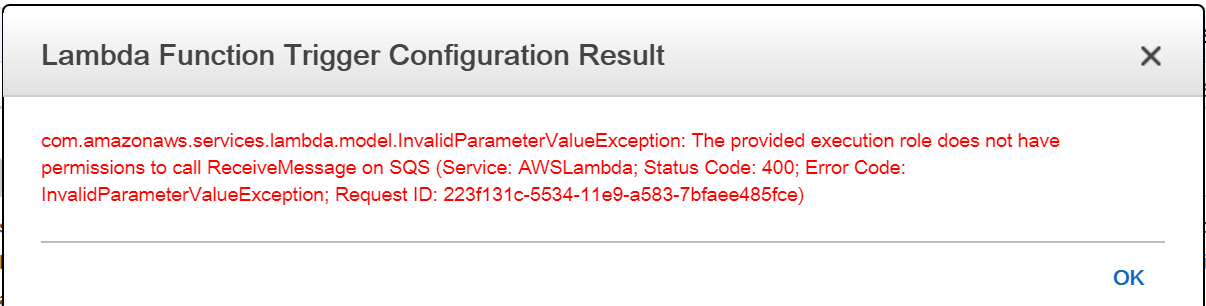
I have a SQS queue and I want to trigger a lambda function when a message arrives in the queue. I have written the lambda function and that works successfully when I click the "Test" button. When I go to SQS and try to configure it as a lambda trigger I see the error message below.
I have created the SQS queue and lambda function using the same user and role and the lambda function has execute permissions against the same role.
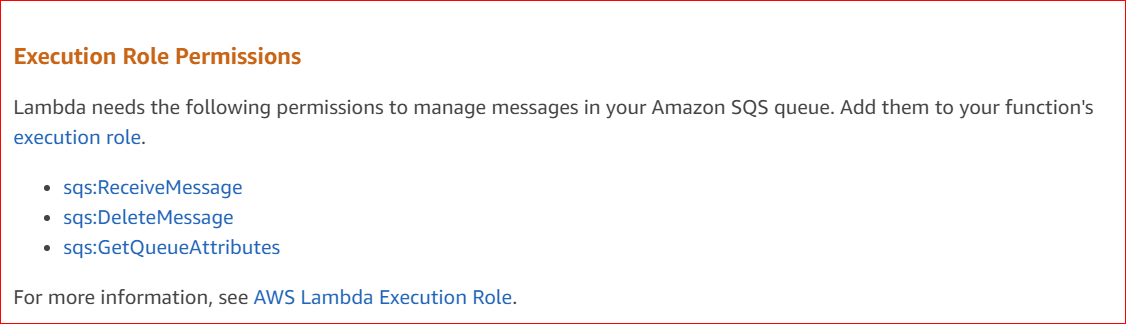
I also have also added SQS receiveMessage permission but it doesn't seem to make a difference unless I'm doing something wrong when I set it.
What could be causing the problem?
Thanks for any help