Basic Facts:
$algorithm = MCRYPT_BLOWFISH;
$mode = MCRYPT_MODE_CBC;
$randSource = MCRYPT_DEV_URANDOM;
Note This is not a strict coding question.
Context:
CentOS 7, Apache 2.4.12, & PHP 5.6.20.
I am making an HTML email with a "verify your email address" link that allows a registration process to complete. Everything on my virtual private server is UTF-8, and all form and query string input is processed with multi-byte (mb) funcions.
Background
As an experiment (I know about the age and state of the mcrypt library), I am attempting to decrypt Blowfish encrypted query string parameters. Assume that on the way up, the encryption sequence works perfectly and I am receiving email with the link.
On the way down, the hmac_hash() signing (SHA-512, just for this experiment) is working and I am able to separate each independent message (32 characters) from its hash checksum (128 characters). Base64 decoding of the separated message portion is working. For each parameter, I am left with the composite cipher text, where composite cipher text equals the IV + base cipher text. Assume I use a version of substr() to obtain the IV and the base cipher text independently (which is par for the course).
Problem
PHP: Warning mcrypt_generic_init(): Iv size is incorrect; supplied length: 12, needed: 8
Assume I have combed the PHP manual and Stackoverflow. Assume I have looked at other questions similar, but not exactly like this one. Assume I have searched the Internet to no avail. Assume I have enough experience to setup mb_string properly. Assume that I will take care of mcrypt padding when I get past this current problem.
Could multi-byte issues be interfering with decryption?
Could base64 encoding the IV + base cipher text corrupt the IV?
Could base64 padding be an issue?
Should I be specifying a more specific MCRYPT_BLOWFISH_*?
Why does the blowfish IV size report 8 bytes, but rarely produces an 8 byte IV?
Which substr() should I use, substr() or mb_substr(), for a setup that leans towards making everything UTF-8 and processes all other input as multi-byte UTF-8. I know that is an odd question, but all of the PHP Manual mycrypt decryption sequence examples use substr(), and none use mb_substr(). Everything on my site works with mb_functions when possible, and I would not mind using substr() if it solved my problem, but it does not solve it. When I use mb_substr(), I get the following warning.
PHP: Warning mcrypt_generic_init(): Iv size is incorrect; supplied length: 11, needed: 8
Does anyone have any experience with this exact issue? Constructive answers will be rewarded!
Latest
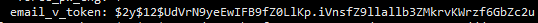
Above is an example Blowfish hash that I am trying to reconstruct from an array, received via a SHA512 HMACed, symmetricly Blowfish encrypted (CBC), url safe Base64 encoded, urlencoded, query string (phew!).
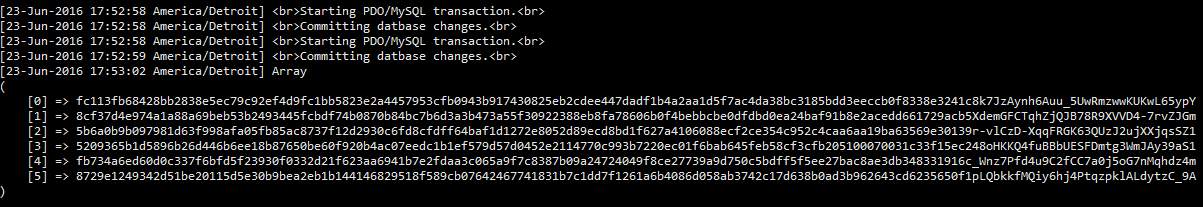
Below, is what the strings for the query string (having chopped up the blowfish hash above) look like after encrypting, signing, and base64 encoding, but before being urlencoded. Each one is 128 characters long (each string gets longer as you do more stuff).
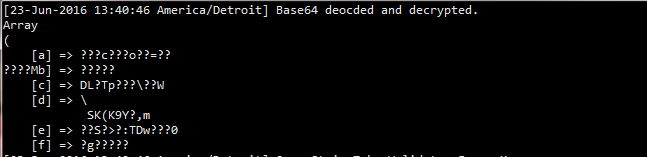
Above is the Base64 decoded and Blowfish decrypted array derived from the query string (Obviously, there are security steps in between this result, but I am just trying to show the latest state of things.) Something is not right. Encryption appears to work without any errors. Decryption does not produce any errors either. The plain text is just wrong. If I join/implode these elements, they will not be like the Blowfish hash above.

filter_input_array(INPUT_GET)) on a link in email (where all inputs are assured to be UTF-8 via mb string functions in my filter framework, not ISO-8859-1), automatically urldecoded by PHP, separted from the HMAC, base64_decoded, and recovered from the composite cipher text. – Kennethkennettmcrypt_create_iv()outputs ISO-8859-1. – Kennethkennett$algorithm = 'blowfish'and$mode = 'cbc', class should handle it but I don't think this would still sort out your particular issue. As you said, it would only work if you started using whole thing at very beginning in a certain manner which unfortunately doesn't really apply to you. It sounds like you might end up with a working solution where a bit of patchy and hacky code is involved. – Zeigler