I am receiving a failure while trying to download blob (JSON file) from Azure storage account from my Azure Automation account. It looks like an authorization issue.
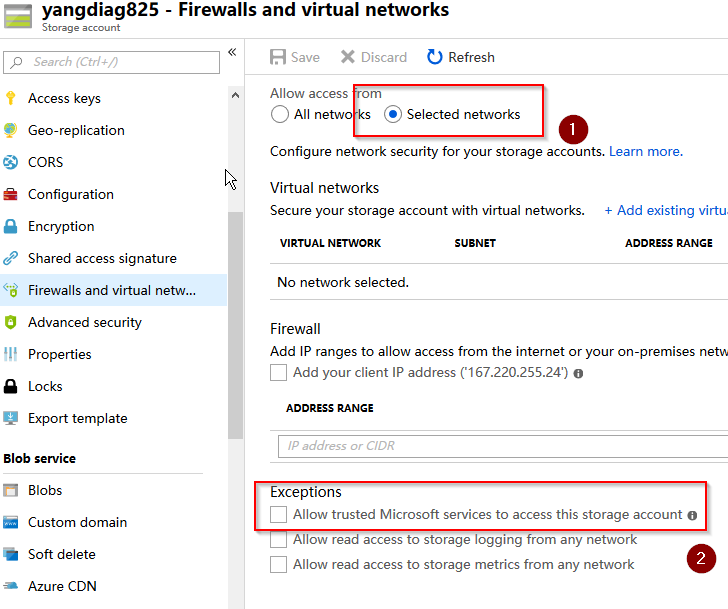
This works on my local laptop, but does not work on Azure Automation Account. Does not work even if I make the container "public"
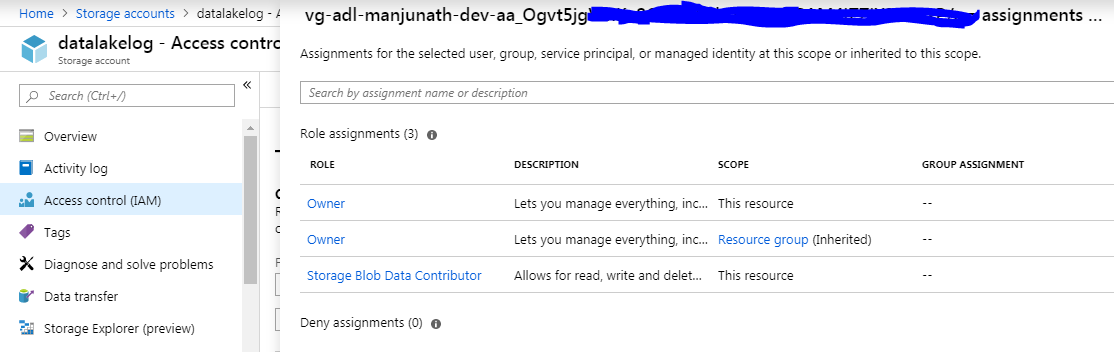
I have assigned OWNER privileges for the Automation accounts's service principle on the Resource Group (Automation account + Storage account stay in this RG) and specifically on the Storage Account as well:
Below is the code:
$connectionName = "AzureRunAsConnection"
try
{
# Get the connection "AzureRunAsConnection "
$servicePrincipalConnection=Get-AutomationConnection -Name $connectionName
"Logging in to Azure..."
Add-AzureRmAccount `
-ServicePrincipal `
-TenantId $servicePrincipalConnection.TenantId `
-ApplicationId $servicePrincipalConnection.ApplicationId `
-CertificateThumbprint $servicePrincipalConnection.CertificateThumbprint
}
catch {
if (!$servicePrincipalConnection)
{
$ErrorMessage = "Connection $connectionName not found."
throw $ErrorMessage
} else{
Write-Error -Message $_.Exception
throw $_.Exception
}
}
$config_file_resource_group_name = "vg-datalake-manjunath"
$config_file_storage_account_name = "datalakelog"
$primary_key = (Get-AzureRmStorageAccountKey -ResourceGroupName $config_file_resource_group_name -AccountName $config_file_storage_account_name).value[0]
$config_file_context = New-AzureStorageContext -StorageAccountName $config_file_storage_account_name -StorageAccountKey $primary_key
Get-AzureStorageBlobContent -Blob "mw_services.json" -Container "fwconfigfiles" -Destination "C:\temp\mw_services.json" -Context $config_file_context
get-content "C:\temp\mw_services.json" | write-output
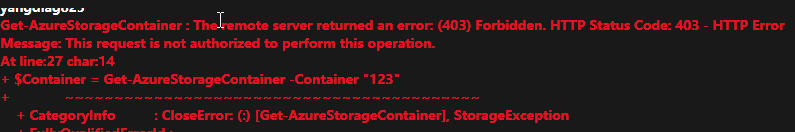
ERROR:
Get-AzureStorageBlobContent : The remote server returned an error: (403) Forbidden. HTTP Status Code: 403 - HTTP Error
Message: This request is not authorized to perform this operation.
At line:30 char:2
+ Get-AzureStorageBlobContent -Blob "mw_services.json" -Container "fwc ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : CloseError: (:) [Get-AzureStorageBlobContent], StorageException
+ FullyQualifiedErrorId :
StorageException,Microsoft.WindowsAzure.Commands.Storage.Blob.Cmdlet.GetAzureStorageBlobContentCommand