When trying to access the Graph Service Client using I am receiving the error:
Code: Authorization_RequestDenied
Message: Insufficient privileges to complete the operation.
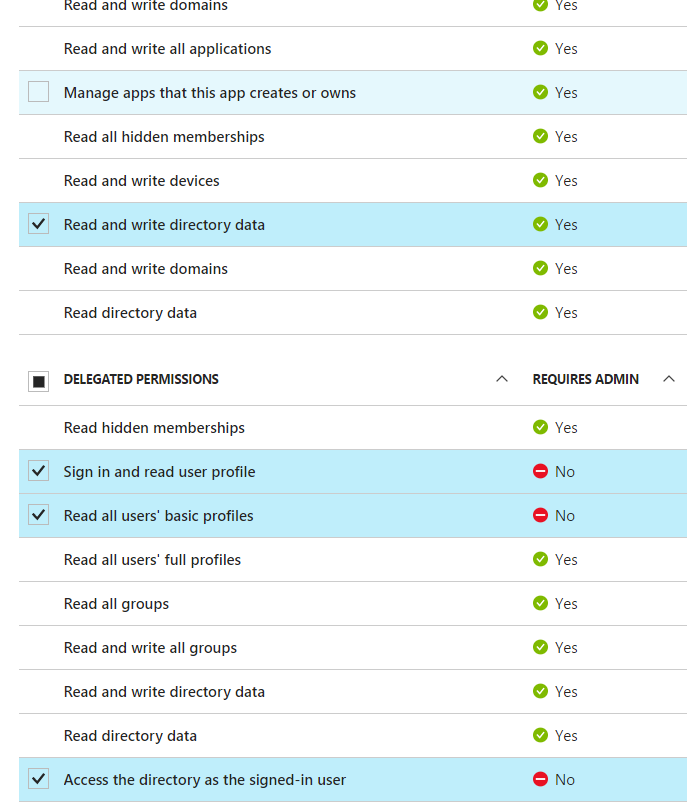
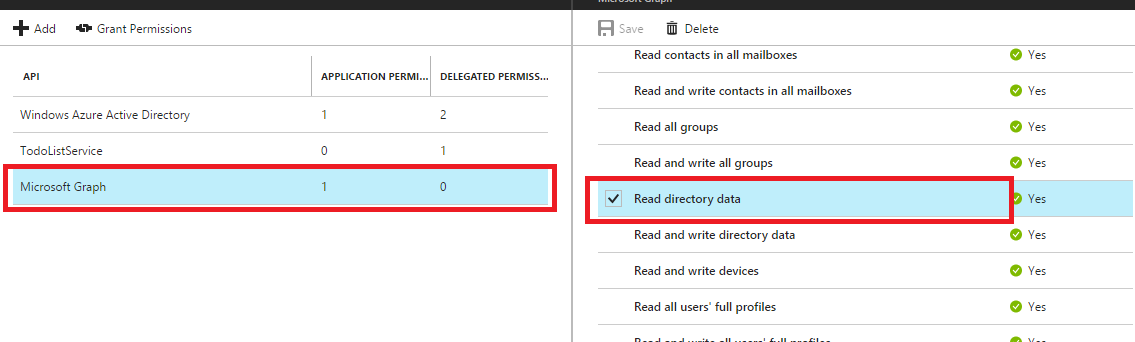
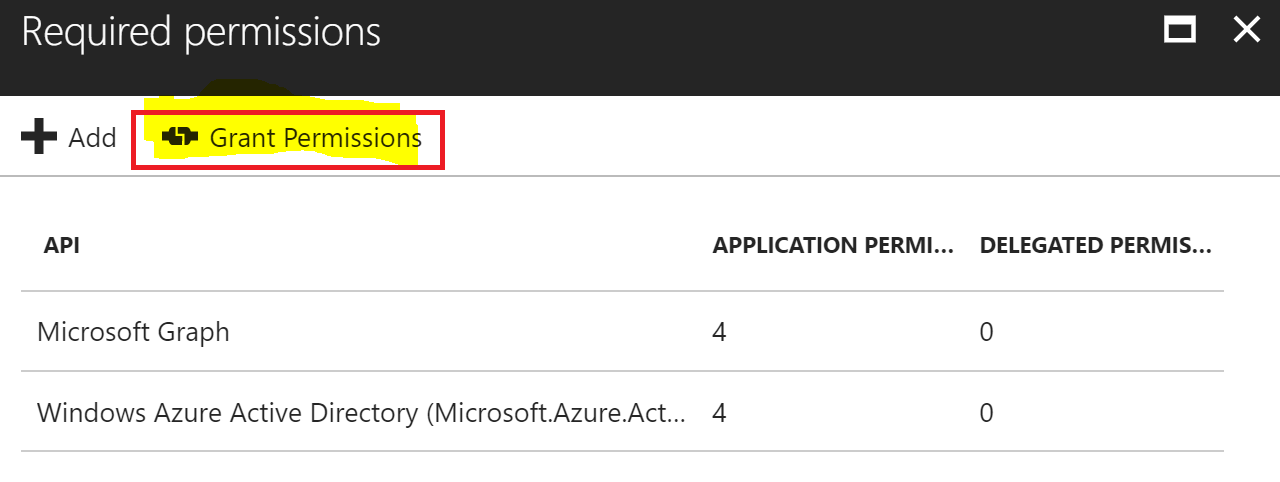
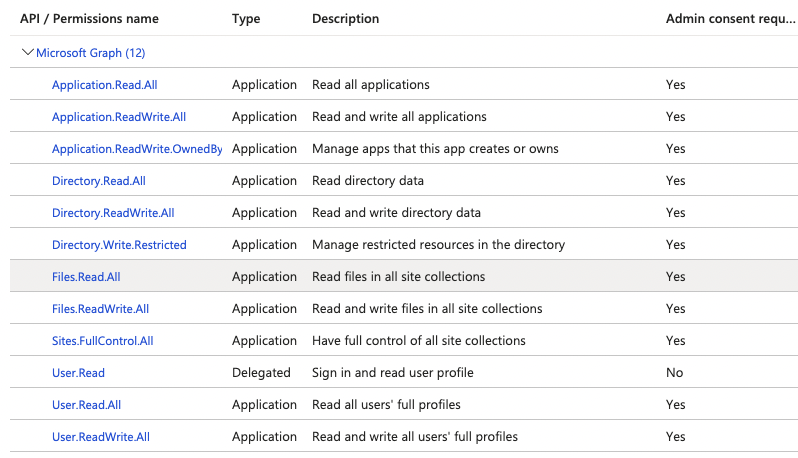
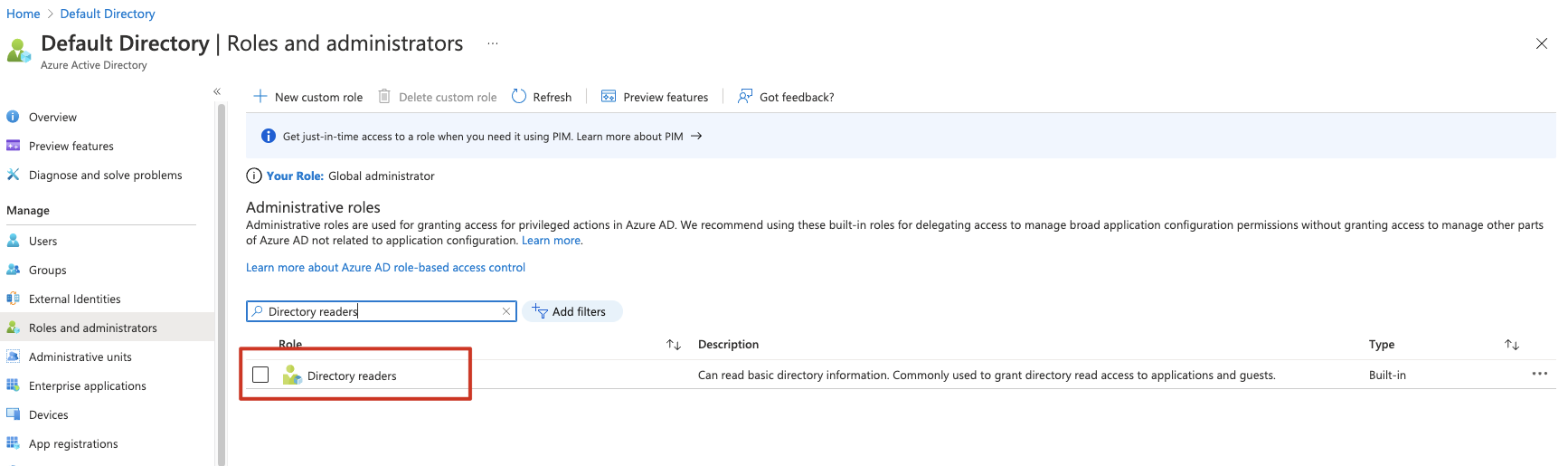
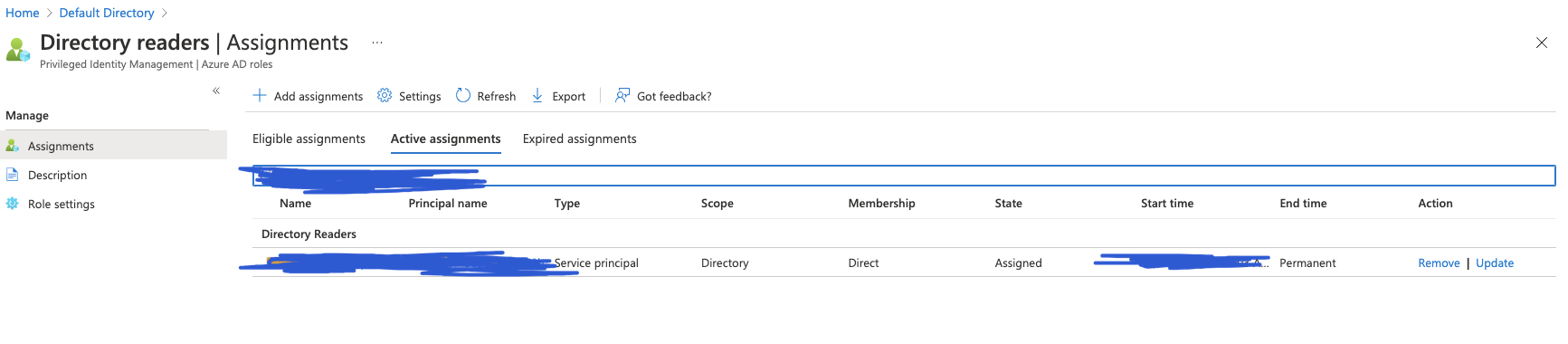
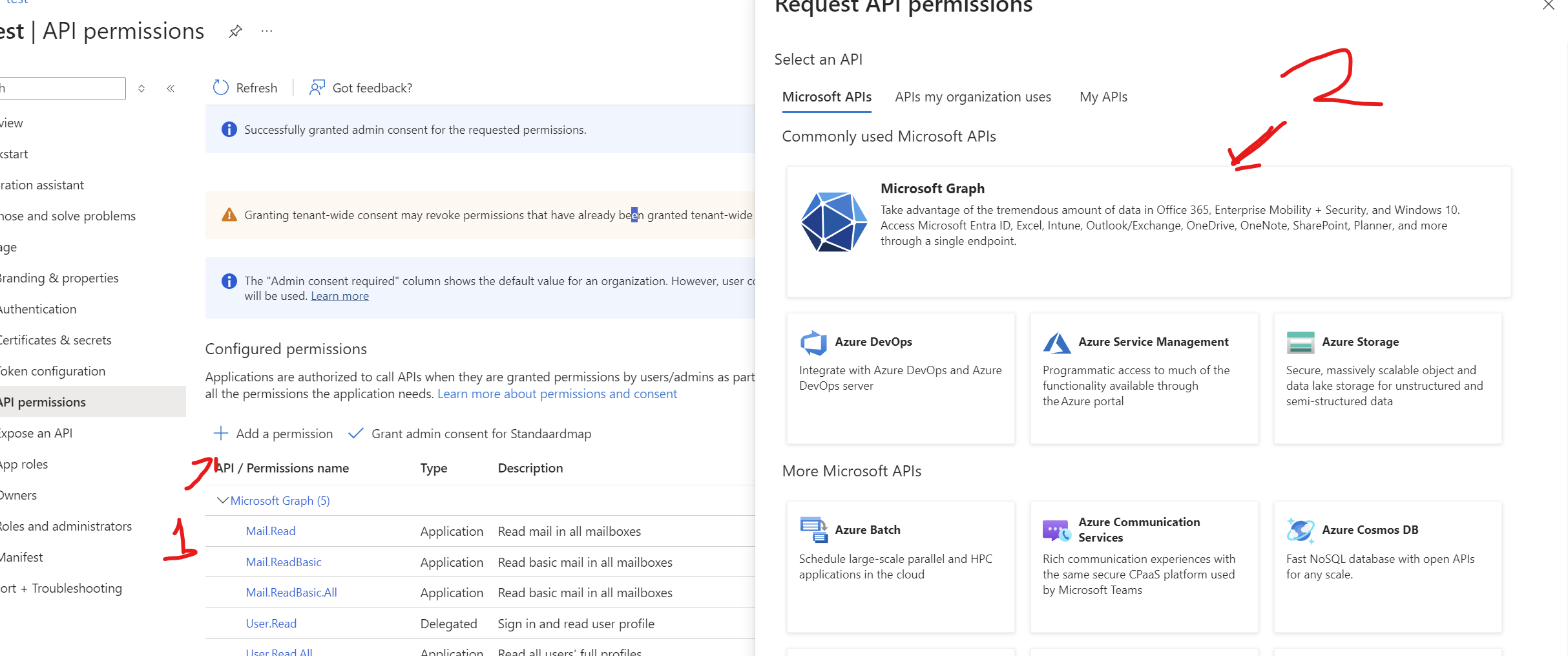
After researching this error the most common solution was to set the permissions for the API. This had already been done and has permissions to read basic/full profiles.
I've delete and re-added the APIs.
Below is the code in my AzureAuthenticationProvider class which inherits from IAuthenticationProvider:
public class AzureAuthenticationProvider : IAuthenticationProvider
{
private string _azureDomain = "myDevDom.onmicrosoft.com";
public async Task AuthenticateRequestAsync(HttpRequestMessage request)
{
try
{
string clientId = "2b823c67-1b0d-4a10-a9e1-737142516f5q";
string clientSecret = "xxxxxx";
AuthenticationContext authContext = new AuthenticationContext("https://login.windows.net/" + _azureDomain + "/oauth2/token");
ClientCredential credentials = new ClientCredential(clientId, clientSecret);
AuthenticationResult authResult = await authContext.AcquireTokenAsync("https://graph.microsoft.com/", credentials);
request.Headers.Add("Authorization", "Bearer " + authResult.AccessToken);
}
catch (Exception ex)
{
}
}
}
I've tried changing the client secret to an invalid Id and it threw an error, so the client key is correct. I've also tried to verify that the access token is valid by altering the access token, this also returns a error.
The above code seems to work fine.
Below is the code where I'm trying to access Azure AD:
public async Task<IGraphServiceUsersCollectionPage> GetUsersByLastName(string lastname)
{
GraphServiceClient graphClient = new GraphServiceClient(new AzureAuthenticationProvider());
string filter = String.Format("startswith(surname, '{0}')", lastname);
IGraphServiceUsersCollectionPage users = await graphClient.Users.Request().Filter(filter).GetAsync(); //Fails on this line
return users;
}