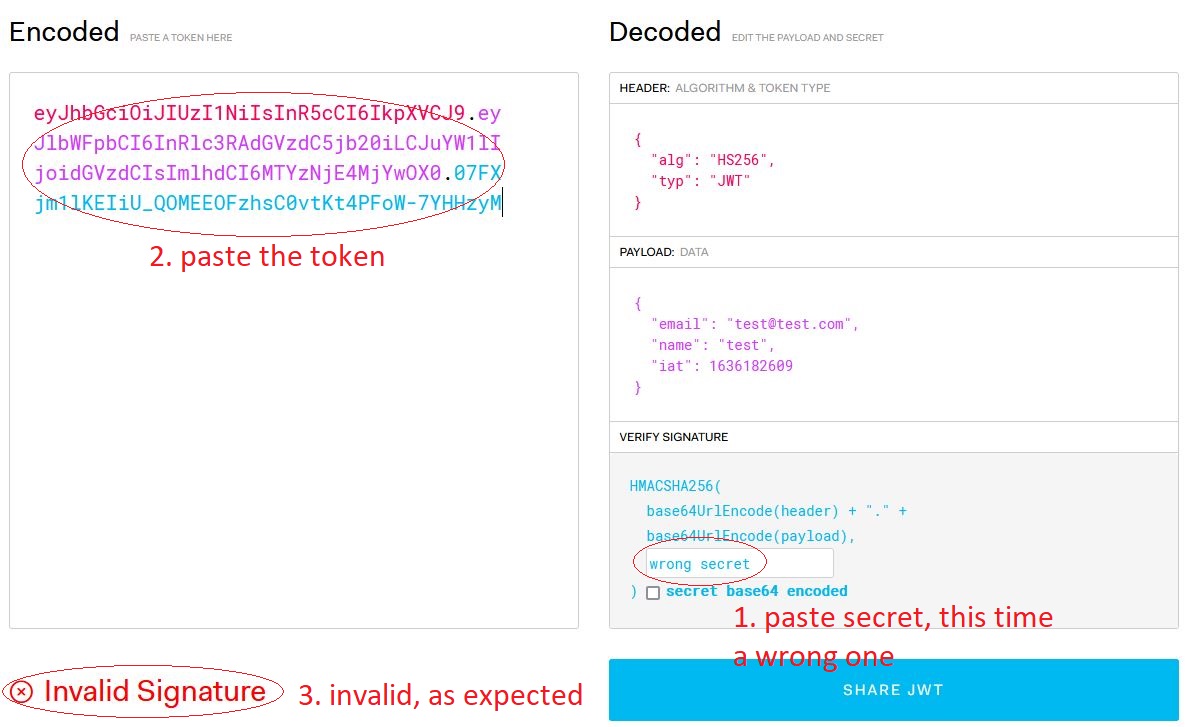
But if you do it in the right order, a wrong secret causes an "invalid signature" result:
![enter image description here]()