I'm really new to Azure but trying to learn - so apologies if this is a daft question. I've started the free trial (which gives me some credit to start with), and I'm trying to create a key vault. If I specify "Vault access policy" under access policies, it works great and I'm able to create secrets. I'd like to use "Azure role-based access control" though instead. If I create a key vault using Azure role-based access control, I get a message when trying to create a new secret which says "The operation is not allowed by RBAC. If role assignments were recently changed, please wait several minutes for role assignments to become effective." I am logged into Azure as the Service Administrator, so I don't think it's a permissions issue. I have left it overnight, and it still displays the message, so I don't think it's a matter of not waiting long enough for role assignments to become effective. I have tried creating the key vault in different regions and get the same results. Note that this is happening when I create a key vault using Azure role-based access control from scratch (i.e. I am not changing it from one to the other or anything like that.) Does anyone know what I'm doing wrong? Thanks for any help Andrew
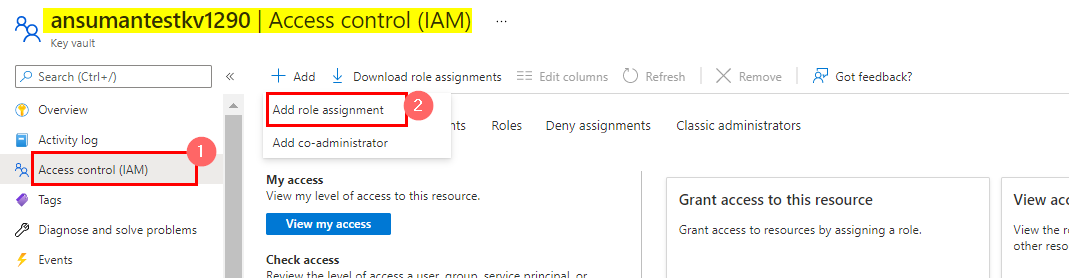
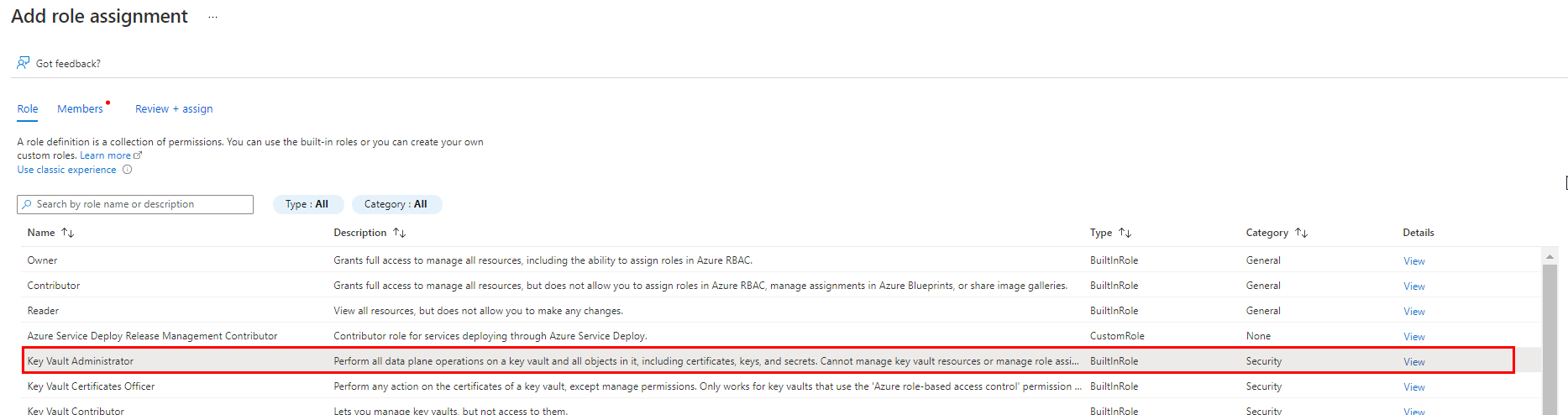
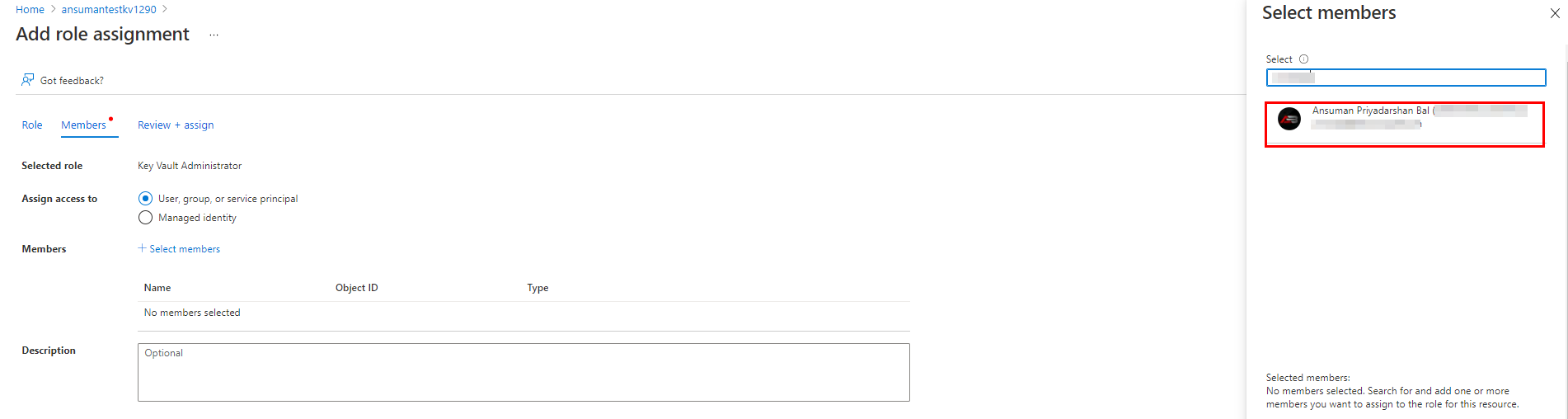
If you are creating the Key vault with RBAC role from scratch then Please assign Key vault Administrator to your name for creating/ managing the secrets, certificates and keys.
Steps:
If you provide access to Key Vault keys, certificates, and secrets with an Azure role-based access control, then you need to use a specific built-in role or a custom one with allowed operations on the Data plane.
You have the list of those aforementioned built-in roles in the official documentation for Key Vault RBAC permission model.
The role you have assigned most probably do not have access to Key Vault Data plane. You can find the whole list of operation providers at this link. See that there is a distinction between Actions which are actions at infrastructure level vs DataActions which are actions at the data level, what is inside your Key Vault. Most of roles do not have access to this.
© 2022 - 2024 — McMap. All rights reserved.