TL/DR: If you are creating a custom role:
empty collection name means "all". Do not use the '*' wild card
check if your database & collection names are correct. Cloud Atlas won't validate the information you provide and maybe the issue is just a typo
Context - 2024 Answer
This response is for those trying to limit their account rights and follow the Least Privilege Access Policy.
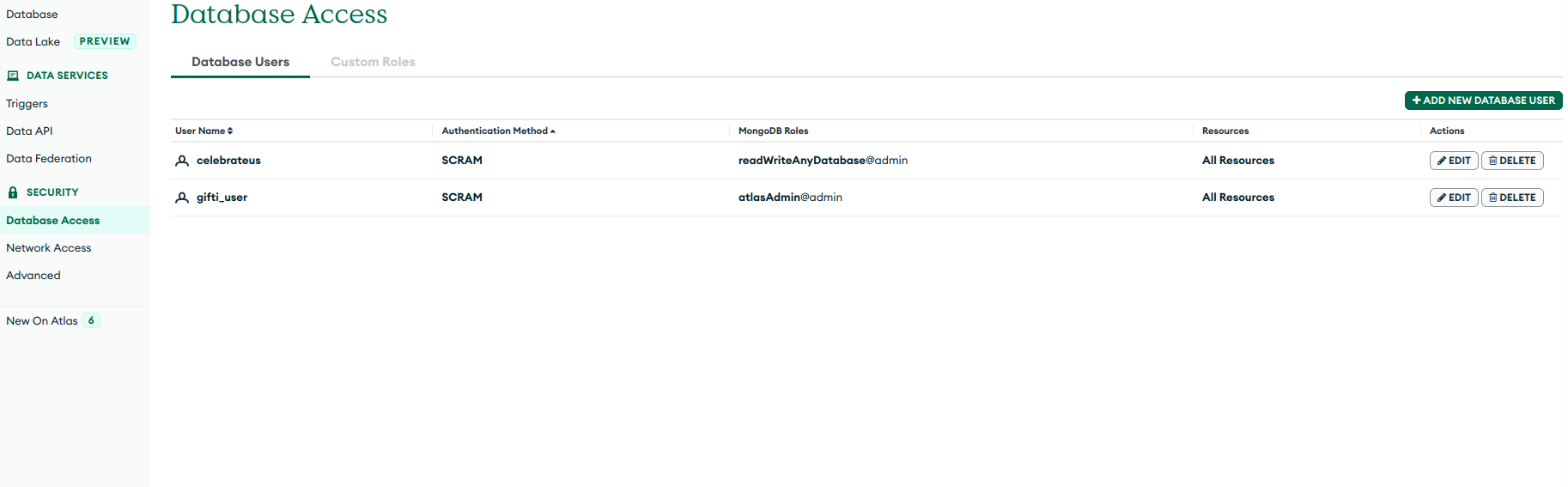
Long Story, Short: readWriteAnyDatabase@admin is too powerful and a security breach. Give only the necessary rights if you want to go safe.
How to do it (Atlas/Services/Security):
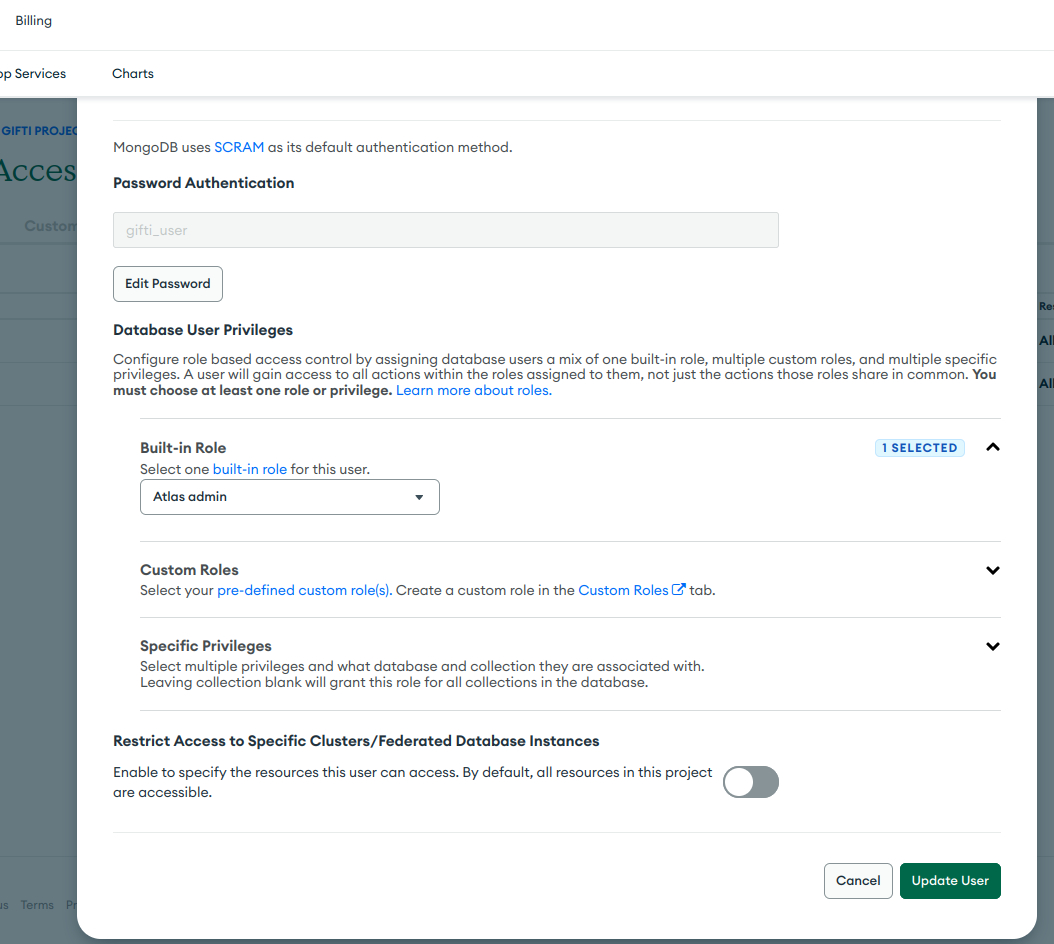
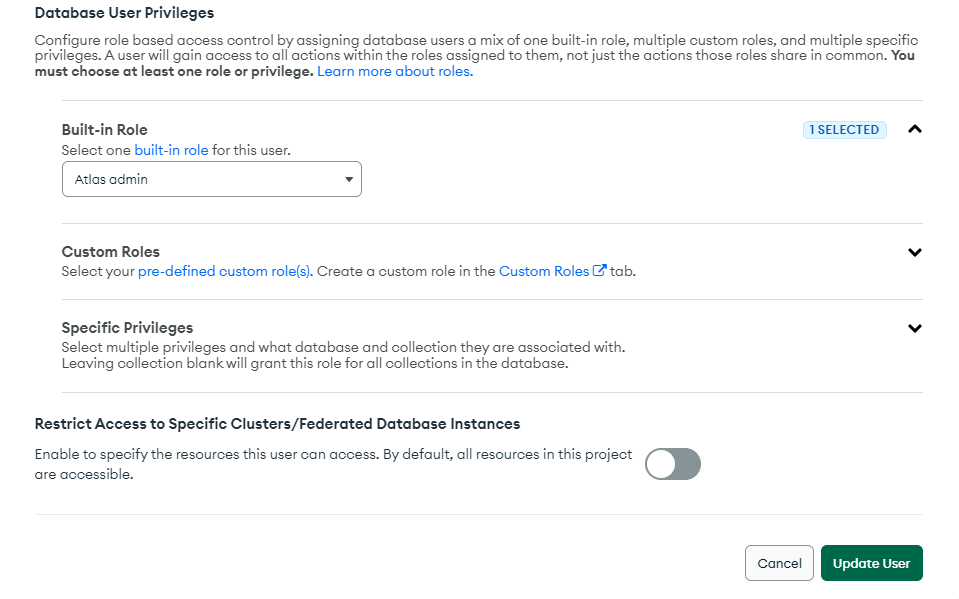
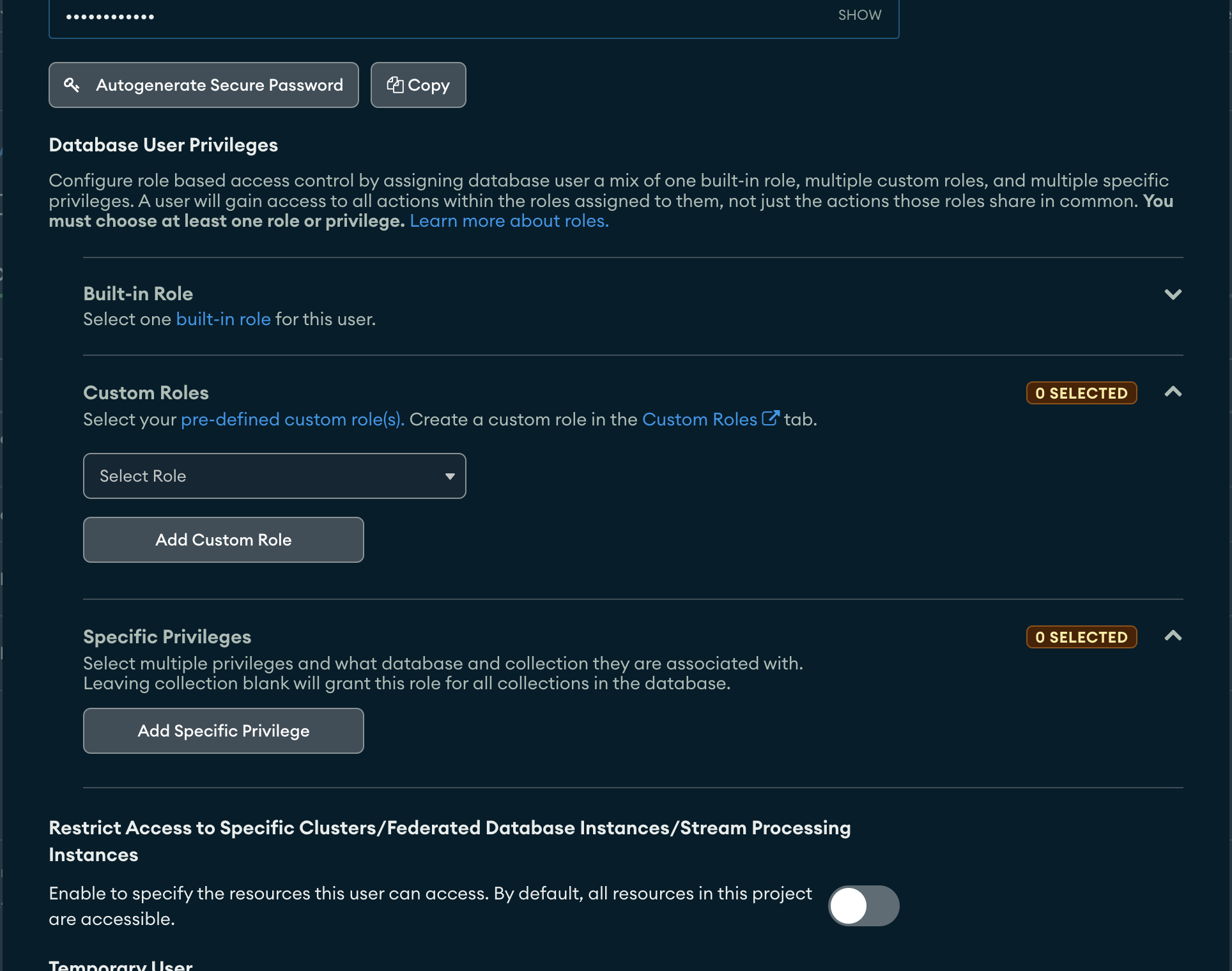
- When creating/updating MongoDB users, you have three types of Database User Privileges:
Built-in Role: Atlas Admin, ReadWriteAnyDatabase, ReadAnyDatabase - Easiest Step, but the "any database" should scare us all
Custom Role: I recommend this one because it's scalable as you can use roles with other accounts
Specific Privilege: it's the same as before, but cannot be replicated to other users
Step by Step
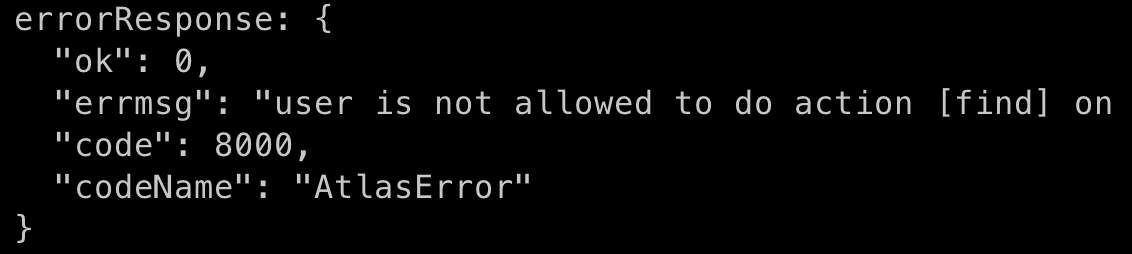
The error we are addressing is: user is not allowed to do action [find] on [a_database.my_collection].
![error]()
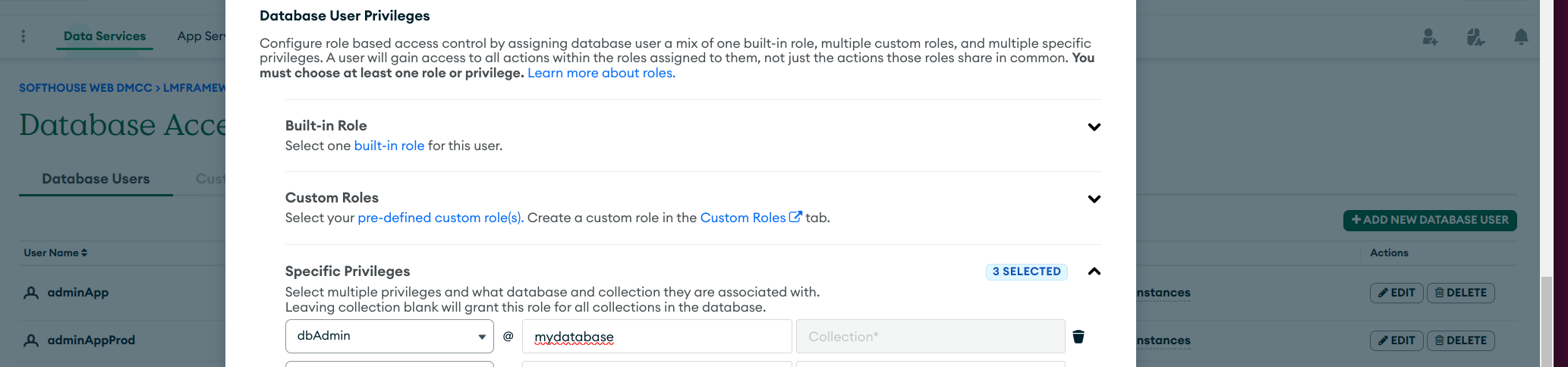
We start from Atlas/Services/Security, adding/editing a user:
![edit or create a user using Cloud Atlas]()
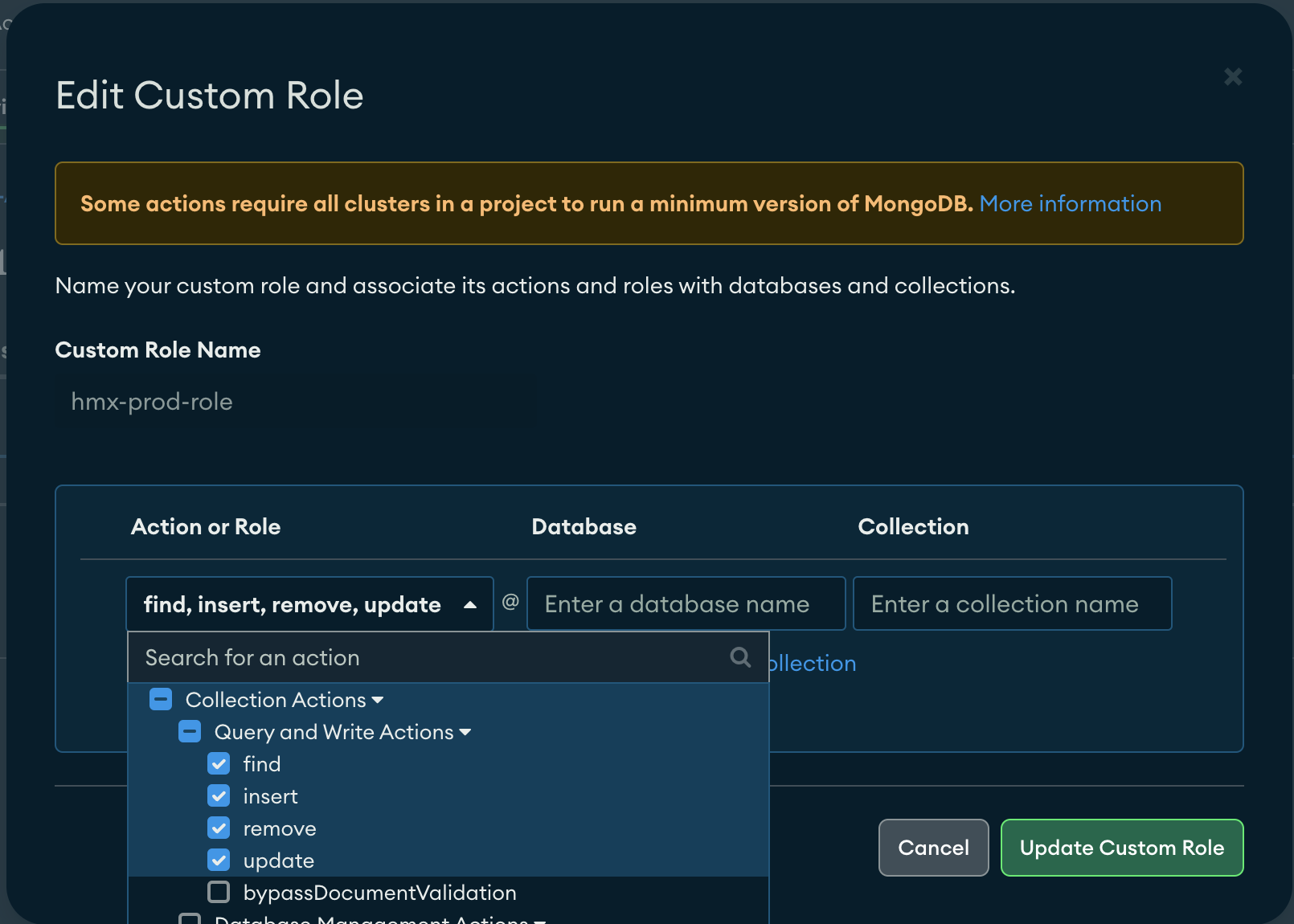
Solution: We will create a new role for a database named a_database and we will check the strategies for the Collection Name. Select only the rights the user will need usually: find, insert, remove, update.
![least privilege policy]()
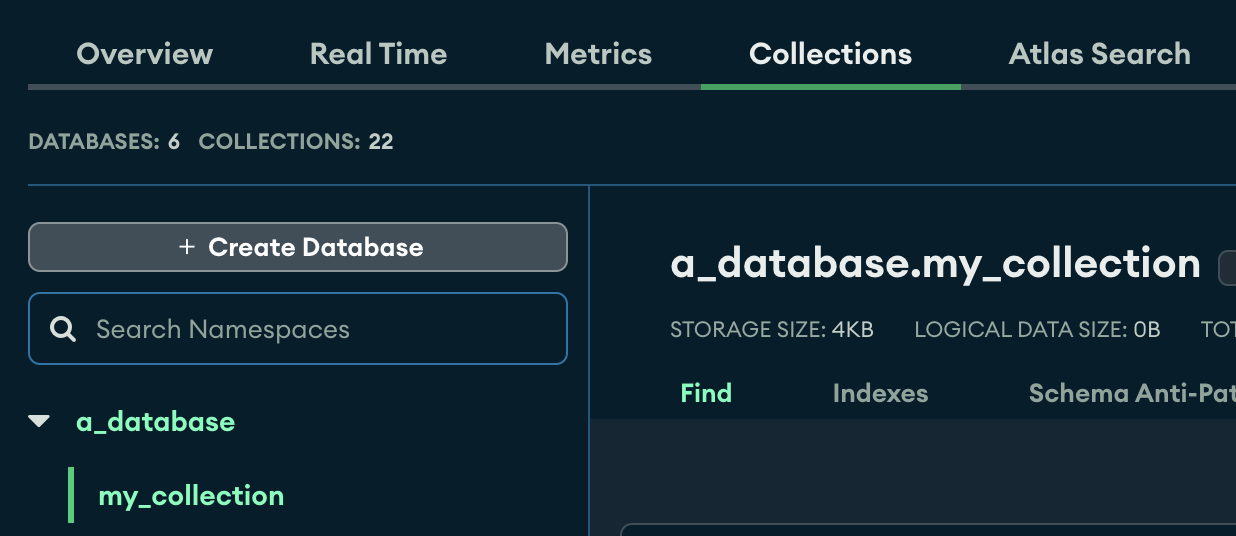
Database Name: A bit confusing, because it's the ones listed under collections in the Cloud Atlas.
![database]()
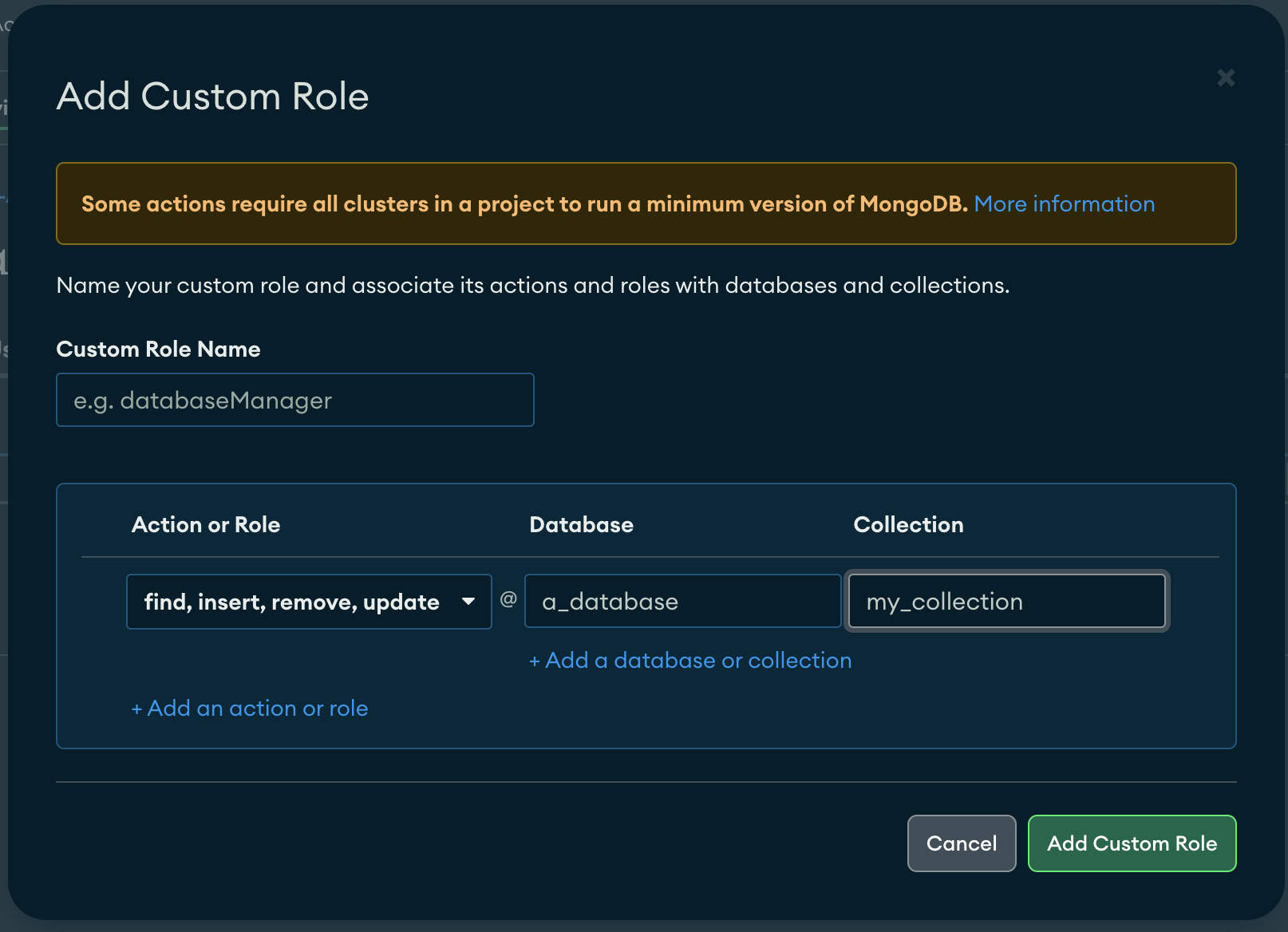
Custom Role is Ready:
![custom role]()
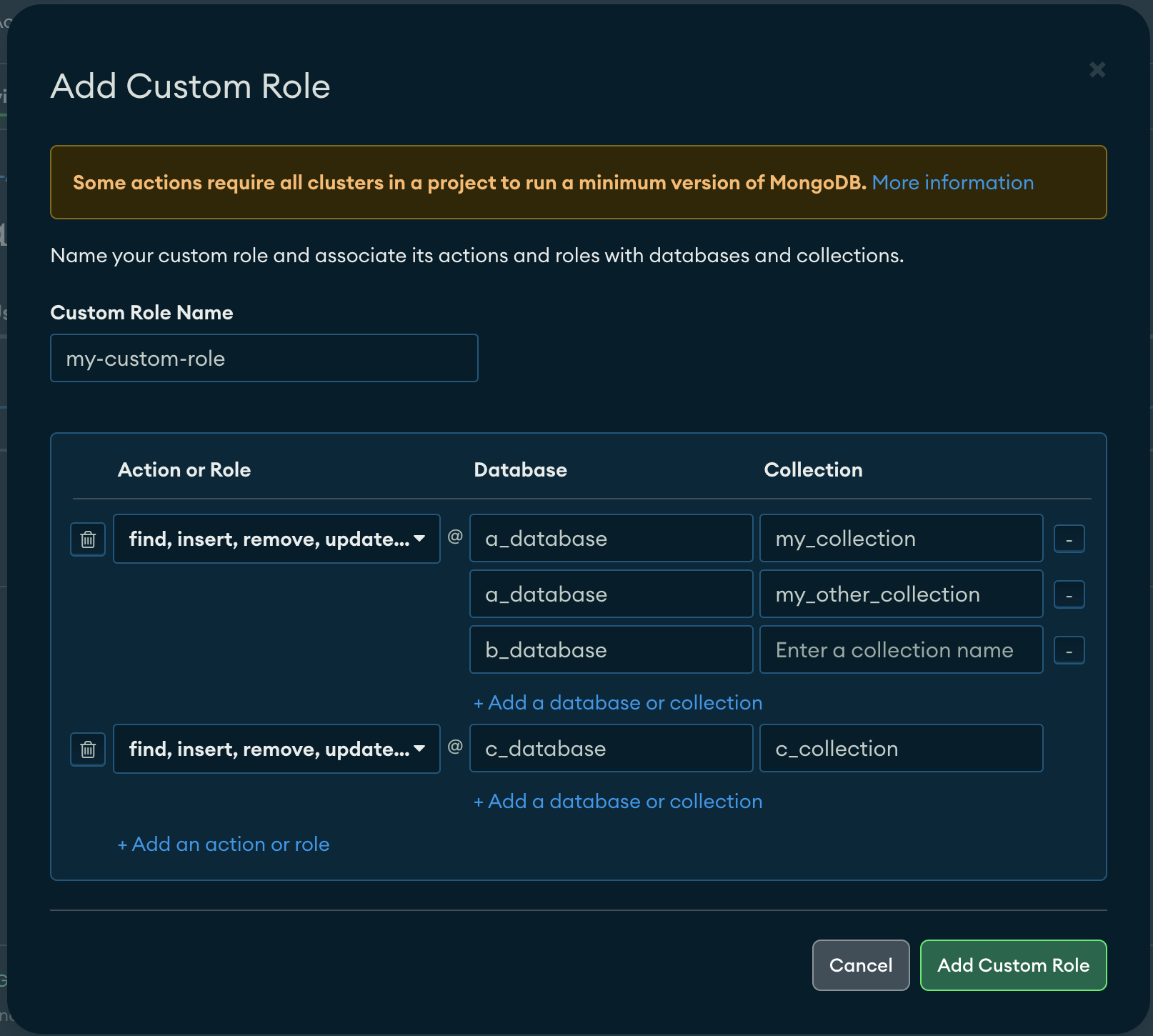
Important: If you have many collections, leave it empty instead of using the wildcard * in the collection name. If you want to restrict access, you must create multiple actions representing each of the collections.
Some Examples of How to Use this. See that we are referencing two different collections of the same "a_database" and we left b_database empty, to represent all the collections. Be careful with the names there, Atlas won't validate and this might be the cause of your error.
![custom roles examples]()
References:
Least Privilege Access Policy
Mongo DB Roles