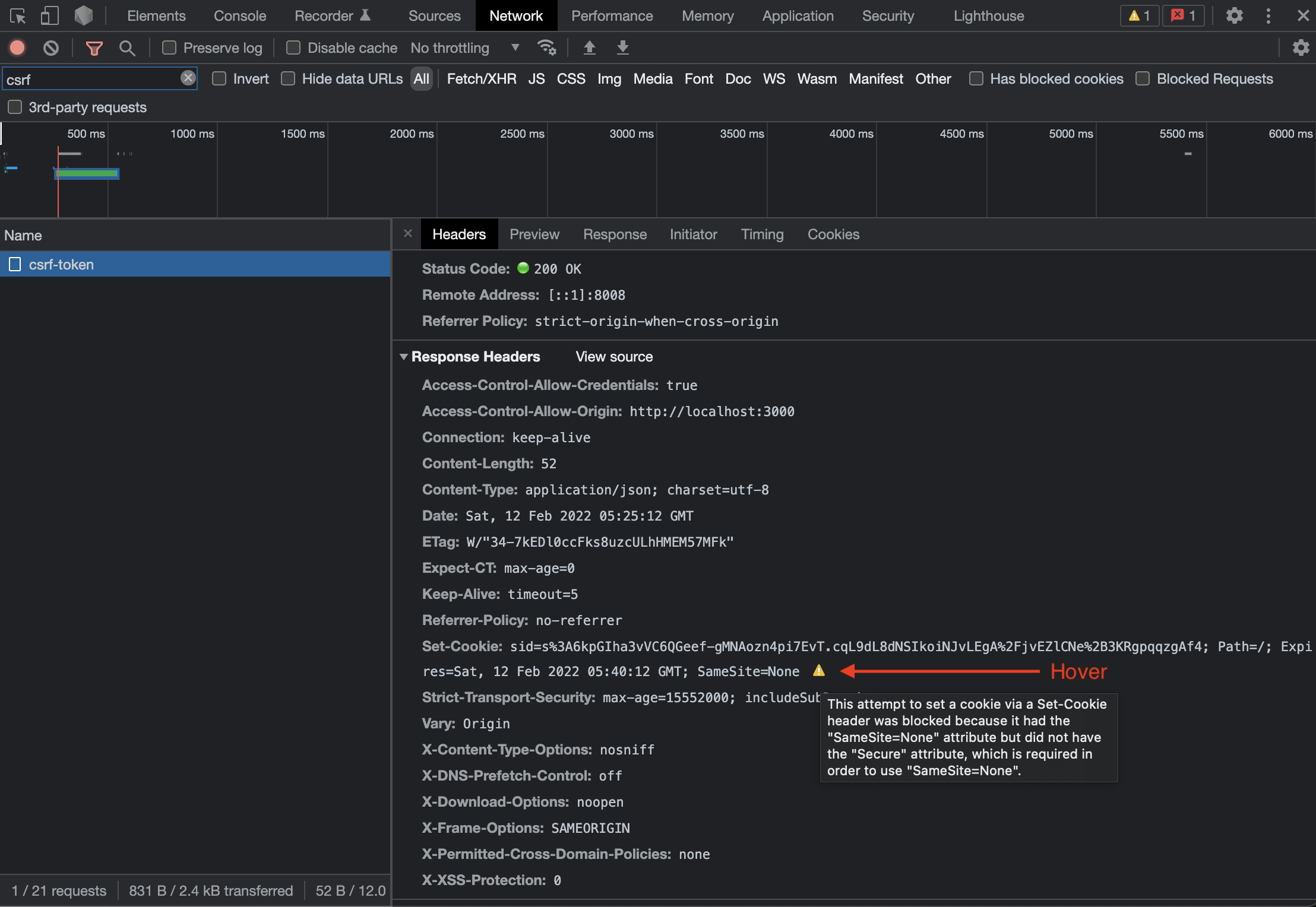
I'm using chrome and I'm wondering if there is either an extension or a method to tell why a cookie is not being sent.
I have one request I'm making to http://dev/login and it's returning,
Set-Cookie:DevId=cffbc7e688864b6811f676e181bc29e6; domain=dev; path=/; expires=Tue, 16-Jun-2015 21:27:43 GMT
However, on a post to http://dev/Base/User/home/ I'm not sending the DevId cookie. I'd love to know why the cookie isn't being sent if anyone happens to know. But, moreover, I'd love to know how I can tell why and how to better debug this problem in the future.
Here are some requests, as captured from Chrome's Dev tools
So here is my response from /login (notice Set-Cookie header),
HTTP/1.1 200 OK
Date: Tue, 16 Jun 2015 19:57:43 GMT
Server: Apache
Pragma: no-cache
Cache-control: no-cache, max-age=0
Set-Cookie: DevId=cffbc7e688864b6811f676e181bc29e6; domain=dev; path=/; expires=Tue, 16-Jun-2015 21:27:43 GMT
Cache-Control: max-age=0
Expires: Tue, 16 Jun 2015 19:57:43 GMT
Keep-Alive: timeout=10, max=10
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: application/json; charset=ISO-8859-1
And here is my post to /Base/User/home/1 (notice no cookie),
POST /Base/User/home/ HTTP/1.1
Host: dev
Connection: keep-alive
Content-Length: 0
Origin: http://dev
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Ubuntu Chromium/43.0.2357.81 Chrome/43.0.2357.81 Safari/537.36
Content-type: application/x-www-form-urlencoded; charset=UTF-8
Accept: text/javascript, text/html, application/xml, text/xml, */*
X-Prototype-Version: 1.7.2
X-Requested-With: XMLHttpRequest
Referer: http://dev/user/1/home
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.8