My question is about how to properly set the package name and SHA-1 certificate fingerprint in the Google Developers Console in order to restrict usage of my Android API key to my app.
When I don't have anything set in the "Restrict usage to your Android apps" section, my requests to the Google Translate API work properly. The API responds normally with status code 200 and my expected result.
But when I specify a package name and SHA-1 certificate fingerprint for my app using the Developers Console, I consistently get 403 Forbidden responses like the following:
HTTP/1.1 403 Forbidden
Vary: Origin
Vary: X-Origin
Content-Type: application/json; charset=UTF-8
Date: Sun, 29 Nov 2015 21:01:39 GMT
Expires: Sun, 29 Nov 2015 21:01:39 GMT
Cache-Control: private, max-age=0
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
X-XSS-Protection: 1; mode=block
Server: GSE
Alternate-Protocol: 443:quic,p=1
Alt-Svc: quic=":443"; ma=604800; v="30,29,28,27,26,25"
Content-Length: 729
{
"error": {
"errors": [
{
"domain": "usageLimits",
"reason": "ipRefererBlocked",
"message": "There is a per-IP or per-Referer restriction configured on your API key and the request does not match these restrictions. Please use the Google Developers Console to update your API key configuration if request from this IP or referer should be allowed.",
"extendedHelp": "https://console.developers.google.com"
}
],
"code": 403,
"message": "There is a per-IP or per-Referer restriction configured on your API key and the request does not match these restrictions. Please use the Google Developers Console to update your API key configuration if request from this IP or referer should be allowed."
}
}
The request looks like the following. Notice that there's no referer header in the request:
GET https://www.googleapis.com/language/translate/v2?key=XXXXXXXXXXXXXXXXXXXXXXXX-XXXXXXXXXXXXXX&source=en&target=es&q=test HTTP/1.1
User-Agent: Dalvik/2.1.0 (Linux; U; Android 5.1.1; Nexus 6 Build/LVY48H)
Host: www.googleapis.com
Connection: Keep-Alive
Accept-Encoding: gzip
I'm assuming that the error message indicates a package name or SHA-1 fingerprint problem, despite its message about a "per-IP or per-Referer restriction". While browser keys allow the setting of a per-referer restriction, I'm using an Android key with nowhere to set a per-IP or per-Referer restriction.
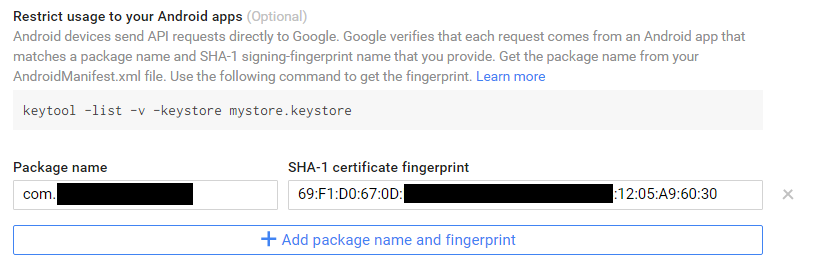
I'm sure I have entered the package name correctly in the Google Developers Console. I'm reading the package name from the package attribute on the manifest tag in my Android manifest file.
I'm also sure I have the SHA-1 fingerprint set correctly in the Google Developers Console. I'm reading this value from my keystore using the command keytool -list -v -keystore /path/to/my/keystore. I get the same value when I read it from the APK file using keytool -list -printcert -jarfile myAppName.apk. I'm installing that same APK file using adb.
Here's what I see in the Developers Console:
I've tested this on multiple devices running stock Android. I get the error response on wifi and on the cell network, whether I'm proxying the traffic or not.
When I remove the restriction from the Developers Console, the app works properly again.
What am I doing wrong here?
Note: Several similar questions have been asked before, but with no adequate answers. I don't want to use a browser key or remove the restriction altogether. I want to get the usage restriction to work properly.

GoogleAuthUtil, which will generate a token for the specific user and package/fingerprint. However, that requiresGET_ACCOUNTSpermission, which smart users are weary of. You could also use the AccountManager'sgetAuthToken()method, but that would require not only theGET_ACCOUNTSpermission, but alsoUSE_CREDENTIALS. You might be best of using an API key and obscuring it a bit. – Erhard