Here is the context:
- I set up a resource in the API gateway. /user/company
- This resource have 2 methods. Get and POST.
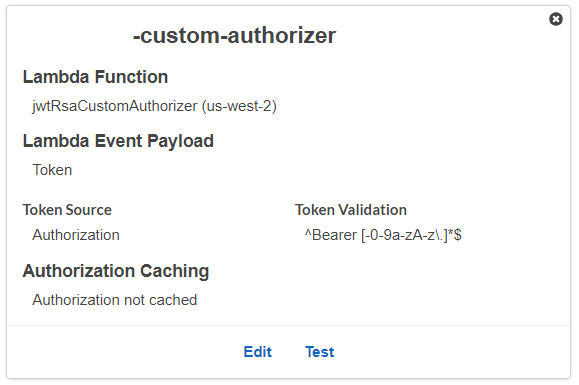
- I have configured a custom Authorizer for this resource.
The problem:
- I can call the GET method by sending right authorization information and I get the results as expected.
- I try to send a POST request and I get the following error:
{
"message": "User is not authorized to access this resource"
}- If I wait for few minutes, then call the POST method, it will work.
- If after calling the POST method and getting the results I call GET method, it will show the same error as mentioned above.
In addition, I have disabled cache for the authorizer.
What might have caused this issue?