I've spent a lot of time trying to find a way to limit the access for web services secured by Keycloak based on user groups or roles. The closest I got for the solution was to implement a custom authenticator script which performs a user attribute check, however that solution comes with a big disadvantage: you lose the SSO function.
I used the below Authenticator script:
AuthenticationFlowError = Java.type("org.keycloak.authentication.AuthenticationFlowError");
function authenticate(context) {
var allowed_groups = ['foo', 'bar'];
var username = user ? user.username : "anonymous";
var groups = user.getGroups();
var group_array = groups.toArray();
for (var i in group_array) {
var gn = group_array[i].getName();
if (allowed_groups.indexOf(gn) >= 0) {
LOG.info("Access granted for user '" + username + "' for being member of LDAP group '" + gn + "'");
return context.success();
}
}
LOG.info("Access denied for user '" + username + ". for not being member of any of the following LDAP groups: " + allowed_groups);
context.failure(AuthenticationFlowError.IDENTITY_PROVIDER_DISABLED, context.form().setError(
"User doesn't have the required LDAP group membership to view this page", null).createForm("error.ftl"));
return;
}
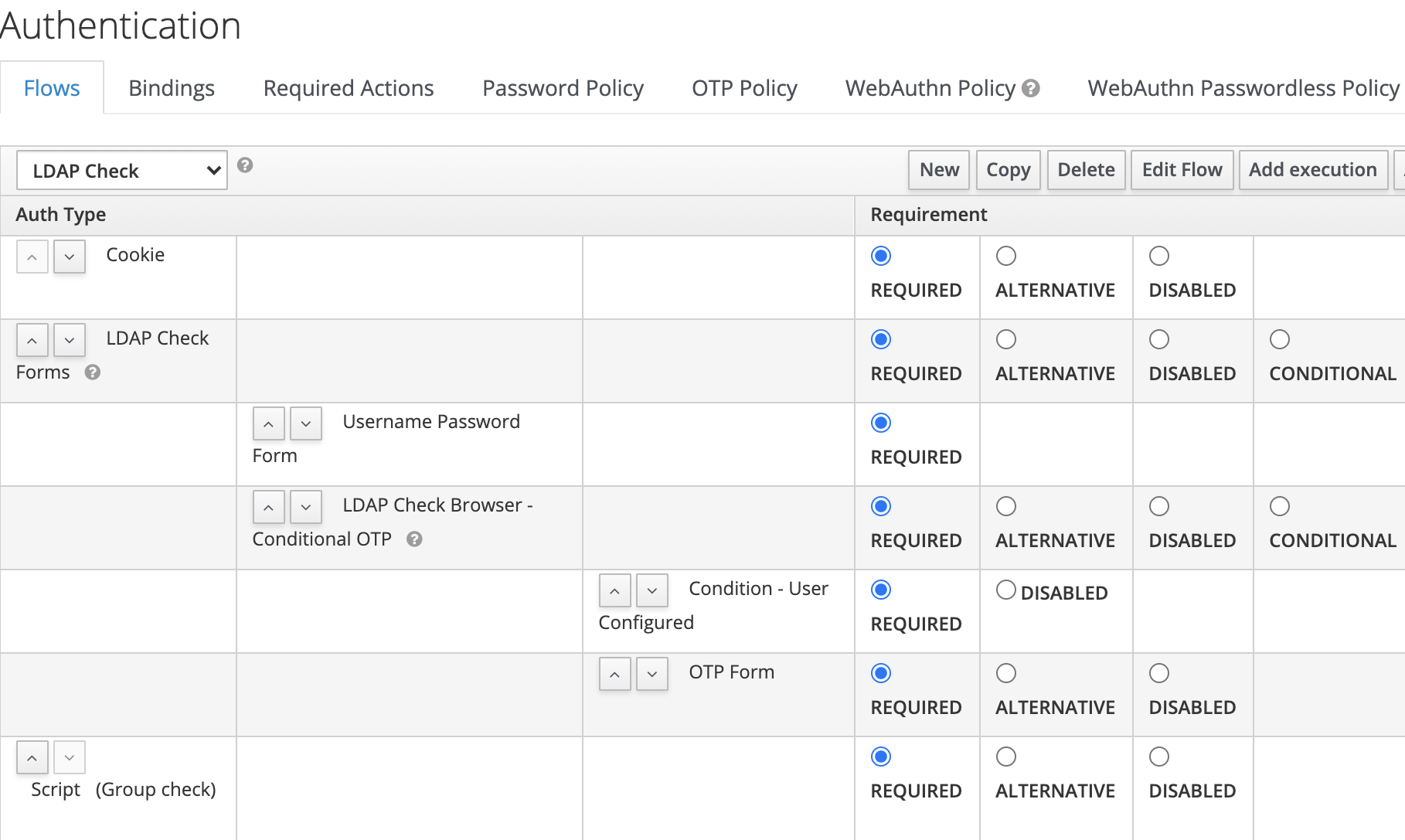
Screenshot from the authentication flow:
Unfortunately the user object within the custom authenticator script only gets populated when the "Username Password Form" auth section is passed, otherwise the user object is null therefore you can't check user attributes such as group or role. This means the user must type their credentials every time for every clients (web services) he intends to access via Keycloak. Unfortunately not having the SSO function is not an option for us as we are running more than 10 web services.
Is there any way to achieve user attribute based client access limitation by Keycloak while still having SSO? I wonder can the user information be somehow retrieved after the "Cookie" auth section passed? I am using Keycloak version 11.0.2